NTDSUTIL is a command-line tool that Microsoft Windows Server administrators use to manage Active Directory (AD) and its related components. It allows administrators to perform various tasks, such as managing domains, trusts, and sites and configuring and troubleshooting Active Directory replication.
The tool is available on all Windows Server operating systems and can be used to manage both the local and remote AD instances. In this post, we’ll explore how to use NTDSUTIL, some typical use case scenarios, and best practices.
Table of Contents
Typical Use Case Scenarios
NTDSUTIL is a powerful tool that can be used for a variety of purposes. Some of the typical use case scenarios include:
- Managing Active Directory Database: NTDSUTIL can be used to manage the Active Directory database, which includes compacting, defragmenting, and repairing the database.
- Managing Domain Controller: It can also be used to manage domain controllers, including transferring and seizing FSMO roles, performing authoritative restores, and managing DNS configurations.
- Managing Active Directory Sites: NTDSUTIL can be used to manage Active Directory sites, including creating, deleting, and configuring sites and subnets.
- Managing Active Directory Trusts: The tool can be used to manage Active Directory trusts, including creating, modifying, and deleting trusts between domains.
Some Reminders Before You Begin
When using NTDSUTIL, it is essential to follow some best practices to ensure that the tool is used correctly and that it does not cause any adverse effects on the Active Directory environment. Here are some best practices to follow:
- Always have a backup of the Active Directory database before performing any NTDSUTIL operations. This ensures that you can restore the AD database to its previous state in case of any errors or damage caused by the tool.
- Understand the NTDSUTIL commands and their functions before running them. Some commands can cause significant changes to the AD environment, and you should ensure that you fully understand the effects of the command before running it.
- Run the tool as a domain administrator or enterprise administrator account. This ensures that you have the necessary privileges to perform the required tasks.
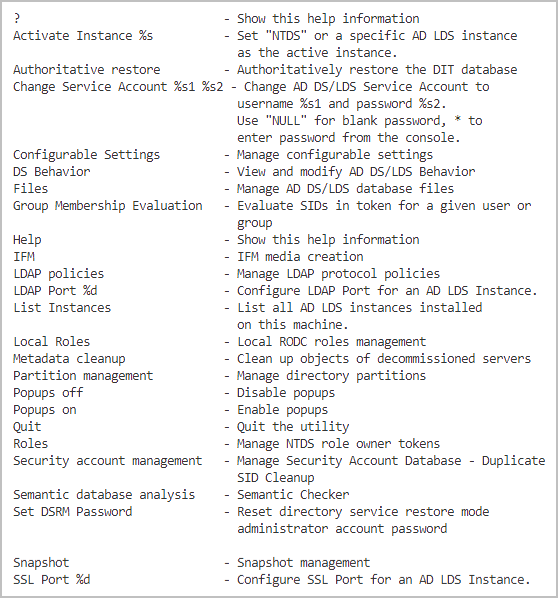
The NTDSUTIL tool has many subcommands available to manage different aspects of the Active Directory. To view the help system, run the below command in an elevated PowerShell or CMD session.
ntdsutil /?
As a result, you’ll get the list of top-level NTDSUTIL subcommands.
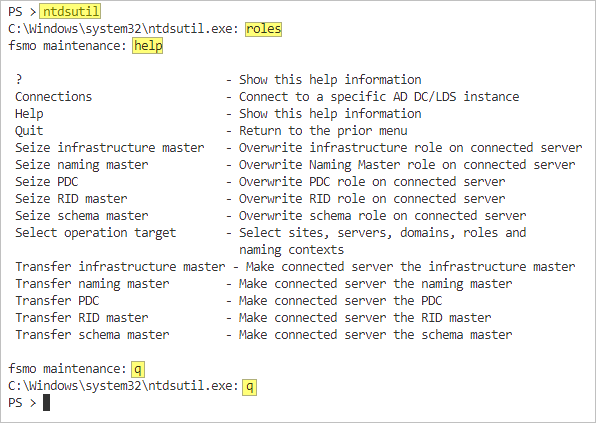
When you need help with a specific subcommand, you can enter the NTDSUTIL interactive prompt and run the help command. For example, if you’d like help with the Roles subcommand:
# Enter the NTDSUTIL prompt ntdsutil # Enter the subcommand roles # List the help for this subcommand help # Exit the subcommand q # Exit the NTDSUTIL prompt q
Using NTDSUTIL to Transfer FSMO Roles
One of the primary NTDSUTIL usages is transferring FSMO roles to another domain controller. There are five FSMO Roles:
- Schema master
- Domain naming master
- RID master
- PDC emulator master
- Infrastructure master
These roles can be assigned to different domain controllers in the forest or domain.
First, determine which server currently holds the FSMO roles.
netdom query fsmo
In this example, all the FSMO roles are owned by the DC1.theitbros.local server.
