Microsoft released a security update that fixes a remote code execution vulnerability in the Credential Security Support Provider Protocol (CredSSP) in March 2018. This vulnerability (CVE-2018-0886) allows an attacker to remotely execute arbitrary code on a vulnerable Windows host with an open RDP port (TCP/3389).
Any app or service that uses the CredSSP provider for authentication may be vulnerable to this type of attack. In May 2018, an update, “2018-05 Security only/Monthly Rollup,” was released. This security update blocks the RDP connection to and from computers with an affected version of CredSSP.
Table of Contents
Checking If the CredSSP Patch is Installed
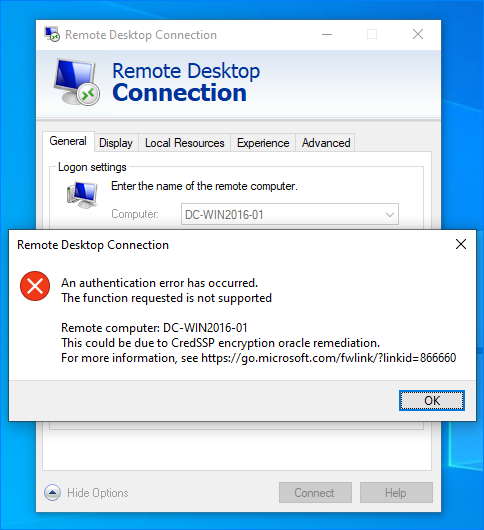
If the RDP client or server does not have the CredSSP update installed, the RDP connection attempt is blocked, and the following error appears:
An authentication error has occurred.
The function is not supported.Remote Computer: hostname
This could be due to CredSSP encryption oracle remediation.
The best way to check whether your computer is affected by this change is to determine the %systemroot%\system32\TSpkg.dll version and compare it to the table below per operating system.
| Operating system | TSpkg.dll version with CredSSP Patch |
| Windows 7 Service Pack 1 / Windows Server 2008 R2 Service Pack 1 | 6.1.7601.24117 |
| Windows Server 2012 | 6.2.9200.22432 |
| Windows 8.1 / Windows Server 2012 R2 | 6.3.9600.18999 |
| RS1 – Windows 10 Version 1607 / Windows Server 2016 | 10.0.14393.2248 |
| RS2 – Windows 10 Version 1703 | 10.0.15063.1088 |
| RS3 – Windows 10 1709 | 10.0.16299.431 |
If the TSpkg.dll version on your computer is lower, then your computer is unpatched. The following command retrieved the TSpkg.dll version.
(Get-ItemProperty -Path $env:SystemRoot\System32\TSpkg.dll).VersionInfo | Format-List
The screenshot below shows that the Windows Server 2016 computer is unpatched because the version (10.0.14393.0) is below the patched version (10.0.14393.2248).
The screenshot below is from an updated Windows 10 computer, so the TSpkg.dll version is higher.
CredSSP Server-Client Interoperability
The CredSSP update introduced this registry key.
| Registry path | HKLM |
| Value | AllowEncryptionOracle |
| Date type | DWORD |
The possible values for this registry key are:
| Registry value | Policy equivalent |
| 0 | Force updated clients |
| 1 | Mitigated |
| 2 | Vulnerable |
Note. When the CredSSP update is installed, the default AllowEncryptionOracle value is 1 (Mitigated).
Based on the table above, the interoperability between server and client RDP CredSSP policy settings is shown in the table below.
In summary, the “This could be due to CredSSP encryption oracle remediation” error only happens if any of the two computers involved in the RDP connection has not installed the CredSSP security update.
Recommended Solution to Fix the “This could be due to CredSSP encryption oracle remediation” Error
The best solution to fix the “This could be due to CredSSP encryption oracle remediation” error is to apply the CredSSP update to all computers.
The CredSSP update installs automatically via Windows Update. Ensuring your computer gets the latest update will fix this error.
