Active Directory is a highly intricate IT ecosystem, even with primary domain controllers and a single Active Directory site. The capability to swiftly assess the health of Active Directory and resolve issues is crucial for a sysadmin. This article explores essential commands that can be employed to check the Active Directory health and identify potential errors.
Table of Contents
Check Services on the Domain Controller Servers
These services are crucial for the functioning and managing of a Windows domain network, providing various capabilities such as authentication, name resolution, time synchronization, and central directory services.
- NTDS (Active Directory Domain Services): NTDS stands for “NT Directory Services,” the core component of Active Directory in Windows. It is responsible for storing and managing information about objects in a network, such as users, computers, and groups. NTDS enables centralized authentication, authorization, and other administrative functions within a Windows domain environment.
- ADWS (Active Directory Web Services): ADWS is a service that provides a web service interface to access and manage Active Directory. It allows applications to interact with Active Directory using web service protocols such as Simple Object Access Protocol (SOAP) over HTTP. ADWS enables remote administration of Active Directory and is used mainly by administrative tools and applications to manage Active Directory objects.
- DNS (Domain Name System): DNS is a fundamental network service that translates domain names (e.g., www.example.com) into IP addresses (e.g., 192.168.0.1) and vice versa. It helps computers locate and communicate with each other over a network. The DNS service runs on Windows servers and enables domain name resolution, essential for various network activities like browsing the web, sending emails, and accessing network resources.
- Dnscache (DNS Client): Dnscache, also known as the DNS Client service, is responsible for caching and resolving DNS queries on a Windows computer. When you access a website or any network resource, the DNS Client service checks its local cache to see if it already has the IP address associated with the domain name. If not, it sends a request to a DNS server to resolve the domain name.
- KDC (Key Distribution Center): KDC is a service involved in the implementation of the Kerberos authentication protocol, which is used for secure authentication in Windows domains. The KDC issues and verifies tickets to authenticate users and grant them access to network resources. It ensures that only authorized users can access protected resources within a domain environment.
- W32time (Windows Time Service): W32time is the Windows Time Service responsible for time synchronization in a Windows environment. It ensures that all computers within a domain have synchronized time, essential for various network operations, including authentication, log file integrity, and event log accuracy. W32time can synchronize time with an external time source or a domain controller acting as the time server.
- Netlogon: Netlogon is a service that provides secure channel connections between domain controllers and clients in a Windows domain. It supports authentication and replication functions required for the Active Directory domain. Netlogon enables secure communication and authentication between domain members and facilitates the replication of Active Directory databases between domain controllers.
That said, monitoring these services’ status on your Active Directory servers is crucial.
Log in to a domain controller, open PowerShell as admin, and run the following command to get the status of the services.
$services = 'ntds', 'adws', 'dns', 'dnscache', 'kdc', 'w32time', 'netlogon'
Get-Service $services | Select-Object MachineName, DisplayName, Status
The command returns the status of the services on the local machine.
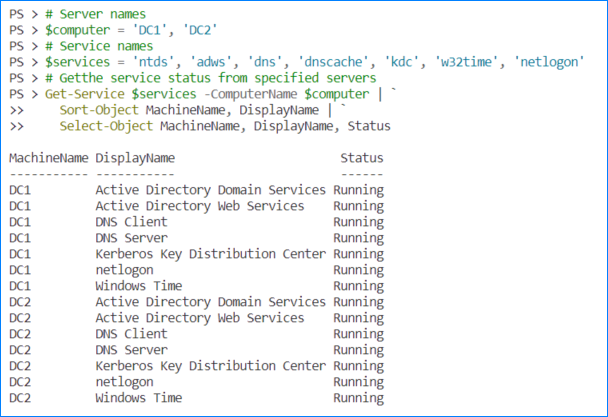
To get the status of the services from multiple servers, you can run the below commands instead. Ensure to replace the $computer values with yours. This example queries two servers – DC1 and DC2.
# Server names
$computer = 'DC1', 'DC2'
# Service names
$services = 'ntds', 'adws', 'dns', 'dnscache', 'kdc', 'w32time', 'netlogon'
# Getthe service status from specified servers
Get-Service $services -ComputerName $computer | `
Sort-Object MachineName, DisplayName | `
Select-Object MachineName, DisplayName, Status
This way, you get a bird’s eye view of the services and quickly identify which ones are not running.
Check Active Directory Health with DCDIAG
DCDiag is a command-line tool in Windows that is used to diagnose the health and functionality of the domain controllers in an Active Directory environment. It helps administrators identify and troubleshoot issues related to the domain controllers, DNS configuration, replication, and other components of Active Directory.
This command has multiple flags and options, which you can find by running the below command.
dcdiag /h
When you run the DCDiag command on its own, it performs a series of tests on the domain controller and provides a detailed report of the results. The tool checks various aspects of the domain controller’s functionality, including:
- Connectivity: DCDiag verifies the network connectivity between the domain controller and other domain controllers, ensuring they can communicate properly.
- DNS Configuration: It checks the DNS settings and ensures the domain controller can resolve DNS queries correctly.
- Active Directory Replication: DCDiag examines the replication process between domain controllers, ensuring that changes made on one domain controller are correctly replicated to others.
