When deleting a domain controller from Active Directory, it is advisable to use the DCPromo (demote) procedure, which allows you to correctly delete all records about the old domain controller from the Active Directory database (the computer object, NTDS Settings, site settings, cross-site links, and replication metadata).
Table of Contents
Why the Importance of Active Directory Metadata Cleanup?
Active Directory metadata cleanup is vital in ensuring the health and security of your Active Directory infrastructure. It primarily involves deleting obsolete data about a domain controller, which, if ignored, can lead to significant issues:
- Replication Issues: Metadata about a non-existent domain controller can lead to replication errors within Active Directory Domain Services (AD DS). Assuming the controller still exists, the system may attempt to replicate data causing efficiency problems.
- Conflicts: Old metadata can generate conflicts leading to inconsistencies in the directory data across controllers, causing challenges in managing users and resources.
- Security Concerns: Stale metadata about a failed domain controller can be exploited by malicious actors to gain unauthorized access, posing a risk to network security.
- Performance Impediments: Outdated server metadata can expand the directory database size, resulting in longer logon times and slower responses when accessing AD objects.
Therefore, whether using the Active Directory Users and Computers snap-in or command line tool like ntdsutil, metadata cleanup needs to be a routine process, ensuring that your network stays reliable, efficient, and secure.
Why is Metadata cleanup needed?
If your controller fails and is not planned to return, you can perform forced removal of the failed domain controller. This procedure is called Metadata cleanup. When you perform metadata cleanup, you will delete all data about the failed DC from Active Directory Domain Services (AD DS). This correctly cleans replication metadata, including the objects in File Replication Service (FRS) and Distributed File System (DFS).
Hint. Keep in mind to check that there are no FSMO roles on the broken DC, and if necessary, you can seize these roles to another DC.
Performing Metadata cleanup using Active Directory Users and Computers
In a domain with a functional level of Windows Server 2008 R2 and newer, you can clean server metadata using the standard Active Directory Users and Computers snap-in (dsa.msc) graphical console.
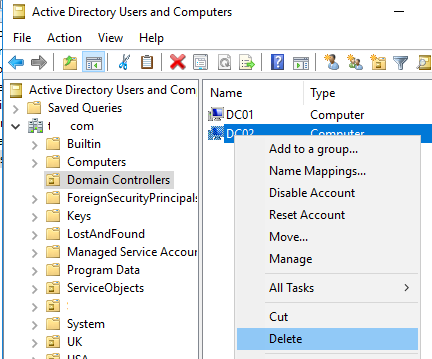
To do this, find the failed DC in the ADUC console and delete it as a regular computer object. Right-click on it, select Delete, and confirm the deletion.
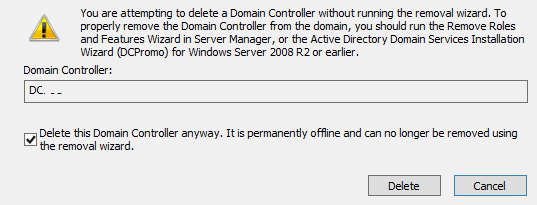
In the next dialog box, check the item “This Domain Controller is permanently offline and can no longer be demoted using the Active Directory Domain Services Installation Wizard (DCPromo)”, and click Delete button.
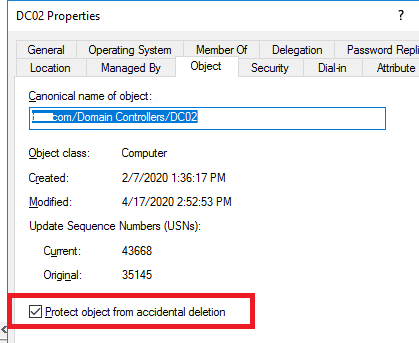
Hint. If the following error appears when you try to remove a DC “You do not have sufficient privileges to delete DC02, or this object is protected from accidental deletion”, please make sure:
- Your account is a member of the Domain admins group;
- The option “Protect object from accidental deletion” must be disabled in the object properties (ADUC snap-in > DC > Object tab).
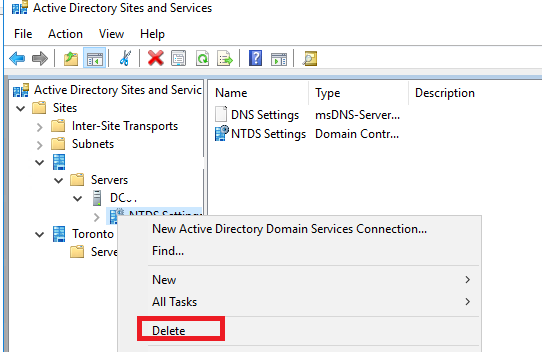
Then you need to open the Active Directory Sites and Services snap-in (dssite.msc) and delete the corresponding NTDS Settings object (expand the domain controller site, which forcibly removed, expand Servers > expand the DC name, right click on the NTDS Settings object > Delete ). Confirm the deletion of the object.