Suppose you need to transfer the FSMO roles to another domain controller, such as DC1.theitbros.local; follow these steps.
- Log in to any domain controller and open CMD or PowerShell as admin.
- Run the below commands in sequence to enter the fsmo maintenance mode:
ntdsutil roles connections
- On the server connections prompt, enter the following command. In this example, DC2 is the target domain controller server name:
connect to server DC2 quit
- You’re back to the fsmo maintenance prompt. To transfer the FSMO roles, run the below commands one at a time:
transfer schema master transfer naming master transfer rid master transfer pdc transfer infrastructure master
- Each command will ask you to confirm the transfer operation. Click Yes.
- In the end, DC2 will be the new owner of the FSMO roles:
- Finally, confirm the new FSMO role owner:
netdom query fsmo
You’ve successfully used NTDSUTIL to transfer the FSMO role owner.
Note. In the above example, the FSMO role transfer is performed between healthy DCs. But you can force seize any FSMO role from a failed domain controller.
Using NTDSUTIL to Reset the Administrator Password for the DSRM
NTDSUTIL can be used to change the Directory Services Restore Mode (DSRM) administrator account password, which is used to restore Active Directory in case of a disaster. Here’s how to use NTDSUTIL for this scenario:
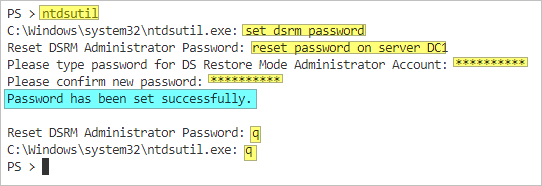
- To launch NTDSUTIL, open a command prompt or PowerShell with administrative privileges, type ntdsutil, and press Enter.
- Type set dsrm password and press Enter.
- Type reset password on server TargetDCName and press Enter, replacing TargetDCName with the domain controller name you want to change the password on.
- Type the new password for the DSRM administrator account and press Enter, then confirm the password by typing it again and pressing Enter.
- Type q and press Enter to exit the set dsrm password context.
- Type q and press Enter again to exit NTDSUTIL.
Using NTDSUTIL to Maintain Active Directory Database
NTDSUTIL can be used to manage the Active Directory database, including compacting, defragmenting, and repairing the database.
Note. The following tasks require that the AD database on the server is offline, so do this only during a planned maintenance window.
Stop Services
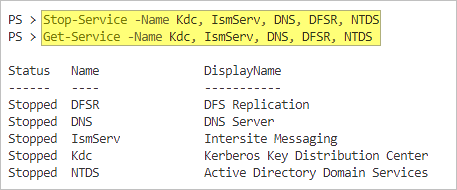
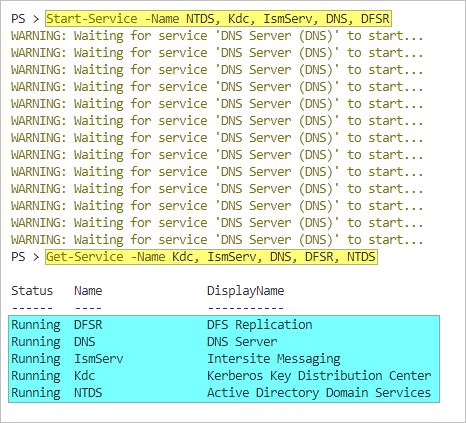
Before doing any AD database maintenance, make sure to stop the following services. Run the following command in an elevated PowerShell window.
# Stop the services Stop-Service -Name Kdc, IsmServ, DNS, DFSR, NTDS # List the status of the services Get-Service -Name Kdc, IsmServ, DNS, DFSR, NTDS
Compacting an Active Directory Database
The online defragmentation happens automatically every 12 hours. This task reorganizes the data in the database and can improve its performance.
But, online defragmentation does not reduce the database file size. When the database size grows large, it may cause performance issues, so periodically compacting the database should be on your maintenance list.
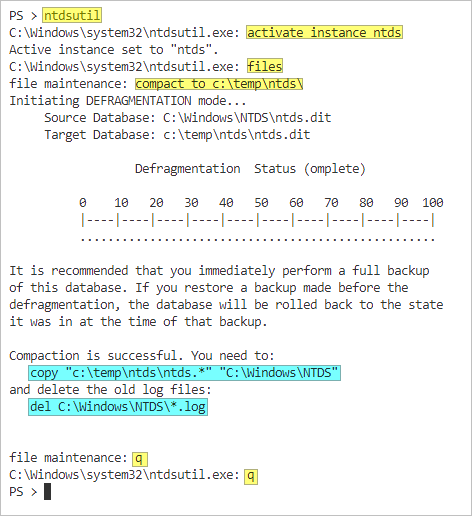
- In the elevated PowerShell prompt, type ntdsutil and press Enter.
