Azure Resource Locks allow administrators to protect resources in Azure Resource Groups from accidental deletion or changes. You can lock almost all types of Azure resources: virtual machines, web apps, storage accounts, databases, Azure Kubernetes Service (AKS) instances, virtual networks, etc. In this article, we want to show you how to use Azure Resource Locks in Azure Resource Manager. You can add or remove Azure Resource Locks through the Azure Portal, using PowerShell or Azure CLI.
You can set two types of locks with Azure Resource Locks:
- ReadOnly — users can read the resource but cannot edit its attributes or delete it;
- CanNotDelete — users can read and modify the resource, but cannot delete it.
Resource locks can be assigned at different levels in the Azure resource hierarchy.
- Subscription;
- Resource Group;
- Resource.
Note that locks are inherited on all child objects. The more restrictive lock will take precedence.
Note.
-
By default, locks can be assigned by the Owner or administrators (with a User Access Administrator role);
-
Azure locks only affect Azure objects, not the data in them;
-
Unlike RBAC, Azure locks apply to all users and roles.
Enable Azure Resource Lock via Azure Portal
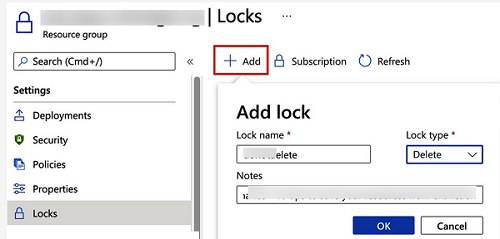
- In the properties of almost all types of Azure resources on the Azure Portal, there is a separate Locks tab. Select it;
- Click the Add button, specify the lock name, Lock type, and a small lock description/comment;
- Save changes;
- The specified resource is now protected with Azure Lock.
Now let’s look at how to lock an Azure resource using PowerShell.
- Sign in to Azure account using the command:
Login-AzAccount
- If multiple Azure subscriptions are associated with your UserPrincipalName, you can select the subscription:
Get-AzSubscription Select-AzSubscription -Subscription "TheITBrosSubs"
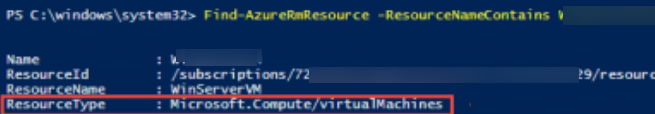
- Let’s try to enable lock for the Azure VM. First, you need to get the type of the object Azure:
Find-AzureResource -ResourceNameContains MyTestVM
In this example, we got the type of this Azure object – Microsoft.Compute/virtualMachines. - To lock this resource, you need to specify the lock name, resource name, resource group, and resource type:
New-AzureRmResourceLock –LockName LockDeleteMyTestVM -LockLevel CanNotDelete –-ResourceGroupName HQ-TEST-RG -ResourceName MyTestVM –ResourceType Microsoft.Compute/virtualMachines
Hint. If you’re using the Azure CLI, you can enable the same VM lock with the command:
az lock create \ --name LockDeleteMyTestVM \ --resource-group HQ-TEST-RG \ --resource MyTestVM \ --lock-type CanNotDelete \ --resource-type Microsoft.Compute/virtualMachines
Now if someone (even an administrator or owner) tries to delete this virtual machine, an error will appear:
Failed to delete the virtual machine VMName. Error: ScopeLocked… Cannot perform delete operation because following scope(s) are locked. Please remove the lock and try again.
To unlock the virtual machine, run the command:
Remove-AzureRmResourceLock -LockName LockDeleteMyTestVM -ResourceGroupName HQ-TEST-RG -ResourceName MyTestVM –ResourceType Microsoft.Compute/virtualMachines
You can lock an entire Azure resource group:
New-AzureRmResourceLock -LockLevel CanNotDelete -LockName LockDelHQTEST-RG -ResourceGroupName HQ-TEST-RG
List all locks in your Azure subscription:
Get-AzResourceLock
Azure Resource Lock will help to protect your critical resources from accidental deletion or modification.