Next, ADDS will automatically perform metadata cleanup.
Running Metadata cleanup using ntdsutil
You can also clean up server metadata using the command-line tool ntdsutil (this is the only correct way to force remove failed DC in domains with a functional level of Windows Server 2008 and lower).
Run the command prompt as an administrator on any of the remaining domain controllers.
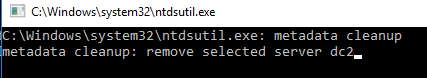
Type ntdsutil on the command line and press Enter.
Enter the following commands one after another:
metadata cleanup
remove selected server <failedDCName>
# specify the name of the DC to be removed from the AD database
Press Yes to correctly remove the DC object and metadata.
Type quit.
Verify that the domain controller has been successfully removed:
- Run the ADUC console. Make sure that the domain controller that you deleted has disappeared from the Domain Controllers container;
- Launch Sites and Services snap-in, check if your DC object does not contain an NTDS Settings object. If so, you can delete the server object in the console.
Frequently Asked Questions
1. What happens if metadata cleanup in Active Directory is not conducted?
If the metadata cleanup process is overlooked after a domain controller fails or is decommissioned, several problems may occur. The active directory may continue trying to replicate with the failed domain controller, leading to unnecessary replication errors. This can also cause the system to retain inaccurate information, resulting in potential conflicts and security vulnerabilities.
2. How do I perform a metadata cleanup for an offline global catalog server?
Performing metadata cleanup for an offline global catalog server follows the same procedure as any other domain controller. It involves using the Active Directory Users and Computers snap-in or the command line tool, ntdsutil, depending on your Windows Server’s functional level.
3. What are the potential security risks associated with not performing Active Directory metadata cleanup?
Not performing Active Directory metadata cleanup after a domain controller is permanently offline can provide a window for malicious actors. They can potentially exploit outdated server metadata, gaining unauthorized access to your network. Thus, promptly removing the metadata is crucial to mitigating such security risks.
4. Can the metadata cleanup be automated, or does it need manual intervention?
While certain aspects of metadata cleanup happen automatically in versions of Windows Server 2008 and above, such as removing a domain controller from the domain controllers container, a comprehensive cleanup may require manual intervention. Manual cleanup may include ntdsutil or removing the server object from the Active Directory Sites and Services snap-in.
5. What role does the NTDS settings object play in the metadata cleanup process?
The NTDS Settings object contains crucial metadata about a domain controller, including its replication partners. When a domain controller is decommissioned, its associated NTDS Settings object should also be deleted as part of the metadata cleanup process.
6. What privileges are necessary to perform Active Directory metadata cleanup?
To perform Active Directory metadata cleanup, you must be a member of the Domain Admins group. This privilege lets you delete the failed server object and other DNS records related to the decommissioned domain controller.
7. How can I confirm that metadata cleanup has been successful?
Post metadata cleanup, you can verify success by checking if the domain controller’s computer account is no longer present in the Domain Controllers container. Also, the NTDS Settings object should be missing from the Active Directory Sites and Services snap-in. Using the command prompt, you can review the list servers in the site and ensure the removed domain controller is no longer listed.
8. Is the cleanup process different for a different domain controller in the same domain?
No, cleaning up metadata remains the same regardless of whether the domain controller was part of the root or child domains. The crucial steps involve deleting the domain controller’s computer account, followed by the NTDS Settings object, and verifying the cleanup.
9. What’s the significance of FSMO roles during metadata cleanup?
FSMO (Flexible Single Master Operation) roles are essential for an AD environment. If a failed domain controller had any FSMO roles, these roles must be seized or transferred to another functional domain controller before performing metadata cleanup. Not doing so can lead to potential issues in the directory service operations.
10. What do I do if a warning message appears during metadata cleanup?
If a warning message appears during metadata cleanup, it usually indicates an issue with privileges or protection settings. Ensure your account is a member of the Domain Admins group and that the “Protect object from accidental deletion” option is disabled. If the problem persists, seeking assistance from an IT professional or exploring Microsoft’s official documentation is recommended.
Wrapping Up
Taking time for an Active Directory metadata cleanup is not just an administrative task but an essential step towards a healthy AD infrastructure. With domain controller deletion, it’s necessary to ensure all traces are removed, including server metadata. Using tools like Active Directory Users and Computers or the command line, you can effectively clean up metadata, depending on your Windows Server’s functional level.
However, remember to check for FSMO roles on the failed server before deletion and ensure that your account has adequate privileges. This process prevents replication errors, conflicts, and possible security risks.
Whether you are dealing with the server metadata of a failed domain controller or an offline global catalog server, the cleanup process is crucial. As a best practice, after metadata cleanup, you should verify that the domain controller’s computer account and NTDS Settings object are no longer present in the respective domain controllers container and Sites and Services snap-in.