- Type activate instance ntds and press Enter.
- Type files and press Enter.
- After entering the file maintenance context, type compact to <path>\newdb.dit and press Enter. Replace <path>\newdb.dit with the path where you want to save the new database file. This command creates a new, smaller version of the database.
Once the compact database process starts, you must wait for it to finish. The duration depends on how big the database is.
- After compacting the database, run the following commands to copy the newly compacted database to the original location. This command overwrites the old ntds.dit and ntds.jfm files:
copy "c:\temp\ntds\ntds.*" "C:\Windows\NTDS"
- Now, delete the old *.LOG files:
del C:\Windows\NTDS\*.log
Repairing an Active Directory Database
If you suspect that the AD database has errors, you can perform a repair on it.
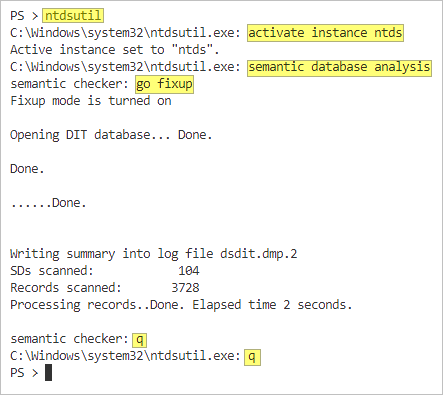
- In the elevated PowerShell prompt, type ntdsutil and press Enter.
- Type activate instance ntds and press Enter.
- To repair the database, type semantic database analysis and press Enter.
- Now that you’re in the semantic checker context, type go fixup and press Enter. This command checks the ntds.dit database and automatically fixes it if needed.
Start Services
Once you’ve completed the database maintenance, you can return the AD database online by starting the required services.
# Start the services Start-Service -Name NTDS, Kdc, IsmServ, DNS, DFSR # List the status of the services Get-Service -Name Kdc, IsmServ, DNS, DFSR, NTDS
Using NTDSUTIL to Manage Active Directory Snapshots
NTDSUTIL can be used to create and manage snapshots of Active Directory, which can be used to recover deleted objects or restore Active Directory to a previous state.
Creating a Snapshot
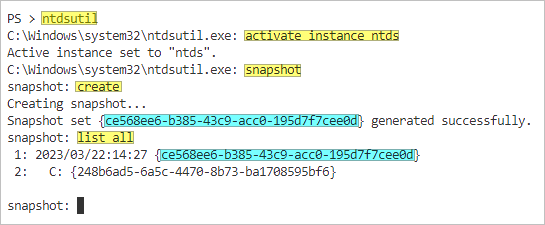
- In the elevated PowerShell prompt, type ntdsutil and press Enter.
- Type activate instance ntds and press Enter.
- To create a snapshot of Active Directory, type snapshot and press Enter.
- Type create and press Enter. This command creates a new snapshot of Active Directory.
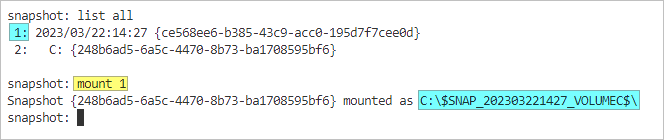
- Now, list all available snapshots by running list all. As you can see, the new snapshot was created. Take note of the GUID and position number of that snapshot.
Mount, Unmount, and Delete the Snapshot
- To mount a snapshot, type mount %s where %s is the index (position) or the GUID of the snapshot. In this example, the snapshot we’ll mount is in index 1.
Note. The snapshot is mounted as read-only.
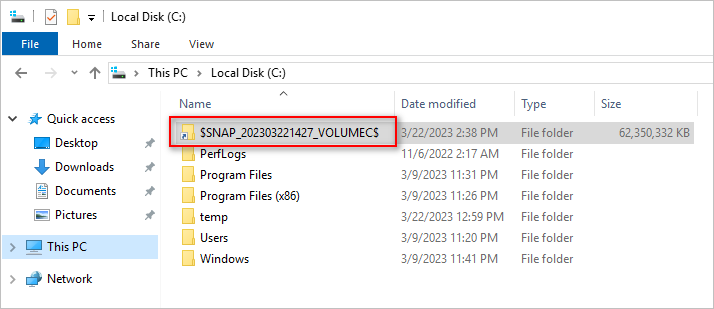
- Now, open the mount path in the File Explorer to view its contents:
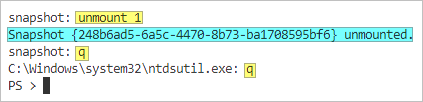
- Once you’re done reviewing the snapshot, you can unmount it by running the unmount %s command, where %s is the position or GUID of the snapshot:
- Finally, when you no longer require the snapshot, you can delete it by running the delete %s command, where %s is the position or GUID of the snapshot:
Using NTDSUTIL to Remove a Failed Domain Controller
When a domain controller fails and cannot be brought online again, you must ensure to clean it up from the environment. You can use NTDSUTIL to remove a failed domain controller.
