A Windows computer’s time must be in sync with the domain in order to function properly in an Active Directory. This is especially important for Kerberos authentication to work. Windows constantly synchronizes the time with the NTP servers. Domain controllers act as NTP servers for the computers that join the Active Directory domain.
On a Windows computer that is not part of an Active Directory domain, the computer’s time is synchronized with one of two Internet time sources by default:
- time.windows.com
- time.nist.gov
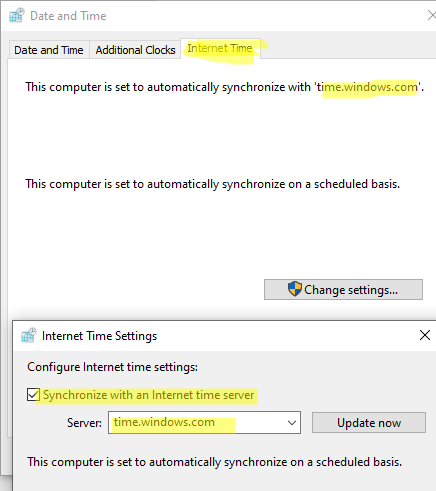
You can find the list of internet servers with which your computer synchronizes time by using the Control Panel > Date and Time > Internet time tab > Change Settings. As you can see this computer is set to automatically synchronize with ‘time.windows.com’ and the Synchronize with an Internet time server option is enabled.
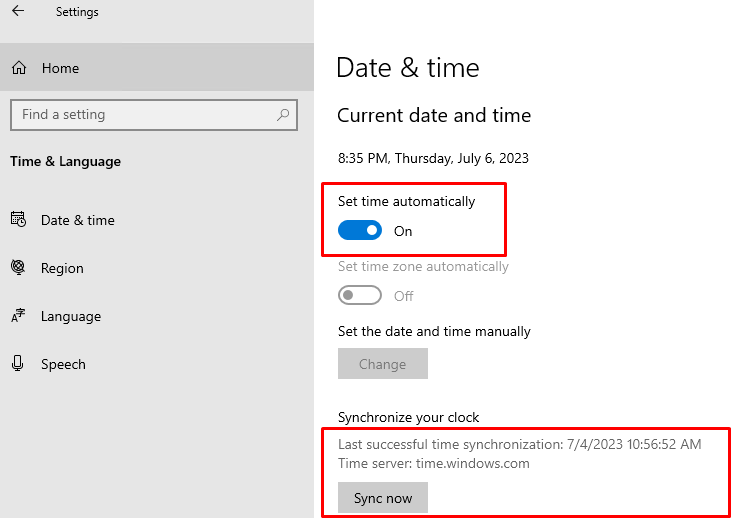
You can also check the time sync settings via the modern Settings app. Navigate to Settings > Time and Language (or run the ms-settings:dateandtime command). Check that the Set time automatically option is enabled.
It also shows the date of the last successful synchronization and the current time server FQDN.
To synchronize the time immediately, click the Sync Now button.
The list of Internet time servers that are currently in use is stored in the Windows registry under the HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\DateTime\Servers key.
Time synchronization works differently on computers that are joined an Active Directory domain.
Features of time synchronization in Active Directory domains:
- All domain computers and servers must use the NT5DS domain time;
- Domain workstations and Windows member servers synchronize their time with the domain controller closest to them;
- Domain controllers synchronize their time with the domain controller that owns the PDC emulator FSMO role;
- The PDC emulator in the child domain must synchronize time with any domain controller in the parent AD domain;
- The PDC emulator in the parent domain must synchronize time with an external NTP source.
If you go to Settings > Time and Language after you have joined the domain, you will see that the AD domain controller is used as the time source. And you can’t change the time source from the GUI.
Hint. Learn more about time syncing in an Active Directory domain using the GPO.
The Windows Time Service (W32Time) is responsible for time synchronization. First of all, make sure this service is running on a Windows client computer using Get-Service cmdlet:
Get-Service W32Time | Select-Object name,status
You can check with which NTP server (NTP source) if your computer is currently synchronizing the time by using the command:
w32tm /query /source
More information on the status of time synchronization on the client device:
w32tm /query /status
In an AD domain, you can list the domain controllers with which time synchronization can be performed:
w32tm /monitor
In this example, there are three domain controllers available for the client to synchronize time with.
For computers in an Active Directory domain, you can use the following commands to enable time synchronization with a DC:
w32tm /config /syncfromflags:domhier /update
net stop w32time && net start w32time
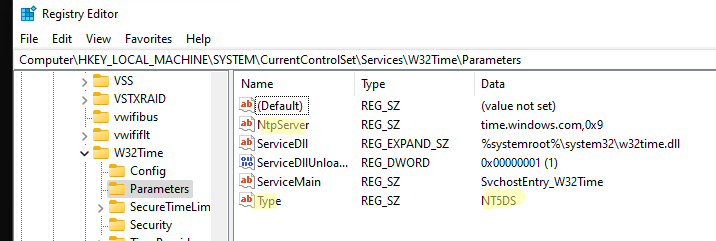
The Windows Time service parameters are stored under the HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Parameters registry key. The synchronization mode is set using the Type parameter. If you change the Type value to NoSync, you completely disable time synchronization in Windows.
