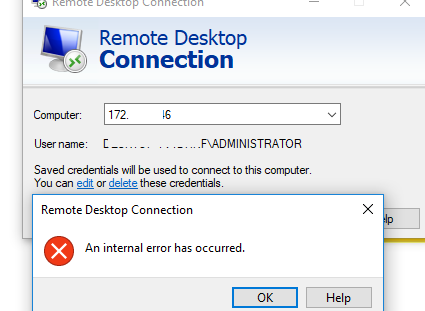
In some cases, when connecting to a remote computer or RDS host via Remote Desktop Connection (RDP), users may encounter an “An internal error has occurred” error. This error can occur for a number of reasons related to both the RDP/RDS server and the client settings.
The “An internal error has occurred” error usually shows after user credentials are entered in the mstsc.exe window or immediately after the Connect button is clicked.
As there are several possible causes for this internal RDP error, try the following tips one by one until you find a solution that will help you.
Table of Contents
Check the Remote Desktop Settings on the Client Device
If the “An internal error has occurred” error is only showing on one computer and other clients are successfully connecting to the Remote Desktop host, you need to check the settings on the current client device.
Reset the DNS client cache on your computer by running the following command from an elevated command prompt:
ipconfig /flushdns
If you have entered the hostname or FQDN of the remote computer in the RD Client window, try to establish an RD connection using an IP address. If the Remote Desktop IP connection is successful, use the nslookup command to check that the DNS settings on your computer are correct:
nslookup yourRDShost
Hint. If the DNS settings are not configured correctly, the Remote Desktop can’t find your computer error will appear.
Then check that the default RDP port (TCP/3389) is available on the remote server and the connection is not blocked by a firewall. Open the PowerShell console and run the command:
Test-NetConnection yourRDShost -port 3389
This command will return TcpTestSucceeded: True if the RDP port is not blocked.
If you are using a VPN to connect to a remote network, try disabling the VPN connections and try reconnecting to the RDP host. You can find and disable all active native Windows VPN connections using PowerShell:
foreach ($item in get-vpnconnection | where { $_.ConnectionStatus -eq "Connected" })
{
Rasdial $item.Name /disconnect
}
If you are using third-party VPN software, disconnect VPN sessions from its interface.
Open the properties of your RDP connection in Remote Desktop Connection windows (mstsc.exe) and make sure the ‘Reconnect if the connection is dropped‘ option is enabled on the Experience tab.
Also, try to disable the Server Authentication warning in the Advanced tab of the RDC client. Set the If server authentication fails to Connect and don’t warn me.
Check the Security Event Log for the following event ID 5379:
Credential Manager credentials were read.
This event occurs when a user performs a read operation on stored credentials in Credential Manager.
Your RDP client may have tried to use saved RDP credentials to connect. You should try removing the saved password from Windows Credential Manager:
- Open the Windows Credentials via the Control Panel. Or by running the command:
rundll32.exe keymgr.dll,KRShowKeyMgr
- Delete the saved RDP logon credentials for your remote host. Find the entry that starts with TERMSRV\your_rdp_host_name or TERMSRV\your_rdp_IP_address and click the Remove button;
Use the following batch script to clear the RDP cache on the client:
@echo off reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Default" /va /f reg delete "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" /f reg add "HKEY_CURRENT_USER\Software\Microsoft\Terminal Server Client\Servers" attrib -s -h %userprofile%\documents\Default.rdp del %userprofile%\documents\Default.rdp del /f /s /q /a %AppData%\Microsoft\Windows\Recent\AutomaticDestinations del /f /s /q /a "%userprofile%\AppData\Local\Microsoft\Terminal Server Client\Cache"
Save this code to the reset_mstsc_cache.bat file and run it as an administrator.
Next, check the settings on the RDP host side if none of these tips work.
Check the Remote Desktop Host Settings
If the Remote Desktop connection error occurs on all clients, the simplest way to resolve the problem is to reboot the remote RDP/RDS host.
If you cannot restart the RD host immediately, you should try to restart the Remote Desktop Service (along with the Remote Desktop Services UserMode Port Redirector). You can do this with the following commands running in the elevated cmd.exe:
net stop termservice net start termservice
Or you can restart Remote Desktop Services from the services.msc console.
If the problem disappeared after a restart, but it reappears after a while, then you need to try to change the settings of the RD Session host.
Use GPO to Fine-tune the RD Host Settings
Try to change some Group Policy settings using the Local GPO editor (gpedit.msc) or domain Group Policy Management Console (gpmc.msc).
- Disable UDP protocol for RDP connections. Navigate to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections, enable the policy Select RDP transport protocols and set Select Transport Type = Use only TCP. This will completely disable the use of UDP for RDP connections;
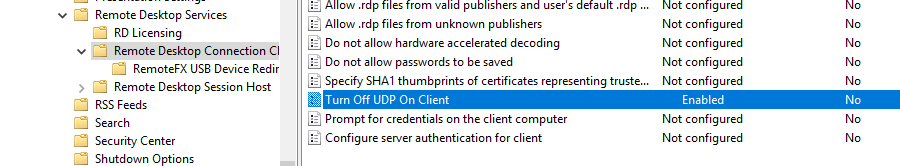
- The error “An internal RD error has occurred” often only occurs on clients that are connected to the network via a VPN tunnel. It seems that the problem is caused by the fragmentation of the UDP packets in the VPN tunnel. To disable RDP over UDP on a specific client only, enable the following GPO option on that computer: Off UDP on Client = Enabled under Computer configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Connection Client > Turn Off UDP on Client = Enabled;
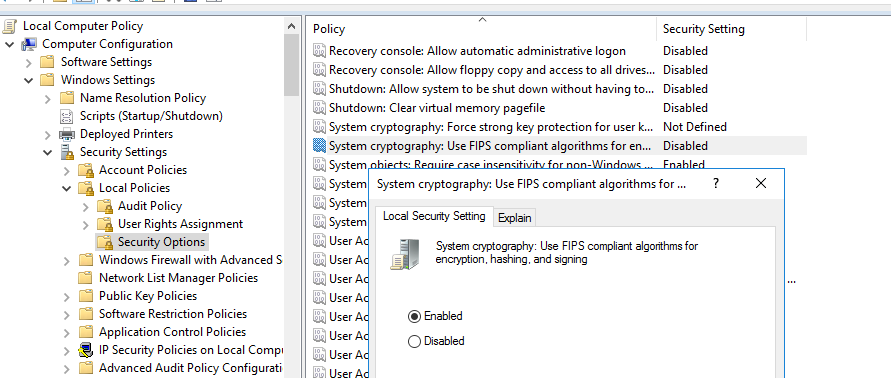
- Enable FIPS compliant algorithms: Computer configuration > Windows Settings > Security Settings > Local Policies > Security Options > System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing = Enabled;
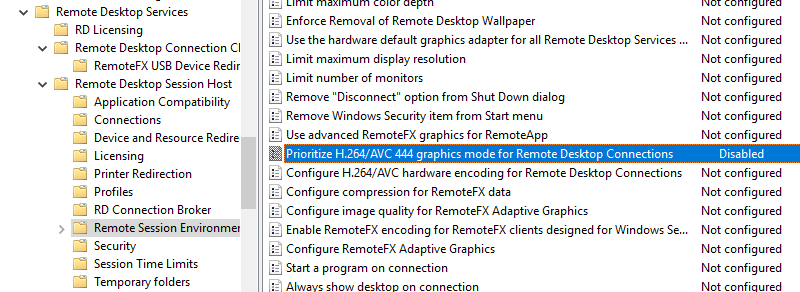
- Disable the hardware encoding and enforced AVC:444 mode on the RDP server side: Computer configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Remote Session Environment > Prioritize H.264/AVC 444 Graphics mode for Remote Desktop Connection = Disabled;
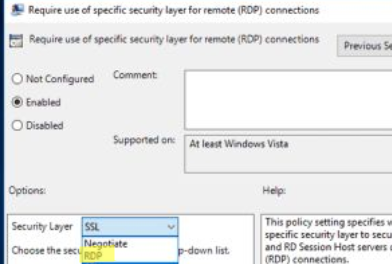
- Try to adjust the RDP security level to RDP mode. Enable the policy ‘Require use of specific security layer for remote connections’ under the GPO section Computer configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security and set the Security level to RDP (according to the article). Restart the remote host to apply this setting.
After changing the local Group Policy settings on a remote server, you need to apply them on the client and server using the gpupdate command.
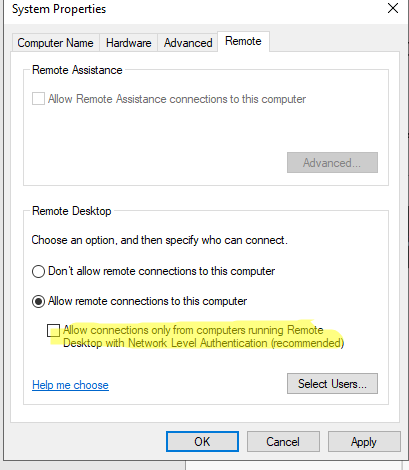
Check Network Level Authentication
To secure RDP connections, Network Level Authentication (NLA) is enabled by default on the RD host. In some cases, NLA can prevent RD connections from legacy or incompatible devices. You can temporarily disable NLA and see if the insecure remote desktop connection works as one of the troubleshooting steps.
Network Settings on Remote Desktop Host
If you are using NIC Teaming (bonding) on your Windows Server host, make sure that the receive side scaling is disabled.
- Open the Device Manager console (devmgmt.msc);
- Expand the Network adapters and open the properties of the Microsoft Network Adapter Multiplexor Driver;
- Go to the Advanced tab and set Receive Side Scaling to Disabled.
You can try to change the maximum outstanding connections limit on your RDP server via the registry. Set the following registry value via regedit.exe:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server DWORD: MaxOutstandingConnections VALUE: 10000
Or with PowerShell:
New-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Control\Terminal Server" -Name MaxOutstandingConnections -Value 10000 -PropertyType DWORD -Force
Check the current MTU size in your Windows with the command:
netsh interface ipv4 show subinterfaces
If the current MTU size for your network interface is equal to or more than 1500 (default Windows value), reduce it by using the command:
netsh interface ipv4 set subinterface "vEthernet (vSwithcExternal)" mtu=1452 store=persistent
RDS Certificates
When you use a smart card certificate to authenticate on the Remote Desktop server, you may encounter the following events in the RemoteDesktopServices-RdpCoreT log on the Windows Server 2019/2016 RDS host:
Warning Event 226, RemoteDesktopServices-RdpCoreTS
General: RDP_TCP: An error was encountered when transitioning from StateUnknown in response to Event_Disconnect (error code 0x80070040)
Warning Event 142, RemoteDesktopServices-RdpCoreT
General: TCP socket READ operation failed, error 64
Make sure your certificate has not been revoked.
Next, try to recreate the RDP certificate:
- Open the local computer certificates MMC snap-in (run the certlm.msc command);
- Go to the following certificate section: Remote Desktop > Certificates;
- Right-click your self-signed certificate RDP cert and delete it (if there are several RDP certs, remove them all);
- Restart the Remote Desktop Services as described above.
RDP and TLS Encryption
If you have disabled the legacy Transport Layer Security (TLS) 1.0 and TLS 1.1 protocols on your RD host, this may cause an Internal error when attempting to establish an RD connection to an RDS farm with the Connection Broker. The reason for this problem is that the Windows Internal Database (WID), which is used by default on an RDCB host running Windows Server 2016/2012 R2, only supports TLS 1.0.
To solve the problem, you can:
- Use an external Microsoft SQL Server with TLS 1.2 support for the RD Connection Broker database.
- Or you need to enable the TLS 1.0 protocol on RDCB:
reg add "HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server" /v Enabled /t REG_DWORD /d 1 /f
Now check if your RDP client connects to the remote host without errors.











5 comments
This issue is so frustrating. I have it when attempting to connect to several different bare metal servers running Windows Server 2012 from a Windows 10 Pro machine. This HAS to be a bug because the way I fix it is to attempt to connect over and over and over until finally it just works. Sometimes it takes 2 tries, sometimes it takes 10 tries.
As Web Developer stated, current workaround is to retry connecting ~10 times, and it works…
This is SHITE advice polease dont follow this as non of these address the issue.
This is due to security protocol being used mismatch.
tls to be exact
what should i do to fix the issue?
I had this issue on two 2019 Windows servers. A simple server reboot resolved this issue for me. Thanks for the tips!