But if your servers do not get updates automatically, refer to the CredSSP updates for the CVE-2018-0886 article to find the appropriate update for your computer.
Workaround to Bypass the “This could be due to CredSSP encryption oracle remediation” Error
If applying the CredSSP update is not an option, or at least not an immediate one, you can temporarily implement one of the two workarounds.
Reminder: These workarounds are intended as temporary solutions. Once you’ve accomplished your tasks or have updated the systems with the latest CredSSP security patches, you must revert the changes you made.
Modify the “Encryption Oracle Remediation” Group Policy
- Open the Local Group Policy Editor on the computer with the CredSSP patch installed.
gpedit.msc - Navigate to Computer Configuration → Administrative Templates → System → Credential Delegation → Double-click on the “Encryption Oracle Remediation” policy.
- Change the Protection Level to Vulnerable and click OK.
- Close the Local Group Policy Editor.
Modify the “AllowEncryptionOracle” Registry
Note. The “Encryption Oracle Remediation” group policy overwrites the changes you make to the “AllowEncryptionOracle” registry.
We can also temporarily bypass the “This could be due to CredSSP encryption oracle remediation” error by modifying the “AllowEncryptionOracle” registry value to 2 (Vulnerable).
Open an elevated command prompt or PowerShell and run the following command.
reg add HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters /f /v AllowEncryptionOracle /t REG_DWORD /d 2
Once you run the command, it changes the “AllowEncryptionOracle” value in the registry.
You can modify the same registry item on a remote computer via PowerShell remoting.
# Connect to the remote computer Enter-PSSession -ComputerName <REMOTE COMPUTER> # Change the AllowEncryptionOracle value to 2 (Vulnerable) Set-ItemProperty -Path 'HKLM:\Software\Microsoft\Windows\CurrentVersion\Policies\System\CredSSP\Parameters' -name "AllowEncryptionOracle" 2 -Type DWord
Disable the “Network Level Authentication (NLA)” on the RDP Server
Disabling the NLA on a remote machine is not the best practice. Still, it may be necessary if you cannot RDP into it due to the “This could be due to CredSSP encryption oracle remediation” error.
To disable the NLA on the RDP server, open the System Properties by running the sysdm.cpl command.
Switch to the Remote tab, uncheck the “Allow connections only from computers running Desktop with Network Level Authentication (recommended)” box, and click OK.
You can also use PowerShell to turn off NLA by running this command:
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "UserAuthentication" -Value 0
Conclusion
The CredSSP updates for CVE-2018-0886 were first released in March 2018 for systems running on Windows 10 1709 and Windows Server 2016 1607 and lower. Since then, newer Windows versions already include this security patch.
So, if your organization is keeping all computers updated, the “This could be due to CredSSP encryption oracle remediation” error should no longer occur. But if it did, you may still try the workarounds in this tutorial.









3 comments
What complete bullshit. I reinstalled Windows 10 and searched for updates. Windows Update says my machine is up-to-date, version 1511, but RDP into it doesn’t work. There’s no option to install a newer version or any more updates. Tell us exactly what update to install and where to download it.
Windows 10 version 1511 went end-of-support in 2018. You should upgrade to build Windows 10 version 21H2, which is expected to be supported through at least 2023 (and Windows Update should prompt you to download & install the next “feature update” aka version when it’s time to do so). The Windows 10 Update Assistant should help you upgrade to 21H2 in the meantime, since your built-in Windows Update is no longer able to find any updates.
https://en.wikipedia.org/wiki/Windows_10_version_history#Channels
https://support.microsoft.com/en-us/topic/windows-10-update-assistant-3550dfb2-a015-7765-12ea-fba2ac36fb3f
Hope this helps!
I’ve tried every solution on the web and nothing worked for me.
Finally after trying for almost 8 hours the only thing that worked was making a new Administrator account and logging in with it. Don’t know why but it did the trick.