Related: REPADMIN Tool: Checking Active Directory Replication Status.
There are several steps involved, which can be confusing, so make sure to follow the instructions carefully.
- Log in to a domain controller and open a PowerShell window as admin.
- Type ntdsutil and press Enter.
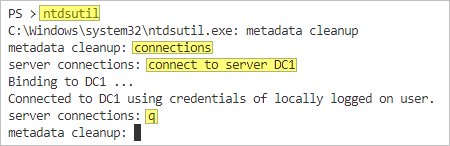
- Type metadata cleanup and press Enter.
- Type connections and press Enter.
- Type connect to server servername and press Enter. Replace servername with the name of the online/healthy domain controller.
- Type q and press Enter:
- Type select operation target and press Enter.
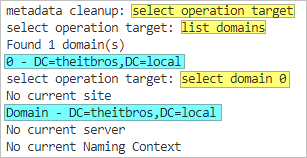
- Type list domains and press Enter. Note the domain to which the failed DC belongs. In this example, there’s only one domain.
- Type select domain %s and press Enter. Replace %s with the domain controller name to which the failed DC belongs.
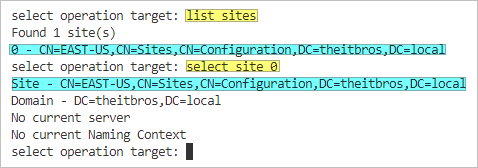
- Type list sites and press Enter. Note the site to which the failed DC belongs.
- Type select site %s and press Enter. Replace %s with the position or name of the site to which the failed DC belongs. In this example, there is only one site.
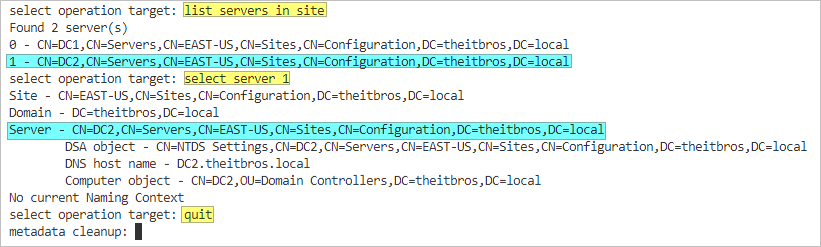
- Type list servers in site and press Enter. Note the name of the failed DC.
- Type select server %s and press Enter. Replace %s with the position number or name of the failed DC. In this example, the failed DC is DC2, which is in position 1.
- Type quit and press Enter.
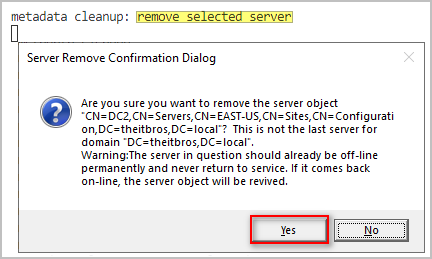
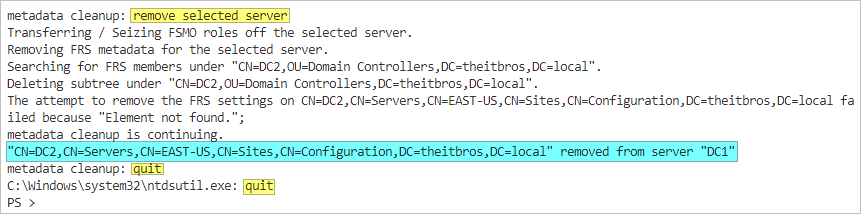
- Type remove selected server and press Enter.
- When asked to confirm, click Yes to confirm the removal of the failed DC.
- Type quit and press Enter.
- Type quit again and press Enter to exit Ntdsutil.
Removing a failed DC using ntdsutil requires careful attention to detail, as any mistakes can have serious consequences for your Active Directory environment. Therefore, it is recommended that you follow these instructions closely and seek assistance from an experienced Active Directory administrator if you have any doubts or concerns.
Conclusion
NTDSUTIL is a powerful command-line tool that allows Windows Server administrators to manage Active Directory and its related components. It is a versatile tool that can be used for various purposes, including managing domains, trusts, and sites and configuring and troubleshooting Active Directory replication.
But, due to its power, it is essential to follow best practices and be aware of the cautions when using the tool to ensure that it is used correctly and does not cause any adverse effects on the Active Directory environment.