When you sign up for a new Microsoft 365 tenant, a default password policy is already in place that Microsoft considers optimal. It helps secure your users’ accounts by forcing a set of rules for creating or updating their passwords.
But can you configure these password policies? Yes, but not all. There’s a small subset of customizable password policy settings, but the majority are not.
Table of Contents
The Default Password Policy in Microsoft 365
The following are the default password policy settings for users created and managed directly in the cloud.
Non-Customizable Password Policy Settings
Below are the non-configurable Microsoft 365 password policy settings.
- Allowed characters:
- A – Z
- a – z
- 0 – 9
- @ # $ % ^ & * – _ ! + = [ ] { } | : ’ , . ? / ` ~ ” ( ) ; < >
- Blank space
- Disallowed characters:
- Unicode characters (e.g., ℗, β)
- Complexity:
- The password length is between 8 to 256 characters.
- The password must contain three out of the four character types: lowercase, uppercase, numbers, and symbols.
- Password reuse:
- The last password cannot be reused when the user changes or resets a password.
Customizable Password Policy Settings
Below are the Microsoft 365 password policy settings you can configure and customize.
- Password expiration policy (maximum password age):
- For tenants created after 2021, there is no default maximum password age. Meaning that passwords do not expire by default.
- Otherwise, the default maximum password age was 90 days.
- Custom smart account lockout:
- The user account is locked out after ten unsuccessful login attempts.
- The initial user account lockout duration is 60 seconds, increasing if the account gets locked out repeatedly.
- Custom banned passwords list:
- Disabled by default.
Enabling the Microsoft 365 Password Policy for On-Premises AD Users
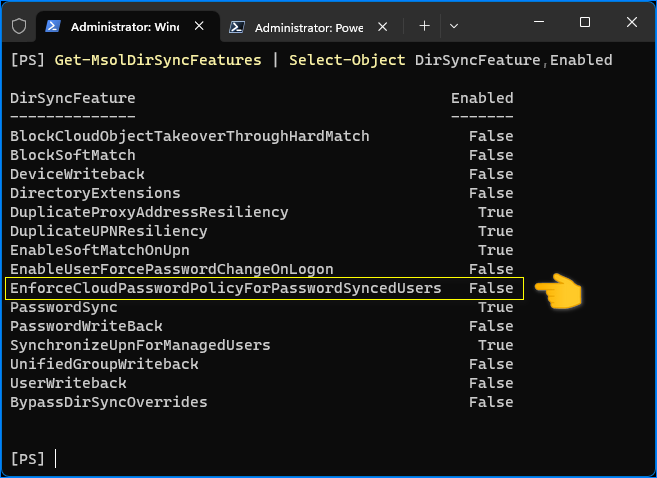
The Microsoft 365 password policy only applies to cloud-only user accounts by default. The EnforceCloudPasswordPolicyForPasswordSyncedUsers identity synchronization feature controls this behavior.
Note. These commands require the MSOnline V1 PowerShell module for Azure Active Directory.
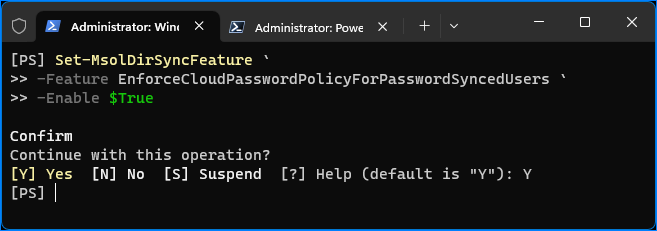
To apply the Microsoft 365 password policy to synchronized on-premises AD accounts, enable the EnforceCloudPasswordPolicyForPasswordSyncedUsers feature by running this command in PowerShell.
Set-MsolDirSyncFeature -Feature EnforceCloudPasswordPolicyForPasswordSyncedUsers -Enable $True
Configuring the Microsoft 365 Password Expiration Policy
The global password expiration policy configuration has two states: Passwords never expire, and password expires in days. You can configure these settings in the GUI or PowerShell.
Related. Configuring Domain Password Expiration Group Policy.
Using the Microsoft 365 Admin Center
Configuring the password expiration policy using the admin center will enforce it to all domains in your Microsoft 365 tenants. Meaning that if you have multiple verified domains, the same password expiration policy will be assigned to those domains.
- Log in to the Microsoft 365 admin center.
- Navigate to Setting → Org settings → Security & privacy and click the Password expiration policy link.
- On the flyout page that appears, select whether never to expire passwords or manually set the days when the passwords expire. In this example, I’m choosing to expire individual user passwords every 120 days.
- You’ll see the confirmation message once you save the password expiration policy, as shown below. You can now close the Password expiration policy flyout page.
Using the Microsoft Graph PowerShell
You can customize the password expiration policy for each domain in your organization using the Microsoft Graph PowerShell. This method requires the Microsoft Graph PowerShell module. If you don’t have it, refer to the Install the Microsoft Graph PowerShell SDK.
- Open PowerShell and connect to Microsoft Graph API with the Domain.ReadWrite.All permission scope:
Connect-MgGraph -Scopes Domain.ReadWrite.All
- Next, by running this command, let’s find out the password expiration policy for each domain.
Get-MgDomain | Format-Table Id,IsDefault,PasswordValidityPeriodInDays
As you can see in this example, all domains’ PasswordValidityPeriodInDays value is 120, meaning the passwords for the users under these domains are valid for 120 days.
- Suppose I want to set the password expiration policy never to expire; the command to run is this:
Update-MgDomain -DomainId lazyexchangeadmin.cyou -PasswordValidityPeriodInDays 2147483647
The value of 2147483647 for the PasswordValidityPeriodInDays means never to expire the password.
Related. How to Send Office 365 Password Expiration Notification.
Configuring the Azure AD Password Protection Policy
The Azure AD password protection policy is a directory setting rule with three categories: Custom smart lockout, Custom banned passwords, and Password protection for Windows Server Active Directory.
Related. How to Configure Account Lockout Policy in Active Directory?.
Follow these steps to configure these settings.
- Log in to Microsoft Entra.
- Navigate to Identity → Protection → Authentication methods.
- Click Password protection on the Authentication methods page. On this page, you’ll find the following configuration items.
| Type | Setting | Description |
|---|---|---|
| Custom smart lockout | Lockout threshold | Determines how many failed logins are allowed before the user account is locked out. |
| Lockout duration in seconds | The initial lockout duration. This value increases if the lockout happens consecutively. | |
| Custom banned passwords | Enforce custom list | Azure AD will check for bad passwords in the Custom banned password list if enabled. |
| Custom banned password list | The list of words to check for bad passwords. | |
| Password protection for Windows Server Active Directory | Enable password protection on Windows Server Active Directory | If enabled, the password protection policy is turned on for On-Premises AD user accounts.
This setting requires that the Azure AD Password Protection Proxy be installed on the on-premises domain controller for it to work. |
| Mode | If set to Enforced, synced users will be prevented from using banned passwords.
If set to Audit, synced users can use the banned passwords, and the attempt will be logged |
Conclusion
The Microsoft 365 password policy settings are essential security mechanisms to protect users’ passwords from possible compromise. Such settings include password expiration, smart account lockout, and a custom banned passwords list.
While the Microsoft 365 password policy helps with account security, it is only one of the security measures you can implement. Consider implementing password policies in your on-premises Active Directory and enable MFA for users to augment your organization’s identity security posture.