The Delegation Control feature in Active Directory allows you to grant non-admin users the permissions to perform some administrative actions. For example, it can be used to allow the support team to create users in AD and reset passwords without having to grant them the domain admin rights.
Permissions delegation in AD is based on the concept of Organizational Units. In most cases, rather than delegating permissions to a specific AD object (such as a user or computer), permissions are delegated to the entire OU.
Before delegating Active Directory permissions, you must create the correct organizational structure in your directory. For example, if your company has a number of branch offices in different states and cities, you may want to create the following OU structure.
We have created separate OUs under each of the cities, to which you can delegate permissions:
- Admins
- Computers
- Groups
- Users
Now let’s delegate to the CA support group the permissions to reset passwords and unlock user accounts in the OU=Users,OU=LosAngeles,OU=California,DC=theitbros,DC=com. It is assumed that technical support team users have already been added to the CA_Tech_Support security group.
- Open the Active Directory Users and Computers snap-in (ADUC);
- Right-click on the OU you want to delegate permissions to (in our example this is the Users OU) and select Delegate Control;
- The graphical Delegation of Control Wizard will start;
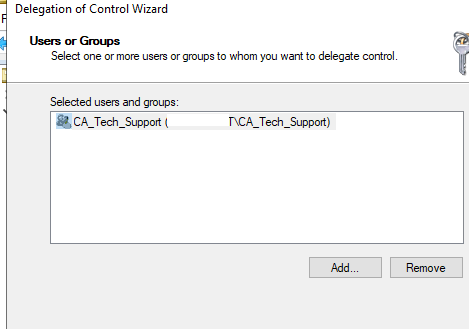
- Select the user group you want to grant privileges to (Add > CA_Tech_Support);
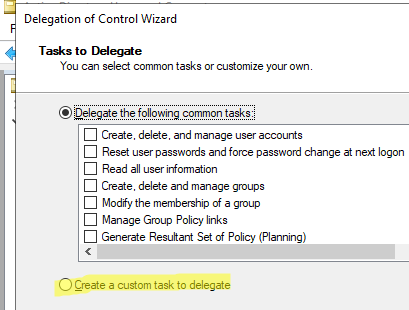
- Next, you need to select which actions you want to delegate. A list of common tasks is available here. However, none of them are suitable for our case. Therefore, you need to select Create a custom task to delegate here;
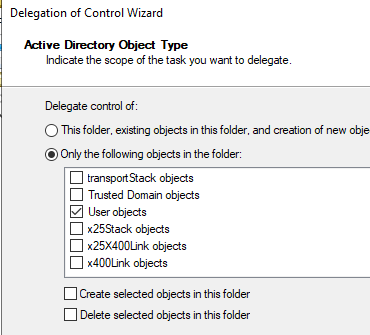
- In the next window, select the Only the following objects in the folder option and check User objects item;
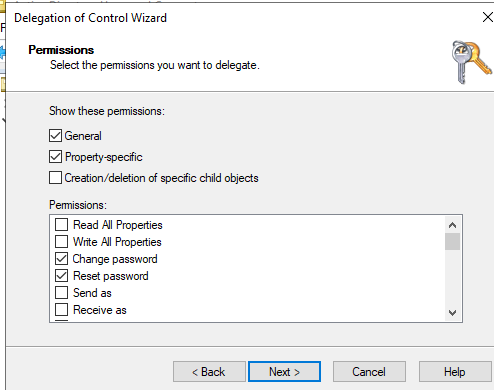
- Then select the following options in the permissions list:
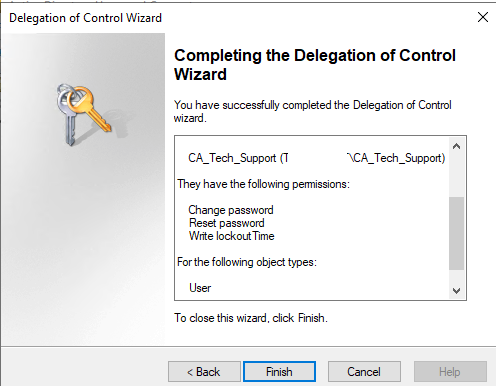
Change password
Reset password
Write lockoutTime
- Click Next. In the final window, you can view the list of objects and permissions you want to delegate. Click Finish.
Users in the CA_Tech_Support group can now unlock user accounts in the LosAngeles OU if they are locked by the domain account lockout policy.
To unlock the user account in Active Directory, use the Accounts tab in the user’s properties in ADUC or PowerShell command:
Unlock-ADAccount a.jackson –Confirm
To view the resulting list of permissions you have delegated to an OU:
- Open OU Properties and go to the Security > Advanced tab.
- Find your technical support group in the list > Edit;
- The type of AD objects to which permissions are delegated is displayed in the Applies to;
- The assigned permissions are displayed in the Permissions and Properties lists.
If you need to revoke the delegation, simply remove the security group from the Organizational Unit ACL.
You can also delegate other rights in AD. For example:
- Permission to move AD objects to a different OU;
- Right to add and remove users from security groups;
- Permission to join computers to domain;
- Group policy link management permissions;
- etc.