Local security settings in Windows let you to allow or deny local (interactive) logon for users on computers. In this article, we’ll take a look on how to manage local logon permissions on Windows 10 and Windows Server 2019.
By default, Windows 10 and Windows Server 2019 allow to log on locally users who are members of the following local Active Directory groups:
- Administrators;
- Backup Operators;
- Users.
If the server is promoted to an Active Directory domain controller, then the list of groups with local logon permissions is changed. The user is not allowed to log on to the AD domain controller console:
- Account Operators;
- Administrators;
- Backup Operators;
- Print Operators;
- Server Operators.
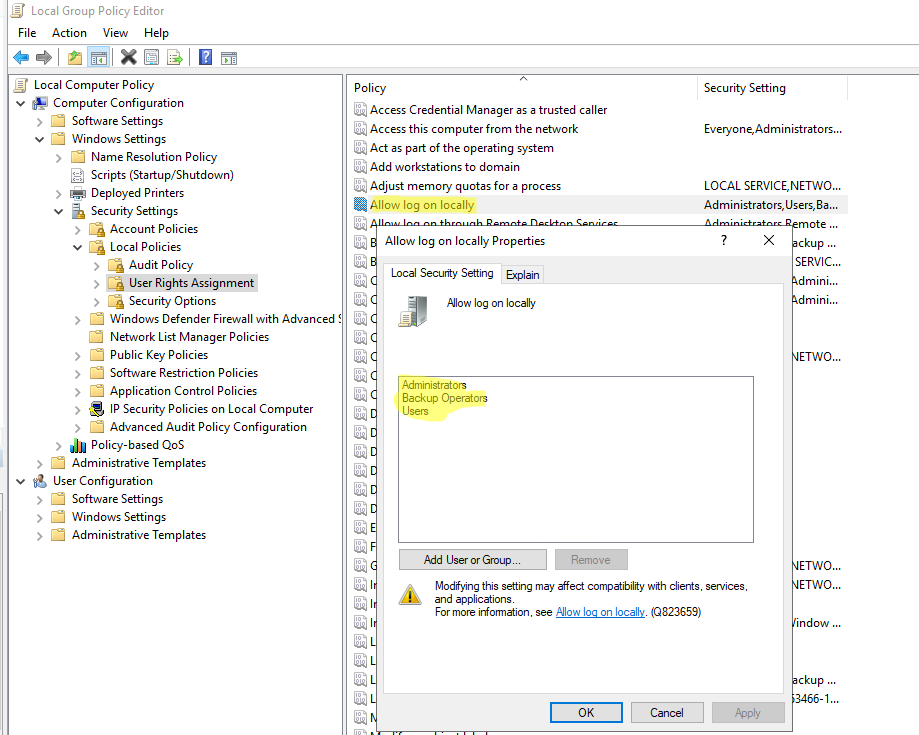
You can view the current list of groups with local logon permissions through the local Group Policy.
- Run the Local Group Policy Editor (gpedit.msc);
- Go to the GPO following section Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment;
- Find the Allow log on locally parameter and open its settings;
With this policy, you can add or remove user groups (or personal user accounts) that are allowed to log on locally. For example, if you remove the local Users group from this policy, then your users will not be allowed to log in interactively to this device.
Hint. However, users can still log on remotely through Remote Desktop Services if this group is added to the local policy Allow logon through Remote Desktop Services in the same GPO section.
After changing the policy settings, it is not necessary to reboot the computer. Changes to user rights assignment of accounts will be applied the user logs on Windows.
In the same section of the GPO, there is another Deny log on locally policy, which allows you to forcibly deny interactive logons to users. It is empty by default. You can manually add users or groups to this policy that are not allowed to log on to this computer interactively. Note that the Deny log on locally policy has a higher priority than the Allow log on locally policy.
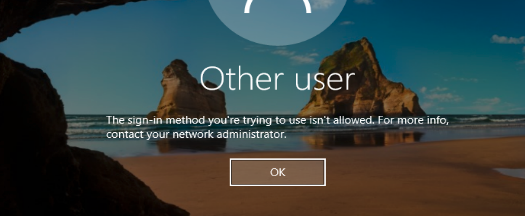
If the user does not have the permissions to log on locally, then when he logs on to the computer after entering the password, the following message will appear:
The sign in method you’re trying to use isn’t allowed. For more info, contact your network administrator.
Always try to configure login policies so that only legitimate users can log on the device console. For security reasons, prevent service accounts from logging on to computers in your organization locally.


1 comment
If you have DUO installed, this will block autologin.