The error “The remote computer requires network level authentication…” may appear when connecting to a remote desktop (RDP) running Windows. In this article, we will explain why this error appears and how to fix it.
Network Level Authentication (NLA) is a security feature used by Remote Desktop Services that requires the client to be authenticated before establishing an RDP session with a remote host. NLA uses CredSSP, which allows Remote Desktop to delegate the user credentials from the client to the target host for remote authentication. NLA was introduced in RDP 6.0 (Windows Vista) and is supported by all modern versions of Windows.
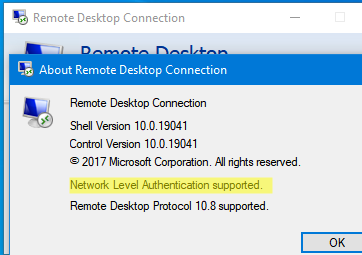
On Windows, the built-in Remote Desktop Connection client (mstsc.exe) supports NLA. You can verify this by running mstsc.exe > About. Make sure you have RDP client version >= 6.0 and the caption Network Level Authentication supported exists.
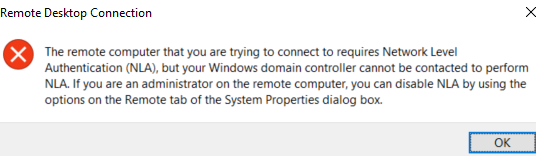
When connecting to a Windows host using Remote Desktop Connection, you may get this error:
The remote computer that you are trying to connect to requires Network Level Authentication but your Windows domain controller cannot be contacted to perform NLA. If you are an administrator on the remote computer, you can disable NLA by using the options on the Remote tab of the System Properties dialog box.
In this case, the remote Windows host is blocking RDP connections with NLA because it cannot connect to an Active Directory domain controller with the credentials of the domain user you are using for RDP authentication. In this case, you need to check:
- Make sure you are connecting to the RDP server by name and not by IP address;
- Check that the domain controller is reachable from the remote Windows host (How to fix Active Directory Domain Controller could not be contacted problem?) and healthy (Checking AD domain controller health);
- Check the Security Channel between the Windows host and the domain controller. You can check the trust relationship using the PowerShell command:
Test-ComputerSecureChannel -verbose
If this command returns False, you can repair the security channel with the command:
Test-ComputerSecureChannel -Repair -Credential corp\domain_adm
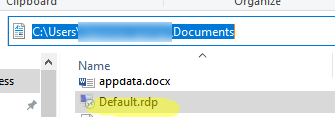
- Try resetting the RDP settings on the client by deleting the hidden Default.rdp file in the current user profile folder (%userprofile%\Documents).
If the solutions above didn’t fix the problem, you can try one of the two workarounds:
- Try to log in with a local administrator account instead of the domain account;
- You can disable NLA on the RDP-server side.
Note. For security reasons, it is not recommended to disable NLA in most cases. But if you are using an alternative RDP client (for example, on Linux or macOS) that doesn’t support NLA, these are the only ways to fix the connection problem.
You can disable Network Level Authentication in Windows in several ways:
Table of Contents
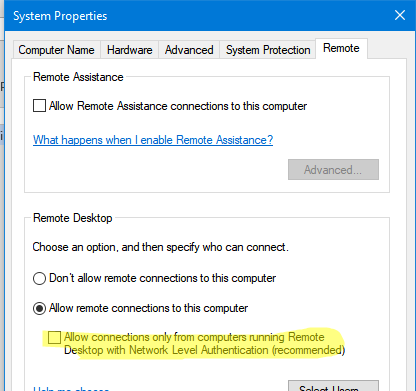
Method 1. Disable NLA via System Properties
- Run the sysdm.cpl command and go to the Remote tab;
- Disable the option Allow connections only from computer running Remote Desktop with Network Level Authentication (recommended).
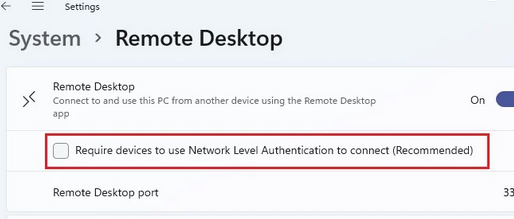
On Windows 11, you can disable NLA from Settings > System > Remote Desktop. Disable the option Require devices to use Network Level Authentication to connect.
