So you’ve deployed a new server, but your staff is complaining that they cannot access it remotely because of the following errors:
To sign in remotely, you need the right to sign in through Remote Desktop Services. By default, members of the Administrators group have this right, or if the right has been removed from the Administrators group, you need to be granted this right manually.
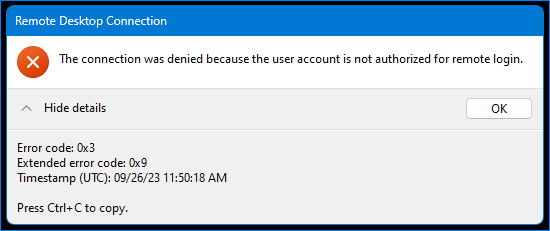
If the Network Level Authentication (NLA) is enabled on the remote machine, users will get this error instead:
The connection was denied because the user account is not authorized for remote login.
Both these errors clearly state the problem—The user is not authorized to log in to the Remote Desktop Services.
So who’s authorized to log in through Remote Desktop Services by default?
- The members of the Administrators and Remote Desktop Users groups on servers and workstations.
- The members of the Administrators group on domain controllers.
- If configured, the users or groups added to the Allow the log on through Remote Desktop Services user rights assignment policy in a Group Policy Object (GPO)
- User groups added to the Remote Desktop Services Collection.
This post will show how to allow individual users or group members the privilege to log in remotely on Windows computers.
Table of Contents
Adding Users to the Remote Desktop Users Group
Every server, workstation, and domain controller has a built-in group called Remote Desktop Users. The members of this group are allowed to log in to the computer through the Remote Desktop Services.
Related post. How to Enable Remote Desktop (RDP) Remotely?
Using the Local Users and Groups Console on Servers and Workstations
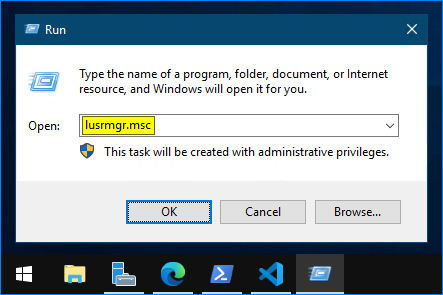
- Open the Local Users and Groups console by running this command:
lusrmgr.msc
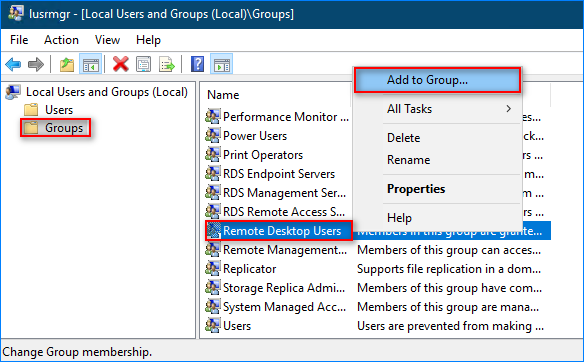
- Click Groups, right-click the “Remote Desktop Users” group, and click “Add to Group…”
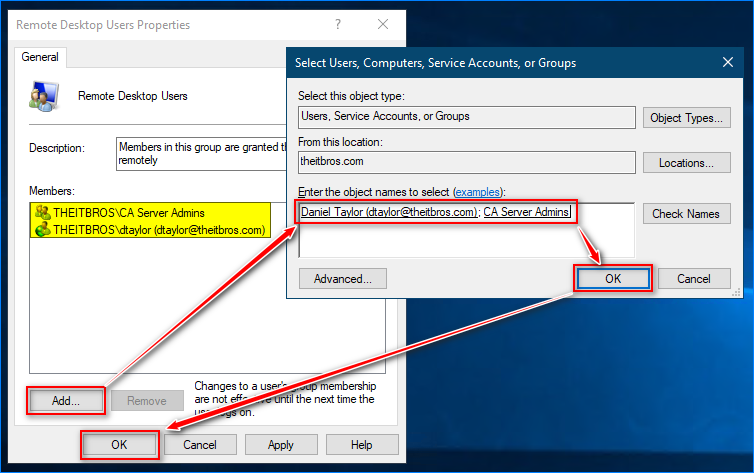
- Click Add, specify the users or groups to add as members, and click OK and OK.
Using the Add-LocalGroupMember PowerShell Cmdlet on Servers and Workstations
- Open an elevated PowerShell session (run as admin).
