Usernames and passwords used to be the standard for account security until the advent of phishing and social engineering. Even experienced users still fall victim to password compromise leading to data loss, financial loss, and damaged reputation.
This is why the push for multifactor authentication (MFA) is stronger than ever. Many options exist for MFA, including biometrics, authenticator apps, hardware security keys, etc.
MFA is one of the crowning glories of cloud service providers today, including Azure Active Directory. And in this tutorial, we’ll explore how to enable/disable MFA in Azure Active Directory.
Table of Contents
Enable or Disable Per User MFA (Legacy) in the Azure AD Portal
Per-user MFA is the legacy method of implementing MFA. As the name implies, MFA status is changed per user. As you can imagine, this method can become challenging to manage as the user count increases.
Nevertheless, if this is the method used in your organization, here’s how you can manage it.
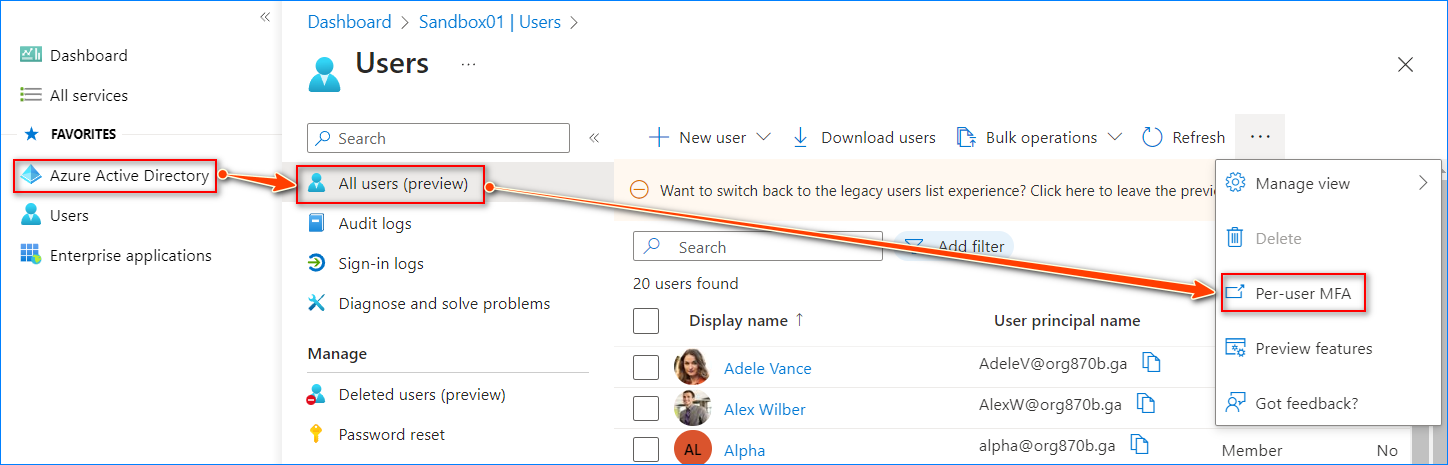
Log in to the Azure Active Directory admin center. Navigate to Azure Active Directory > All Users and click Per-user MFA.
On the multi-factor authentication page, you’ll see the list of users and their corresponding MFA status.
- Disabled — MFA is disabled for the user.
- Enabled — MFA is enabled for the user, but the user hasn’t completed the MFA registration yet.
- Enforced — MFA is enabled for the user who has completed the MFA registration.
Filter the list by selecting the Multi-Factor Auth Status. In this example, I’ll choose Enabled. Select the user or users and click the Disable link.
When prompted, click Yes to confirm the action.
Once the operation is completed, click Close.
Conversely, you can do the same steps with MFA-disabled users to enable them.
Enable or Disable Per User MFA (Legacy) in PowerShell
Managing the MFA status of multiple users is more efficient using PowerShell, which is possible through the Azure Active Directory PowerShell module. Here’s how to enable or disable the per-user MFA in PowerShell.
Related post. How to Disable Multi-Factor Authentication (MFA) in Office 365?
Connect to Azure AD PowerShell:
Import-Module MSOnline Connect-MsolService
Disable MFA for One User
To disable the MFA of one user, run the Set-MsolUser command, as shown below. Replace the “UPN” with the user’s user principal name.
Set-MsolUser -UserPrincipalName "UPN" -StrongAuthenticationRequirements @()
Disable MFA for All Users
To disable MFA for all users, run this command. The first command gets all users from Azure AD and pipes the result to the second command to disable per-user MFA.
