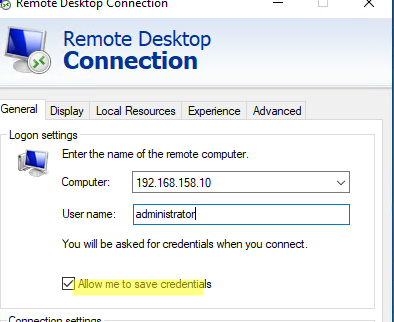
The built-in Microsoft Remote Desktop Connection client in Windows (mstsc.exe) allows you to save the user credentials that you use to connect to an RDP host. Just tick the ‘Allow me to save credentials‘ or ‘Remember me‘ option in the RD Connection client windows, click on ‘Connect’ and enter the user password. This password will be saved to the Windows Credentials Manager.
In some cases, this does not work, and each RDP connection requires a password to be entered. This article looks at how to allow Windows to save passwords for Remote Desktop connections.
Table of Contents
Your System Administrator Does Not Allow the Use of Saved Credentials
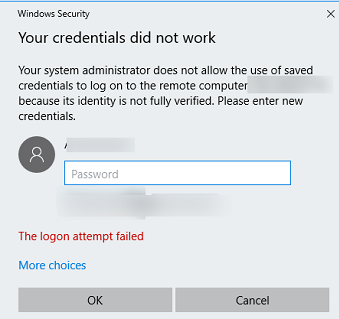
Windows 10/11 security policies may restrict the use of stored credentials to access the RDP/RDS host. In this case, when you try to connect with an RDP saved password, the Remote Desktop Client will show the following error:
Your Credentials did not work
Your system administrator does not allow the use of saved credentials to log on to the remote computer server_name because its identity is not fully verified. Please enter new credentials.
The logon attempt failed
Windows won’t allow you to use saved credentials to connect to a remote computer if the trust relationship between your computer and the remote computer is missing or broken. If the remote RDP host is in a workgroup or remote domain, you cannot save the connection password.
This is defined by the default Windows security policy settings. You can change this behavior with a GPO.
Allow Saved Credentials for RDP Connections with GPO
You can use the local Group Policy Editor to allow the use of saved RDP credentials on the current computer.
- Press Win + R and run the gpedit.msc command;
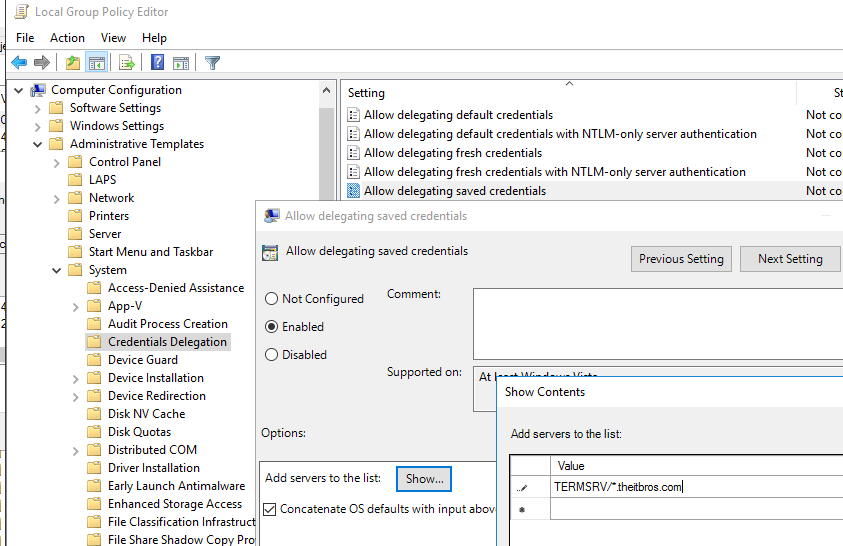
- Go to Local Computer Policy > Computer Configuration > Administrative Templates > System > Credentials Delegation;
- Enable the policy “Allow delegating saved credentials with NTLM-only server authentication” and then the Show button;
- Add the list of remote servers/computers for which you want to allow the use of saved RDP credentials:
When specifying the list of allowed remote hosts, use the following format:
1) TERMSRV/remote_pc — allow to save RDP credentials to access specific computer (you can use IP address, hostname, or wildcards);
2) TERMSRV/*.theitbros.com — allow using the saved credentials to access all hosts in the domain theitbros.com;
3) TERMSRV/* — allow use of saved RDP credentials for all computers without exception.Note. Use TERMSRV in uppercase. If you specify a specific computer, the remote_pc value must exactly match the name entered in the “Computer” field of the RDP client.
- Then enable the policy “Allow delegating saved credentials” in the same GPO section. Add the same TERMSRV/xxx values to the policy setting as mentioned above.
- Check that the following Group Policy options are disabled or not configured:
Deny delegating default credentials;
Deny delegating fresh credentials;
Deny delegating saved credentials.
- Press OK to save the changes and then close the Group Policy Editor.
- Update the Group Policy settings on your computer by running:
gpupdate /force
You should now be able to connect to Remote Desktop using your saved credentials.
Create a separate domain GPO with the above settings if you want to allow saved RDP credentials to be used on multiple domain computers. Use the Group Policy Management Console (GPMC.msc) to create and link the new GPO to the computers’ Organizational Unit (OU).