- Run this command to list the current members of the Remote Desktop Users group.
Get-LocalGroupMember -Group 'Remote Desktop Users'
The screenshot below shows that the Remote Desktop Users group is empty.
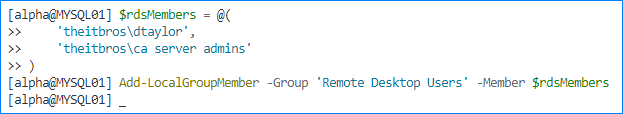
- Now, let’s put all users and groups to add as members in an array. In this example, I’m adding one group and one user:
$rdsMembers = @( 'theitbros\dtaylor', 'theitbros\ca server admins' )
- Run the Add-LocalGroupMember cmdlet to add the $rdsMembers to the Remote Desktop Users group.
Add-LocalGroupMember -Group 'Remote Desktop Users' -Member $rdsMembers
This command does not return anything on the screen, which means the operation is successful.
- Lastly, confirm that the new members are added to the Remote Desktop Users group.
Get-LocalGroupMember -Group 'Remote Desktop Users'
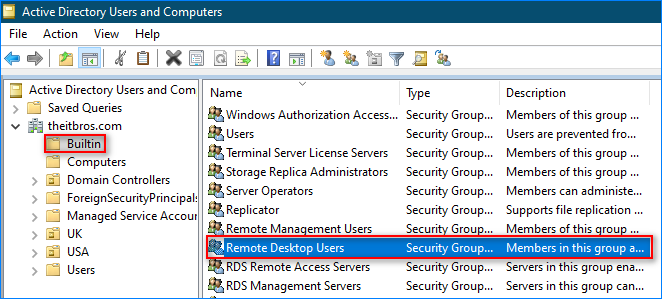
Using the Active Directory Users and Computers on Domain Controllers
- On the domain controller, open the Active Directory Users and Computers console by running the dsa.msc command.
Related post. Installing Active Directory Users and Computers Snap-in (ADUC) on Windows 11/10 - Select the “Builtin” container and double-click the “Remote Desktop Users” group.
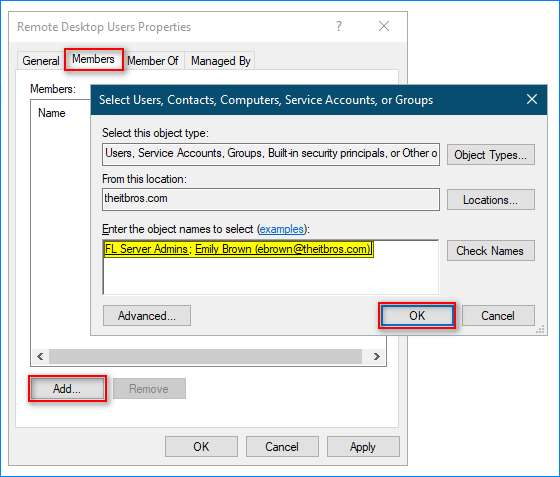
- Switch to the Members tab, click Add, specify the groups and users to add, and click OK.
- Once the users and groups are added, click OK.
Using the Add-ADGroupMember PowerShell Cmdlet on Domain Controllers
- Open PowerShell on the domain controller.
- Import the Active Directory PowerShell module:
Import-Module ActiveDirectory
Related. How to Install and Import PowerShell Active Directory Module?
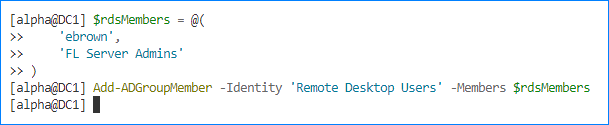
- Run the following commands to add new members to the Remote Desktop Users group. Replace the values in the $rdsMembers array with your groups and users.
$rdsMembers = @( 'ebrown', 'FL Server Admins' )Add-ADGroupMember -Identity 'Remote Desktop Users' -Members $rdsMembers
- Confirm the new members by listing them:
Get-ADGroupMember -Identity 'Remote Desktop Users'
Granting Allow Log On Through Remote Desktop Services via GPO
For more centralized management, you can also allow users to connect to Remote Desktop Services using the Allow Log On Through Remote Desktop Services policy.
Related post. Managing “Logon As a Service” Permissions Using Group Policy or PowerShell
Configure the Allow Log On Through Remote Desktop Services Policy
- Run the gpedit.msc command on the domain controller.