Table of Contents
Windows Time Synchronization in an Active Directory Domain
On all computers joined to the Active Directory domain the closest domain controller is used as the default time source. In this case, the Type parameter must be set to NT5DS. If NTP is specified here, then your computer synchronizes time with an external time source (possibly on the Internet). In this case, the external time source for your computer (NTP server) will be specified in the NtpServer registry parameter.
You must set the Type parameter to NT5DS to enable automatic time synchronization of a Windows client with a domain controller.
When the NT5DS time synchronization type is used, the time source specified in the NtpServer parameter is ignored and Windows synchronizes the time with the domain controller (in accordance with the Active Directory sites and subnets).
You can manually change this parameter by using the Registry Editor (regedit.exe) or with PowerShell:
Set-ItemProperty HKLM:\SYSTEM\CurrentControlSet\services\W32Time\Parameters -Name "Type" -Value "NT5DS"
Restart Windows Times service:
Restart-Service -Name w32time
If the Windows client fails to synchronize time with the AD domain controller, you must to reset the Windows Time service configuration. To do this, open a command prompt as an administrator and run the following commands:
- The first command unregisters the w32time service and removes the settings from the registry:
w32tm /unregister
- Then register w32tm service and restore the default time settings:
w32tm /register
- Restart the service:
net stop w32time && net start w32time
- Update settings:
w32tm /config /update
- Synchronize the time:
w32tm /resync
- Check your current sync settings:
w32tm /query /status
The screenshot below shows that Windows is now synchronizing with DC (Source).
Time Sync Issues on Windows Domain Joined Computers
UDP port 123 is used for time synchronization on Windows. If this port is not available on the DC, the client computer won’t be able to synchronize the time.
You may get an error when you try to synchronize the time with the w32tm /resync command:
Sending resync command to local computer
The computer did not resync because no time data was available.
In this case you need to check that the w32time service is running on the domain controller:
Get-Service w32time
The w32time service should listen on UDP port 123. Check that this port is listening on the DC.
netstat -an | find "UDP" | find ":123"
If the w32time service is running and listening on port 123, check the Windows Defender firewall rules. Go to Control Panel > Windows Firewall > Advanced settings > Inbound rules.
Check that the Active Directory Domain Controller – W32Time (NTP-UDP-In) rule is enabled.
You can also check Windows Defender Firewall rule status with PowerShell:
Get-NetFirewallrule -DisplayName 'Active Directory Domain Controller - W32Time (NTP-UDP-In)'|select Enabled
If the rule is disabled, you must enable it:
Get-NetFirewallrule -DisplayName 'Active Directory Domain Controller - W32Time (NTP-UDP-In)'|Enable-NetFirewallrule
If the rule is missing (accidentally deleted), create a new rule allowing clients to connect to the Windows Time service on a domain controller:
netsh advfirewall firewall add rule name="NTP Server" dir=out protocol=udp localport=123 profile=any enable=yes action=allow
netsh advfirewall firewall add rule name="NTP Server" dir=in protocol=udp localport=123 profile=any enable=yes action=allow
You can also force a manual time sync with another domain controller. Use the command:
net time \\ny-dc01 /set /y
This command should return “The command completed successfully.”
Configuring NTP Client on Windows Using GPO
In most cases, time sync with a domain in Windows client doesn’t require any administrator intervention. However, if you find that time synchronization is not working properly on clients in your domain, you can centrally configure client NTP settings on Windows devices using Group Policy.
- Use the gpedit.msc console if you want to change Group Policy settings on a single computer (this is the best solution if you need to solve synchronization problems on a single computer or test new NTP client settings). If you are setting up a GPO for multiple computers in a domain, use the Group Policy Management Console (gpmc.msc);
- Expand the following node in the left pane of the GPO editor Computer Configuration > Administrative Templates > System > Windows Time Service;
- Open the Enable Windows NTP Client policy in the right pane and enable it;
- Then select the Configure NTP Client option. Change its state to Enabled;
- You need to set the following settings in the Options panel:
NTPServer: your domain name (preferred) or FQDN name of the domain controller with the PDC Emulator role (you can find it with the command: netdom.exe query fsmo)
Type: NT5DS
CrossSiteSyncFlags: 2
ResolvePeerBackoffMinutes: 15
ResolvePeerBackoffMaxTimes: 7
SpecialPollInterval: 64
EventLogFlags: 0 - Restart your computer to apply the new GPO client time settings.