Remote Desktop Protocol (RDP) is a popular, simple, and convenient way to connect to remote Windows computers. Thanks to RDP, you get full access to the graphical desktop environment of a remote computer and work with it just as if it was your own local device. By default, Remote Desktop is disabled on both desktop versions of Windows and Windows Server. In this article, we will look at several ways to enable RDP in Windows.
Table of Contents
Enable and Disable Remote Desktop Locally
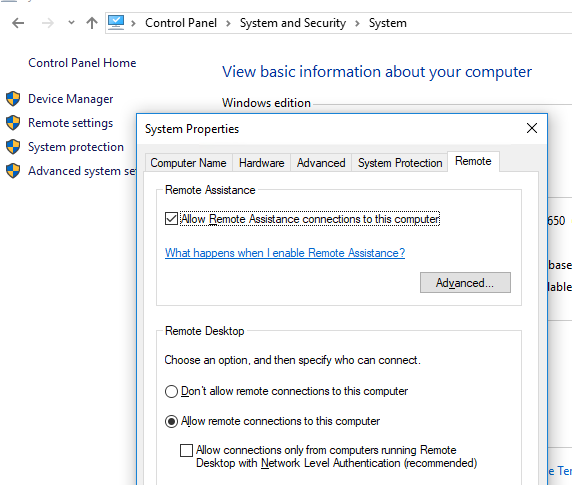
The most intuitive way to enable Remote Desktop on Windows 10 and 11 is to use a GUI. You can enable RDP:
- From the classic SystemPropertiesRemote control panel: run the command SystemPropertiesRemote and enable the Allow remote connections to this computer option in the Remote Desktop section;
- From the modern Settings panel: run the ms-settings:remotedesktop command and toggle the option “Remote Desktop”:
However, this requires local access to the computer on which you want to enable RDP. You can usually ask the user for this (local administrator permissions required), or local technical support. However, what to do if no one in the remote branch office could enable the Remote Desktop locally?
Let’s look at several ways that allow you to remotely enable Remote Desktop (RDP) on a remote host (server or computer),
Enable RDP Using Remote Registry
You can enable Remote Desktop on a remote computer using Registry Editor. This requires:
- The remote computer must be accessible over the network;
- You must know the credentials of an account with local administrator permissions on the remote computer;
- The Remote Registry service must be running on the remote computer (you can enable it through the services.msc snap-in, GPO, or with the command sc \\RemotePCName start RemoteRegistry).
So, to enable the remote desktop via remote registry, follow these steps:
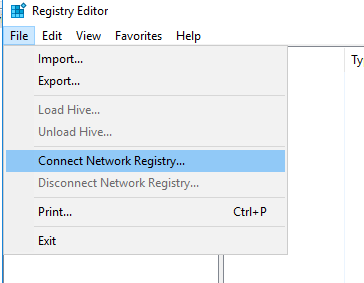
- Press the Win + R key combination, type regedit.exe > OK;
- In the Registry Editor select File > Connect Network Registry;
- Specify the hostname or IP address of the remote computer. If the remote computer could not authorize you as the current user, you will be prompted to enter credentials;
- The registry of the remote computer will appear in the registry editor (only HKLM and HKEY_Users hives are accessible);
- Go to the following reg key on the remote computer: HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server. Change the value of the fDenyTSConnections parameter (Type=REG_DWORD) from 1 to 0;
- If a firewall is enabled on the remote computer, you must enable the rule that allows remote desktop connections. You can enable it via GPO, via PowerShell Remoting, or using Psexec (check the next sections of this guide).
How to Enable RDP Remotely Using PsExec Tool?
You can use the PsExec cmd tool to enable Remote Desktop on a remote Windows device.
Download the PsExec toolkit from the Microsoft website and extract the PSTools.zip archive to a local folder.
Open a command prompt as an administrator and go to the PSTools directory:
CD c:\PS\PStools
In order to enable RDP on a remote computer in your domain using PSExec, run the command:
PsExec.exe /accepteula \\RemoteComputerName_or_IP reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
Then enable the rule to access the RDP port in Windows Defender Firewall:
PsExec.exe /accepteula \\RemoteComputerName_or_IP netsh advfirewall firewall set rule group="remote desktop" new enable=Yes
If the remote computer is in a different domain or workgroup, you can provide a username with administrator permissions to connect to the remote computer:
PsExec.exe /accepteula \\RemoteComputerName_or_IP -u administrator reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server" /v fDenyTSConnections /t REG_DWORD /d 0 /f
Then allow inbound connections to the RDP port (3389/TCP):
PsExec.exe /accepteula \\RemoteComputerName_or_IP -u administrator netsh advfirewall firewall set rule group="remote desktop" new enable=Yes
Now try to connect to the remote computer via RDP.
Enable Remote Desktop Remotely Using PowerShell
To enable RDP remotely, you need to configure and run the WinRM service (Windows Remote Management) on the remote computer. The WinRM service is enabled by default in all versions of Windows Server starting with Windows Server 2012. However, WinRM is disabled by default in client operating systems such as Windows 10 or 11.
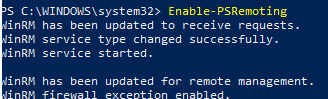
You can enable WinRM on domain-joined computers using GPO or locally using PowerShell. The easiest way to locally enable the WinRM service on Windows 10/11 and allow access via PowerShell Remoting is using the command:
Enable-PSRemoting
WinRM has been updated to receive requests.
WinRM service type changed successfully.
WinRM service started.
Next, you need to check if WinRM is enabled on the remote computer and if PSRemoting connections are allowed. Run the command:
Test-WsMan 192.168.31.102
If the WinRM service on the remote computer responds, you will receive this response:
If the service is disabled or access is blocked by Windows Defender Firewall, an error will appear:
Test-WsMan WSManFault: WinRM cannot complete the operation. Verify that the specified computer name is valid, that the computer is accessible over the network, and that a firewall exception for the WinRM service is enabled and allows access from this computer. By default, the WinRM firewall exception for public profiles limits access to remote computers within the same local subnet.
Thus, to enable Remote Desktop remotely via PowerShell, the remote computer must meet the following requirements:
- The WinRM service should be started;
- You must have administrator permissions on the remote device;
- Windows Defender Firewall with Advanced Security rules must accept PowerShell Remoting on WinRM ports TCP 5985 and 5986. You can enable the WinRM firewall rules with the command:
netsh advfirewall firewall set rule group=”Windows Remote Management” new enable=yes)
Suppose you want to remotely enable RDP on Windows Server 2022/2019/2016/2012R2. Open the PowerShell console on your computer and run the following command to connect to your server remotely:
Enter-PSSession -ComputerName server.domain.local -Credential domainadministrator
Tip. The Enter-PSSession and Invoke-Command cmdlets allow you to run PowerShell script on remote computer through WinRM.
So, you have established a remote session with a computer and now you can run PowerShell commands against it. To enable Remote Desktop, you just need to change the registry parameter fDenyTSConnections from 1 to 0. Run the command:
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server'-name "fDenyTSConnections" -Value 0
When RDP is enabled in this way (as opposed to the GUI method), you need to enable Windows Firewall rules for Remote Desktop manually. Run the command:
Enable-NetFirewallRule -DisplayGroup "Remote Desktop"
If for some reason this RDP firewall rule is missing, you can create it manually using netsh:
netsh advfirewall firewall add rule name="allow RemoteDesktop" dir=in protocol=TCP localport=3389 action=allow
or using Powershell:
New-NetFirewallRule -DisplayName 'Allow RemoteDesktop' -Profile @('Domain', 'Private') -Direction Inbound -Action Allow -Protocol TCP -LocalPort @('3389')
If you want to restrict hosts or subnets that are allowed to connect to Remote Desktop, you can create a custom rule that allows Windows Firewall to only accept incoming RDP connections from specific IP addresses, subnets, or IP ranges. In this case, instead of the previous command, you need to use the following one:
New-NetFirewallRule -DisplayName “Restrict_RDP_access" -Direction Inbound -Protocol TCP -LocalPort 3389 -RemoteAddress 192.168.1.0/24,192.168.2.100 -Action Allow
If you need to enable secure RDP authentication (NLA – Network Level Authentication), run the command:
Set-ItemProperty -Path 'HKLM:\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp' -name "UserAuthentication" -Value 1
Now you can check the availability of TCP port 3389 on the remote host from your computer. Run the command:
Test-NetConnection 192.168.1.11 -CommonTCPPort rdp
There should be a result like this:
ComputerName : 192.168.1.11 RemoteAddress : 192.168.1.11 RemotePort : 3389 InterfaceAlias : Ethernet0 SourceAddress : 192.168.1.90 TcpTestSucceeded : True
This means that RDP on the remote host is enabled and you can establish a remote desktop connection using mstsc.exe, RDCMan, or any alternative RDP client.