- Edit an existing GPO or create a new one. In this example, we’ll edit the Default Domain Policy and Default Domain Controllers Policy.
- Navigate to Computer Configuration → Policies → Windows Settings → Security Settings → Local policies → User Rights Assignment.
- Double-click the “Allow log on through Remote Desktop Services” policy.
- Check the “Define these policy settings” box, click “Add User or Group…”, specify the users and groups to add, and click OK.
- Ensure that the “Deny log on through Remote Desktop Services” policy does not contain the same users or groups because this policy takes precedence.
Confirm the Policy Results
- Log in to a server or workstation.
- Open a CMD or PowerShell window.
- Run the gpupdate /force command to force the policy update.
- Run a group policy result HTML report:
GPResult /h gp_report.html /f
- Once the report is done, open it and confirm that the “Allow log on through Terminal Services” policy is configured.
On domain controllers, the policy result will look like this:
Allowing Users and Groups to the Remote Desktop Services Collection
If you’re logging in remotely to a Windows Server that’s part of a Remote Desktop Services Collection, you may get the following error, and your log-in fails.
This could happen if your user account or group is not listed in the RDS collection, and here’s how to fix this.
Using the Remote Desktop Services in Server Manager (GUI)
- Open the Server Manager on another server that lets you log in.
- Right-click on Servers and click Add Servers.
- Add your RDS servers and click OK.
- Click Remote Desktop Services, select the RDS collection, and click Tasks → Edit Properties.
- Click Add, specify the users or groups to allow, and click OK and OK.
Using the PowerShell RemoteDesktop Module
- Open PowerShell and run the following command to retrieve the RDS collection names.
# If running on the server with an RDS role Get-RDSessionCollection# If running on the server without an RDS role Get-RDSessionCollection -ConnectionBroker <RDS Server FQDN>
In this example, there is only one RDS Collection.
- Next, back up the current users and groups who are allowed to RDP into the RDS collection.
$rdsUserGroup = Get-RDSessionCollectionConfiguration -CollectionName <RDS Collection Name> -ConnectionBroker <RDS Server FQDN> -UserGroup $rdsUserGroup.UserGroup
As you can see, this RDS collection has two entries in the UserGroup property.
- Next, let’s combine the new and current user and group lists. In this example, we’re adding three new entries.
$newRdsUserGroup = $rdsUserGroup.UserGroup + @( "THEITBROS\FL Server Admins", "THEITBROS\LND Server Admins", "THEITBROS\janderson" )
- To add new users and groups who will be allowed to RDP into the RDS collection, run this command. Make sure to replace the collection name and specify the correct users and groups.
Set-RDSessionCollectionConfiguration -CollectionName "<RDS Collection Name>" -UserGroup $newRdsUserGroup -ConnectionBroker "<RDS Server FQDN>"
The command does not return any result if the operation is successful.
- Re-run the commands in Step 2 to list the new RDS collection users and groups.
Disabling Enhanced Session Mode on Hyper-V Virtual Machines
Suppose you’re getting the “To sign in remotely, you need the right to sign in through Remote Desktop Services” error when connecting to a VM inside the Hyper-V Manager, you can use the previous methods in this post to troubleshoot.
This situation doesn’t happen if you’re connecting to the VM using the native Hyper-V bus. But when the Enhanced Session Mode is enabled, the VM’s connection is made through the Remote Desktop Services instead.
- Connecting via Basic Mode = Using the native Hyper-V bus.
- Connecting via Enhanced Session Mode = Using the Remote Desktop Services.
To disable the Enhanced Session Mode, click View and uncheck the Enhanced Session menu item.
Or click the Basic Session toolbar button.
And once you’re logged in, you can perform the previous methods we discussed in this post. Once you’ve remedied the source of the “To sign in remotely, you need the right to sign in through Remote Desktop Services” error, it’s up to you to re-enable the Enhanced Session Mode or not.
Conclusion
We’ve learned the different ways to solve the “To sign in remotely, you need the right to sign in through Remote Desktop Services” error when remotely accessing Windows computers via RDP.
This post doesn’t aim to cover every possible cause of the error. Rather, provides you with the usual starting points for troubleshooting.












 On domain controllers, the policy result will look like this:
On domain controllers, the policy result will look like this:











