Active Directory Domain Password Expiration Policy plays a crucial role in ensuring the security of user accounts within organizations. By enforcing regular password changes, this policy helps mitigate the risk of unauthorized access to sensitive information and protects against potential security breaches.
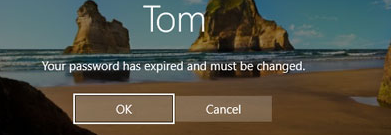
What happens when a user password expires in Active Directory? The user account is not blocked, but the user must change his password at the next logon: Your password has expired and must be changed.
Users can’t access domain resources and computers until they change their password.
In this blog post, we will explore the importance of password expiration policies and guide you through the process of configuring them within a domain environment.
Table of Contents
Does Microsoft Still Recommend Periodic Password Expiration?
Previously, Microsoft recommended periodically expiring Active Directory user passwords as a security measure. But, in recent years, Microsoft has updated its stance on this practice.
In their security baseline documentation (1903), Microsoft suggests that periodic password expiration may not be as effective as previously thought.
They emphasize the importance of strong, complex passwords and multi-factor authentication as more reliable security measures.
While it is still possible to configure password expiration policies, organizations should carefully evaluate the effectiveness of such policies based on their specific security requirements and risk assessments.
Getting User Password Expiration Date
Before diving into the password expiration policy, let’s have a refresher on how to get user password expiration dates using PowerShell. This method requires the PowerShell AD module.
You can perform this method on a domain controller or a computer with the Remote Server Administration Tools (RSAT) installed.
Run the PowerShell command to determine a user’s password expiration date. Replace alpha with the username you’re getting.
Get-ADUser -Identity alpha -Properties "msDS-UserPasswordExpiryTimeComputed" | Select-Object -Property Name, @{Name = "PasswordExpiryDate"; Expression = { [datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed") } }
This command retrieves the password expiration date for a user named “alpha” and displays it alongside the user’s name.
To retrieve the password expiration dates for all users, excluding those with the “PasswordNeverExpires” attribute set to “True,” run the following command:
Get-ADUser -Filter 'PasswordNeverExpires -eq "False"' -Properties PasswordNeverExpires, "msDS-UserPasswordExpiryTimeComputed" | Select-Object -Property Name, @{Name = "PasswordExpiryDate"; Expression = { [datetime]::FromFileTime($_."msDS-UserPasswordExpiryTimeComputed") } }
This command retrieves the password expiration dates for all users with the “PasswordNeverExpires” attribute set to “False” and displays the results, including the users’ names and corresponding password expiration dates.
Configuring Domain Password Expiration Policy
Now that we understand how to determine user password expiration dates, let’s delve into configuring the Domain Password Expiration Policy within a Group Policy Object (GPO).
To locate the password expiration policy settings within a GPO, follow these steps:
- Open the Group Policy Management Console (GPMC) on a domain controller or a machine with the Remote Server Administration Tools (RSAT) installed.
- Expand the desired domain within the GPMC and navigate to “Group Policy Objects.”
- Right click on the Default Domain Policy and select “Edit” to open the Group Policy Management Editor.
- In the editor, navigate to “Computer Configuration” → “Policies” → “Windows Settings” → “Security Settings” → “Account Policies” → “Password Policy.”
Within the “Password Policy” folder, you will find various password-related policy settings, including the “Maximum password age” value. By default, the user account passwords expire after 42 days from the last password change.
- Double-click on the “Maximum Password Age” policy setting to open its properties.
- Set the desired password expiration duration (in days) in the “Maximum password age” field. For example, if you want passwords to expire every 90 days, enter “90” as the value.
- Click “OK” to save the changes.
- You can run the gpupdate /force on a domain-joined machine or wait for the next Group Policy refresh interval. After which, all domain user accounts adhere to the updated password expiration policy.
- To confirm the applied GPO, run the following command to get the resultant set of policies.
Get-GPResultantSetOfPolicy -ReportType HTML -Path rsop.html
- Open the report and see the password expiration policy settings applied.