.
Method 2. Disable NLA using Group Policy
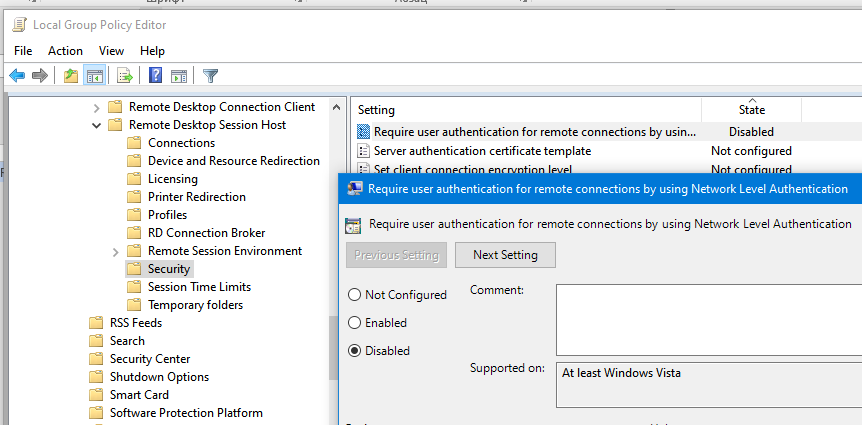
- Open the Local Group Policy Editor console (gpedit.msc);
- Go to Computer configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security;
- Open the option ‘Require user authentication for remote connections by using Network Level Authentication and set it to Disabled;
- Run the gpupdate /force command to update the local Group Policy settings.
Method 3. Disable Network Level Authentication using PowerShell
You can check the status of NLA on a remote computer (wks12lk22) using the following PowerShell command:
(Get-WmiObject -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -ComputerName wks12lk22 -Filter "TerminalName='RDP-tcp'").UserAuthenticationRequired
- 1 – NLA is enable;
- 0 – disables.
In order to disable NLA on a remote computer, use the command:
(Get-WmiObject -class "Win32_TSGeneralSetting" -Namespace root\cimv2\terminalservices -ComputerName wks12lk22 -Filter "TerminalName='RDP-tcp'").SetUserAuthenticationRequired(0)
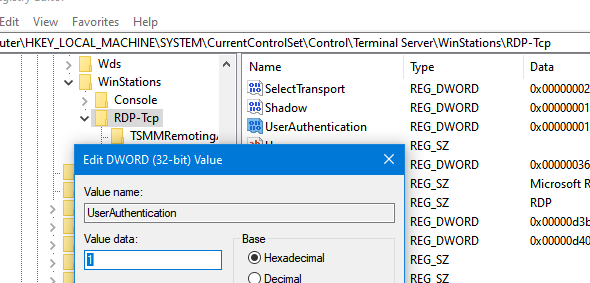
Note. The UserAuthentication setting is located under the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp. You can change its value manually.
In some cases, you must also set the value of the SecurityLayer registry entry to 0.
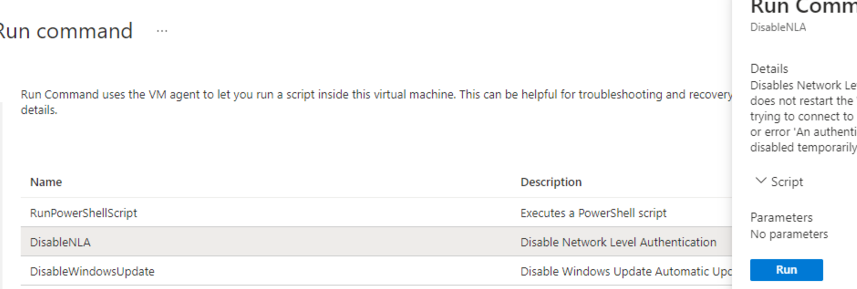
If you get the “The remote computer requires NLA…” error when trying to RDP to an Azure VM, you can disable NLA for that VM through the Azure Portal:
- Sign in to Azure Portal;
- Select your VM > go to Run command;
- Find the DisableNLA script and click Run.
These methods can be used to temporarily disable NLA. This will allow you to access the RDP host from a computer where the remote desktop client does not support NLA.

1 comment
I had this issue when I accidentally deleted the remote machine from Active Directory. Manually unjoining and rejoining the computer to AD resolved the issue.