Get-MsolUser -All | Set-MsolUser -StrongAuthenticationRequirements @()
Enable MFA for One User
To enable the per-user MFA for one user, create the StrongAuthenticationRequirement object first.
$mfaReq = [Microsoft.Online.Administration.StrongAuthenticationRequirement]@{
RelyingParty = "*"
State = "Enabled"
}
Next, run the following command to enable the user’s MFA.
Set-MsolUser -UserPrincipalName "AdeleV@org870b.ga" ` -StrongAuthenticationRequirements $mfaReq
Finally, confirm the user’s MFA state is enabled:
Get-MsolUser -UserPrincipalName "AdeleV@org870b.ga" | ` Select-Object -ExpandProperty StrongAuthenticationRequirements
Enable MFA for All Users
To enable the per-user MFA for all users, run the following code.
$mfaReq = [Microsoft.Online.Administration.StrongAuthenticationRequirement]@{
RelyingParty = "*"
State = "Enabled"
}
Get-MsolUser -All | Set-MsolUser -StrongAuthenticationRequirements $mfaReq
Note. The AAD and MSOL PowerShell modules are in the pipeline for retirement anytime after December 2022. As of this writing, there’s no equivalent Microsoft Graph API SDK method of disabling or enabling per-user MFA yet.
Enable or Disable Security Defaults in Azure AD
Another way to enable or disable MFA in Azure Active Directory is through security defaults. This option affects every user in the organization and is not customizable.
Microsoft provides a default level of security for Azure AD tenants. The following settings will be applied when the security default is turned on in the tenant.
- Requiring all users to register for Azure AD Multifactor Authentication.
- Requiring administrators to do multifactor authentication.
- Requiring users to do multifactor authentication when necessary.
- Blocking legacy authentication protocols.
- Protecting privileged activities like access to the Azure Portal.
Source: Security defaults in Azure AD
Some organizations may find the security defaults sufficient, but some may prefer to customize their security policies.
To view the current Security Defaults settings in your Azure Active Directory tenant, log in to the Azure Active Directory admin center. Navigate to Azure Active Directory > Overview > Properties.
Under the Properties tab, you’ll see the status of the security defaults. The image below shows the message when the security defaults are turned off.
To enable, click the Manage security defaults link, select Enabled, and click Save.
The security defaults status changes, and it is now applied.
To disable the security defaults, click the Manage security defaults link, select Disabled, select a reason for disabling it, and click Save.
At the confirmation prompt, click Disable.
Create and Apply a Conditional Access Policy
The most recommended method of enforcing MFA in Azure AD is with conditional access.
Conditional Access is an Azure Active Directory (Azure AD) feature that allows administrators to enforce specific conditions that must be met before a user is granted access to resources or applications. It allows organizations to define access policies based on factors such as a user’s location, device, application, or risk level.
Using Conditional Access policies, administrators can define rules that restrict access to resources based on a user’s identity or the state of their device. For example, a policy can be created to require all users to use multi-factor authentication.
Let’s create a conditional access policy requiring MFA for Azure Active Directory users with optional exclusions.
Log in to the Azure AD admin center and navigate to Azure Active Directory > Security > Conditional Access > Policies.
Click New policy from template. This option allows you to choose a template for your policy.
Next, select the Require multifactor authentication for all users option and click Review + Create.
Leave the default options for now and click Create.
Note. Do not turn on the policy yet. Doing so may risk locking out your users and your account.
Click the new policy to open it.
Now, let’s add users and groups to exclude from the policy. It is rare for most organizations to not have exclusions for MFA. Some accounts, like service and emergency accounts, may need to be excluded from the MFA requirement.
Click Users > Exclude. Add the users and groups to exclude and click Select.
You’ll notice that your account was already added to the exclusion when you created the policy. Now, click On under the Enable policy section and click Save.
Note. Turning on the conditional access policy without observing its effect in Report-only mode first is not recommended. Ensure you allot ample time to analyze the policy’s impact on users when performing this in production.
The conditional access policy state is now turned on.
Users will be forced to register their MFA methods if they haven’t done so previously.
Conclusion
Multi-Factor Authentication (MFA) is an essential security feature that every organization should enable to protect their sensitive data and resources from unauthorized access. Azure Active Directory provides robust MFA capabilities that are easy to configure and manage.
In this blog post, we have discussed how to enable and disable MFA in Azure Active Directory using different methods. We have also explored configuring MFA policies and managing MFA users. By following these guidelines, organizations can strengthen their security posture and reduce the risk of data breaches and cyber-attacks.