Configuring Fine-Grained Password Expiration Policy
In addition to the password expiration policy configuration through Group Policy Objects (GPO), Active Directory offers a more granular approach to password expiration policy known as Fine-Grained Password Policy (FGPP).
This feature allows administrators to define specific password policies for user groups or individuals within the Active Directory domain. This section will explore the differences between configuring password expiration policies via GPO and using the Active Directory Administration Center console password settings.
Furthermore, we will guide you through creating, configuring, and applying fine-grained password expiration settings.
Password Expiration Policy: Group Policy Object vs. Fine-Grained
When configuring password expiration policies, the primary difference between GPO and the FGPP console lies in their scope and level of control.
Group Policy Objects (GPO) provide a domain-wide approach to policy enforcement. By configuring password expiration settings in the GPO, the policy applies uniformly to all users within the targeted domain. GPOs are suitable for organizations that require consistent password policies across their entire Active Directory infrastructure.
On the other hand, the FGPP offers more flexibility through Fine-Grained Password Expiration (FGPP) policies. This allows administrators to create and apply different password policies to specific user groups or individual user accounts. FGPE provides a more tailored approach to password expiration, allowing organizations to address unique requirements based on user roles, security levels, or compliance needs.
Using Active Directory Administrative Center (GUI)
To create and configure a Fine-Grained Password Expiration policy, follow these steps:
- Open the Active Directory Administration Center console on a domain controller or a machine with the Remote Server Administration Tools (RSAT) installed.
- Navigate to “Domain” → “System” → “Password Settings Container.”
- Under the Tasks pane, click New → Password Settings.
- Provide a unique name for the password policy, precedence, and the maximum password age in days.
- Specify the users or groups to whom the policy should apply by adding them to the “Directly Applies To” section. In this example, I added the CA Server Admins group.
- Click OK to save the password policy.
The FGPE policy will now be applied to the specified user or group, providing a custom password expiration policy that differs from the domain-wide settings.
Using PowerShell
Using the same example, let’s create a fine-grained password expiration policy for another group of users.
- Open PowerShell as admin on the domain controller or a computer with RSAT installed.
- Run the following command to create a new fine-grained password policy. This policy will expire affected users’ passwords after 60 days from the last change.
# Create the new Fine-Grained password expiration policy $policySettings = @{ Name = 'Expire Password after 60-days' MinPasswordAge = '1.00:00:00' MaxPasswordAge = '60.00:00:00' Precedence = 1 } New-ADFineGrainedPasswordPolicy @policySettings # Display the new Fine-Grained password expiration policy Get-ADFineGrainedPasswordPolicy $policySettings['Name'] - Now, let’s assign this password expiration policy to specific targets. In this example, I’ll apply the policy to the CA DevOps group and the jsmith user account.
# Add new subjects to the password expiration policy. Add-ADFineGrainedPasswordPolicySubject -Identity 'Expire Password after 60-days' -Subjects 'CA DevOps', 'jsmith' # Display the password expiration policy subjects. Get-ADFineGrainedPasswordPolicySubject -Identity 'Expire Password after 60-days'
Summary
Thank you for reading and reaching the end of this post. Before you go, here are some summary points.
- GPO Password Expiration Policy is applied domain-wide.
- FGPP is applied to specific users or groups and takes precedence over GPO settings.
- FGPP cannot be turned off. Once created, it is enabled and applied. FGPP can only be deleted to stop them from applying to target AD groups and users.
- FGPP can be created and configured using the Active Directory Administrative Console (GUI) and PowerShell.
- Both types of password expiration policies only apply to user accounts directly or as members of groups. They do not apply to computer accounts.
- As of security baseline 1903, Microsoft no longer recommends periodic password expiration/changes as best practice. Instead, MSFT recommends implementing other measures such as:
- Banned-password lists
- Multi-factor authentication.
- Detection of password-guessing attacks
- Detection of abnormal logon attempts