- Directory Services: It tests the overall health of the Active Directory database and checks for any errors or inconsistencies.
- Security: DCDiag verifies the security settings and permissions related to domain controllers, ensuring they are configured correctly.
- SysVol: It checks the availability and synchronization of the SysVol folder, which contains important Group Policy objects and scripts.
Testing Local vs. Remote vs. All
To test the local domain controller, you run dcdiag like this:
dcdiag
To test the remote server, append the /s flag:
dcdiag /s: DC2
Run the below commands to test all domain controllers within the site or in the enterprise:
# Test all DCs in a site
dcdiag /a
# Test all DCs in the enterprise
dcdiag /e
Focusing on Errors
The DCDiag results can be overwhelming because of their verbosity. But, like any monitoring, it makes more sense to know which tests failed than which ones passed. To limit the result to show errors only, use the /q flag.
dcdiag /a /q
Running Specific Tests
You can run specific tests with DCDiag, such as DNS and NetLogons. You can find all known tests by running dcdiag /h and referring to “The list of known tests”.
For example, you can run the DNS test by running this command:
dcdiag /test:DNS /v /e
The /v switch makes the output verbose and summarizes the results. If there is no problem with the DNS service, PASS should be indicated everywhere in the “Summary of DNS test results” section.
The /test:DNS flag runs the following DNS sub tests. You can also run each of the above DNS sub-tests individually.
|
DNS Sub test |
Details |
|---|---|
|
/DnsBasic |
Performs the basic DNS tests |
|
/DnsForwarders |
Tests the forwarders and root hints |
|
/DnsDelegation |
DNS delegation test |
|
/DnsDynamicUpdate |
Tests the DNS dynamic updates |
|
/DnsRecordRegistration |
Tests the DNS record registration |
|
/DnsResolveExtName |
Runs a DNS name resolution of the www.microsoft.com address by default. |
|
/DnsAll |
Runs all the above tests |
|
/DnsInternetName: |
Runs a DNS name resolution test of the given internet address |
If there are errors in the test, you can instruct DCDiag to perform safe repairs by adding the /fix flag before trying to fix them manually.
DCDiag /Test:DNS /s:DC1.theitbros.com /fix
Another example is the NetLogns test.
dcdiag /test:netlogons
Skipping Specific Tests
Some tests can be skipped, especially if they have errors you know can be ignored. For example, when I run the below command, it performs the tests and outputs only the errors found.
dcdiag /q
As you can see, the SystemLog test failed because events were showing the server could not communicate with external DNS forwarders 8.8.8.8 and 1.1.1.1. But I can confirm that the DNS forwarders are working, so I can safely exclude this test.
To skip the SystemLog test, I’ll use the /skip:<test_name> flag:
dcdiag /skip:systemlog /q
As you can see below, the SystemLog test error did not show up in the results, letting you focus on other possible issues.
Redirecting Test Results to File
Sending the DCDiag results to a file can be handy for later reviewing or if you have a workflow that sends the results via email.
You can do this in a few ways.
Using the /f:<log_file_path> flag:
dcdiag /test:DNS /v /f:dcdiag_log.txt
Using the > output redirector:
dcdiag /test:DNS /v > dcdiag_log.txt
Using the Out-File PowerShell cmdlet:
dcdiag /test:DNS /v | Out-File dcdiag_log.txt
Check Active Directory Replication Health with REPADMIN
The REPADMIN tool is a command-line utility used in Microsoft Windows Server environments for managing and troubleshooting replication issues in Active Directory.
System administrators primarily use it to diagnose and repair problems in Active Directory replication between domain controllers.
To learn how to use REPADMIN to check Active Directory health, visit our related articles:
- Repadmin Tool: Checking Active Directory Replication Status.
- How to Check Active Directory Replication?
Incorrect server time can also contribute to Active Directory errors. To test, run the command below in your domain controller.
w32tm /monitor
The desired result is that the NTP offset is around 0 (+/-), which means that the server time is not too far off.
Related. How to Sync Client Time with Domain Controller on Windows?
If not, you should also check the NTP Time Sync.
Related. How to Export All Group Policies to HTML Report or File?
Also, verify if all domain controllers have SYSVOL and Netlogon folders published as network shares. These folders are needed to apply and replicate Group Policy Objects. The list of shared folders on a DC can be displayed with the command:
net share
Conclusion
Regularly checking Active Directory health is important to ensure it is running smoothly and securely. By using the commands and techniques described in this article, sysadmins can quickly identify and fix any problems that may occur. This will help to prevent AD from becoming unavailable or corrupted, which can cause serious disruptions to an organization’s IT infrastructure.
Here are some additional tips for keeping AD healthy:
- Monitor AD replication status. Replication is the process of copying AD data to all domain controllers in a domain. If replication fails, it can cause data loss and other problems. You can use the repadmin command to monitor the replication status.
- Back up AD regularly. A backup is a copy of AD data that can be restored during a disaster. It would be best if you backed up AD regularly.
Related. How to Backup Active Directory? - Train your staff. Your staff should be trained on how to use AD to report problems. This will help to ensure that issues are identified and fixed quickly.
By following these tips, you can help to keep AD healthy and secure.