The Server’s Authentication Policy Does Not Allow Saved Credentials
In some cases, you may get the following error when try to use the saved RDP credentials:
Windows Security
Your credentials did not work
The server’s authentication policy does not allow connection requests using saved credentials. Please enter new credentials.
This error indicates that the remote host doesn’t allow the use of stored RD credentials to connect. In this case, change the GPO settings on the target RDP/RDS host as follows:
- Log on to the remote computer and open the gpedit.msc snap-in;
- Go Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Security;
- Disable the policy ‘Always prompt for password upon connection‘;
- Reboot the remote host.
Remote Desktop Services must always prompt a client for passwords during an RDP connection when this policy is enabled.
You can also change this parameter on the RDS host using the command:
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services" /v fPromptForPassword /t REG_DWORD /d 0 /f
Saved Credentials Didn’t Work in Remote Desktop Connection
In some cases, you will not be able to connect to remote hosts using the saved RDP credentials even after configuring the above Group Policy settings.
First, try deleting any previously saved credentials from Windows Credential Manager (Control Panel\All Control Panel Items\Credential Manager\Windows Credentials). Delete any the saved entries from the Windows Credentials and Generic Credentials lists.
You can then manually add your RDP credentials in Generic Credentials.
- Click the Add a generic credential link;
- Add the prefix “TERMSRV/” to the Internet or Network Address before your Remote Desktop host name or IP address;
- Set RDP user name and password;
- Click OK.
Also, you can add a credential to the Credential Manager from a command prompt using the built-in cmdkey tool:
cmdkey /generic:TERMSRV/sql01.theitbros.com /user:jbrown /pass:RDP_SupPassw0rd2 CMDKEY: Credential added successfully.
You can display information about the stored credentials for the specific host:
cmdkey /list:TERMSRV/sql01.theitbros.com
Currently stored credentials for TERMSRV/sql01.theitbros.com:
Target: termsrv/sql01.theitbros.com Type: Generic User: jbrown
Hint. Passwords in the Credential Manager are encrypted with the current user’s login password using the SHA algorithm.
Then you should check the following policies that might prevent Windows from saving passwords. Use the gpresult tool or rsop.msc to obtain the current GPO parameter settings on your computer.
- Network access: Do not allow storage of passwords and credentials for network authentication (Computer Configuration > Windows Settings > Security Settings > Local Policies > Security Options). This Windows Group Policy setting prevents Remote Desktop Credentials from being stored in Credential Manager and used for network authentication on the local system. In this case, an error will occur when you try to save the RDP credentials:
Unable to save credentials. To save credentials in this vault, check your computer configuration.
Error code: 0x80070520
Make sure this policy is disabled. This policy corresponds to the registry parameter DisableDomainCreds under the reg key HKLM\SYSTEM\CurrentControlSet\Control\Lsa\. Change its value from 1 to 0; - Deny delegation saved credentials (Computer Configuration > Administrative Templates > System > Credentials Delegation). Disable the policy. Check the value of the ConcatenateDefaults_DenySaved registry entry (HKLM\Software\Policies\Microsoft\Windows\CredentialsDelegation). Change the value to 0;
- Do not allow passwords to be saved (Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Connection Client). Disable the policy.
- Prompt for credentials on the client computer (Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Connection Client). Change the policy value to Not Configured or Disabled.
After upgrading to Windows 11 build 22H2, an error occurs when you try to use saved RDP credentials:
Windows Defender Credential Guard does not allow using saved credentials.
Starting with this build of Windows, Credential Guard will be enabled on any computer that meets the requirements (UEFI+Secure Boot+Virtualization-based security). Credential Guard protects against credential theft attacks by protecting NTLM password hashes, Kerberos Ticket Granting Tickets, and credentials stored by applications. As a result, the MSTSC client won’t able to access the stored RDP credentials in the Credential Manager.
You can disable Credential Guard using Group Policy:
- Enable the policy Turn on Virtualization Based Security in Computer Configuration > Administrative Templates > System > Device Guard;
- Select Disabled from the drop-down list in the Credential Guard Configuration option;
- Reboot computer;
- Now the Credential Guard will no longer block the RDP client from accessing the saved credentials.
If you use a PIN instead of a password to sign-in Windows, try deleting your current PIN.
Go to Settings > Accounts > Sign-in options (or run the following command: ms-settings:signinoptions). Select Windows Hello PIN and click Remove.
If you are using a pre-configured *.RDP file to connect to Remote Desktop or RemoteApp, open it with any text editor. Check the value of the following parameters. Change them as follows:
- Always use the saved Remote Desktop credentials for hosts you have previously saved: prompt for credentials:i:0
- When connecting through a Remote Desktop Gateway, use the same credentials for the RD Gateway and the remote computer:
promptcredentialonce:i:1
Hope this was useful!













4 comments
Thank you so much. This is the ultimate solution.
This is really great – so clear and concise. thanks a lot!
Getting error whn launching avd using RDC application :
Your Remote Desktop Services session has ended. possibly for one of the following reasons:
The administrator has ended the session
An error occurred while the connection was being established.
A network problem occurred.
This is a very well-written technical article and extremely thorough. Great work, and thanks for the help!