Hint. If you need to enable RDP on several remote computers at once, you can use the following PowerShell script:
$comps = “Server1”, “Server2”, “Server3”, “Server4” Invoke-Command –Computername $comps –ScriptBlock {Set-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Terminal Server" -Name "fDenyTSConnections" –Value 0} Invoke-Command –Computername $comps –ScriptBlock {Enable-NetFirewallRule -DisplayGroup "Remote Desktop"}
By default, only members of the local Administrators group can connect via the RDP remotely. To allow RDP connections for non-admin users, just add domain user to Remote Desktop Group.
You can add the desired users to the Remote Desktop Users locally by using the Local Users and Groups MMC snap-in (LUSRMGR.MSC).
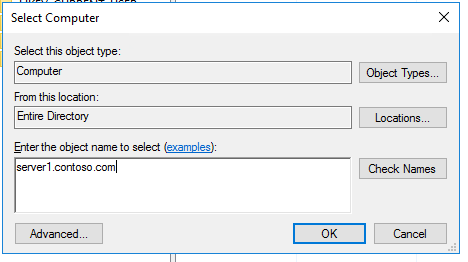
Or you can change RD Users group membership remotely using the Enter-PSSession. Use the following command to add the domain user ASmith to the local group:
net localgroup "remote desktop users" /add "contoso\asmith”
Alternatively, instead of the Enter-PSSession cmdlet, you can use another PS Remoting command Invoke-Command:
Invoke-Command -Scriptblock {net localgroup "remote desktop users" /add "contoso\asmith”} -Computer Server1.contoso.com
How to Check if Remote Desktop is Enabled on Remote Computers with PowerShell?
Consider a PowerShell script that allows you to remotely get the RDP status on multiple computers in your network. Set a variable that contains a list of remote computers on which you want to check if Remote Desktop is enabled:
$comps=’wks101’,’wks102’,’wks112’, ‘wks223’
You can also check if RDP is enabled on all computers in the Active Directory domain. To get a list of active computers in AD, you can use the Get-ADComputer cmdlet from the PowerShell Active Directory module:
$comps = (Get-ADComputer -Filter 'operatingsystem -like "*Windows 10*" -and enabled -eq "true"').Name
Now you need to get the status of the fDenyTSConnections registry parameter on the remote computers in your list.
$Report = @()
$comps ='localhost','localhost'
foreach ($comp in $comps) {
$RDPRegistry = Invoke-Command $comp -ScriptBlock { (Get-ItemProperty 'HKLM:SYSTEM\CurrentControlSet\Control\Terminal Server').fDenyTSConnections } -ErrorAction SilentlyContinue
$RDPState = switch ($RDPRegistry)
{
'0' {"Enabled"}
'1' {"Disabled"}
Default {"n/a"}
}
$objReport = [PSCustomObject]@{
ComputerName = $comp
RDPState = $RDPState
}
$Report += $objReport
}
$Report
As a result, you have a cool report that shows which computers on the network have Remote Desktop enabled.
How to Enable Remote Desktop via WMI?
If you want to enable RDP on a remote computer where WinRM is disabled, you can use the WMI PowerShell command.
Tip. To access the WMI namespace on the remote computer, TCP port 135 must be open, and the account must have WMI and DCOM access permissions.
To check if RDP access is enabled on the remote computer 192.168.1.90, run the command (see the value of the AllowTSConnections property):
Get-WmiObject -Class Win32_TerminalServiceSetting -Namespace root\CIMV2\TerminalServices -Computer 192.168.1.90 -Authentication 6
To enable RDP and add a Windows Firewall exception rule, run the following command:
(Get-WmiObject -Class Win32_TerminalServiceSetting -Namespace root\CIMV2\TerminalServices -Computer 192.168.1.90 -Authentication 6).SetAllowTSConnections(1,1)












4 comments
Fantastic! Registry edit worked perfectly!
The command to enable Remote Desktop using WMI is truncated. Please provide the full command.
Hi, looks like you forgot to add the commands at the very end.
(Get-WmiObject -Class Win32_TerminalServiceSetting -Namespace root\CIMV2\TerminalService … (?)
The last option (WMI) worked for me whereas the other did not due to my system’s config. Thank you very much!!