In this article, we will look at how to transfer (or seize) one or more AD FSMO roles from one domain controller to another. You can use both the Active Directory graphical snap-ins and the PowerShell command prompt to transfer FSMO roles from one DC to another. Unlike graphical MMC snap-ins, PowerShell allows you to transfer or seize any role with just a single command.
Transferring FSMO roles is not an everyday task. It is usually needed when:
- Promoting new domain controllers
- Demoting old DCs
- Scheduled server maintenance (updating hardware and/or software)
- Disaster recovery
Table of Contents
Check FSMO Roles in Active Directory with PowerShell
By default, when you create a new Active Directory domain, all FSMO roles are assigned to the first domain controller in the forest root domain.
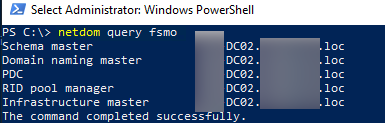
You can check how FSMO roles are assigned in your AD using the command:
netdom query fsmo
In this example, dc02.test.com holds all five FSMO roles.
There are 5 special roles for AD domain controllers called Flexible Single Master Operations (FSMO or Operations Master).
- Schema Master;
- Domain Naming Master;
- PDC;
- RID Master;
- Infrastructure Master.
You can also use the PowerShell Active Directory module cmdlets to get the forest level FSMO role holders (Domain Naming Master and Schema Master roles) in the specified domain:
Get-ADForest contoso.com| ft DomainNamingMaster, SchemaMaster
To view domain-wide FSMO role owners (Infrastructure Master, PDC Emulator, and RID master roles):
Get-ADDomain contoso.com | ft InfrastructureMaster, PDCEmulator, RIDMaster
Or you can get information about all roles in your AD using the following PowerShell one-liner:
Get-ADDomainController -Filter * | Select-Object Name, Domain, Forest, OperationMasterRoles | Where-Object {$_.OperationMasterRoles}
FSMO roles can be assigned to a single domain controller or spread across multiple DCs, depending on your requirement. There are two ways to move the FSMO role between domain controllers:
- Transfer — gracefully moving a role to a new owner if both DCs are online and considered healthy. Role transfers occur when you need to decommission a domain controller, perform routine maintenance tasks on a physical server or underlying hardware;
- Seize — forced grab of the FSMO role caused by unexpected circumstances such as hardware failure or crash of the original role holder. Performed in the scenarios of a non-operational (offline) role holder.
Transfer FSMO Roles Using PowerShell
The Move-ADDirectoryServerOperationMasterRole cmdlet is used to transfer FSMO roles between Active Directory domain controllers. Specify the name of the destination DC to which you want to transfer the role and the name of the operation master role(s).
Note. The Move-ADDirectoryServerOperationMasterRole can be used in an AD environment with at least Windows Server 2008 R2 OS version on a DC.
Choose the domain controller to transfer the FSMO role to. You can list DCs in Active Directory with the command:
Get-ADDomainController -Filter * | Select-Object HostName
For example, to transfer the PDC Emulator role to a domain controller named dc2, use the command (you can run this command from any DC):
Move-ADDirectoryServerOperationMasterRole -Identity dc2 -OperationMasterRole PDCEmulator
Press Y > Enter to confirm the role transfer. To skip the confirmation, you can add the -Confirm:$false parameter to the previous command.
It is possible to transfer several roles at once:
Move-ADDirectoryServerOperationMasterRole -Identity dc2 –OperationMasterRole DomainNamingMaster,PDCEmulator,RIDMaster,SchemaMaster,InfrastructureMaster
Tip. To make it easier to use the Move-ADDirectoryServerOperationMasterRole cmdlet, you can replace the names of roles with numbers from 0 to 4:
| PDCEmulator | 0 |
| RIDMaster | 1 |
| InfrastructureMaster | 2 |
| SchemaMaster | 3 |
| DomainNamingMaster | 4 |
So, the last command can be replaced by a shorter one:
Move-ADDirectoryServerOperationMasterRole dc2 –OperationMasterRole 0,1,2,3,4
You can move the forest-wide operations master roles to a directory server in a different domain in the same AD forest.
Note. Don’t put the role of the Infrastructure Master role on the same DC as the server that hosts the Global Catalog.
If you want to run the FSMO transfer command under a different user account, you can use the -Credential parameter:
$cred = Get-Credential Move-ADDirectoryServerOperationMasterRole dc2 -OperationMasterRole SchemaMaster -Verbose -Force -Credential $cred
Use the Get-ADForest and Get-ADDomain cmdlets to verify that the transfer task completed successfully.
In order to migrate the Operations Master roles, your account must be a member of the privileged domain groups: Domain admins, Enterprise Admins, and Schema Admins. If you receive an “Access Denied” error when you run Move-ADDirectoryServerOperationMasterRole, check that you are a member of the specified AD groups:
Move-ADDirectoryServerOperationMasterRole : Access is denied
Seizing FSMO Roles Using PowerShell
Whenever it’s possible, you should try to transfer FSMO roles rather than trying to cap seize ture them!
If you need to transfer the FSMO role from one DC to another, then a role transfer is the best option. If a DC that is currently performing an FSMO role goes offline (crashes or goes down for an extended period of time), the FSMO role cannot be transferred.
Move-ADDirectoryServerOperationMasterRole returns the following error when attempting to move a role from an offline server:
Move-ADDirectoryServerOperationMasterRole : The directory service is unavailable
Attempting to move an FSMO role from an offline DC using ADDS graphical snap-ins results in an error:
The transfer of the operation master role cannot be performed because: The requested FSMO operation failed. The current FSMO role holder could not be contacted.
In this case, you can use the -Force option to seize the FSMO role(s) from the offline DC:
Move-ADDirectoryServerOperationMasterRole -Identity dc2 –OperationMasterRole DomainNamingMaster,PDCEmulator,RIDMaster,SchemaMaster,InfrastructureMaster –Force
The old FSMO role holder should never be brought back online after the seize process is complete. There will be conflicts and inconsistencies in the ADDS if the old domain controller is connected to your infrastructure.
Be sure to remove this DC Computer object from your domain by using the forced removal of the failed domain controller and metadata cleanup procedure.
As you can see, PowerShell allows you to perform FSMO role management tasks much faster and easier than the Ntdsutil tools and the MMC snap-ins.