A lockout policy that automatically disables user accounts after a certain number of failed logon attempts is applied to all Active Directory users. This article shows how to find and unlock the AD account of a user or all locked AD domain users at once.
The user’s account in Active Directory will be locked if the user try to enter an incorrect password several times in a row. In this case, the Windows login screen will display a message after the password is entered:
The referenced account is currently locked out and may not be logged on to.
After multiple failed logins, the user account will be locked for a period of time. The Account Lockout Policy in Active Directory sets the number of failed logon attempts and the lockout time.
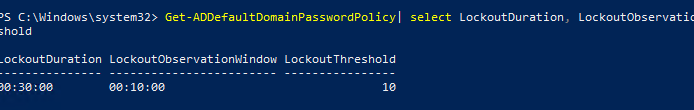
To quickly find the account lockout settings in the Default Domain Policy, you can use PowerShell:
Get-ADDefaultDomainPasswordPolicy| select LockoutDuration, LockoutObservationWindow, LockoutThreshold
In this example, the account will be locked for 30 minutes (LockoutDuration) after 10 failed login attempts (LockoutThreshold).
Active Directory will unlock the account and the user will be able to log on to the domain when the LockoutDuration time has expired.
Note. A LockoutDuration value of 0 means accounts in your domain are never automatically unlocked. The lock can only be removed manually by the domain administrator.
If the Fine-Grained Password Policy with custom account lockout settings is enabled for the user, you can check the resulting lockout policy settings for the target user with the command:
Get-ADUserResultantPasswordPolicy -Identity j.brion | select-object LockoutDuration, LockoutObservationWindow, LockoutThreshold
Note. You can track user lockout events on the domain controller running the PDC Emulator FSMO role by the EventID 4740. For more information about finding the source of user lockouts in AD, see the article at the link.
Table of Contents
Unlock a Domain User Accounts with GUI
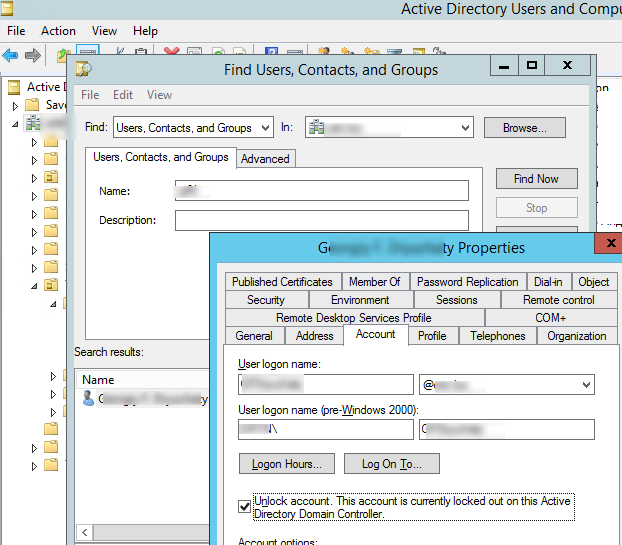
The domain administrator can unlock the user’s account immediately, so they don’t have to wait 30 minutes. You can unlock a user account using the Active Directory Users and Computers snap-in (ADUC).
- Open the dsa.msc console;
- Find the user object in the AD and open its properties;
- Go to the Account tab, check the option “Unlock account. This account is currently locked out on this Active Directory Domain Controller” and press OK.
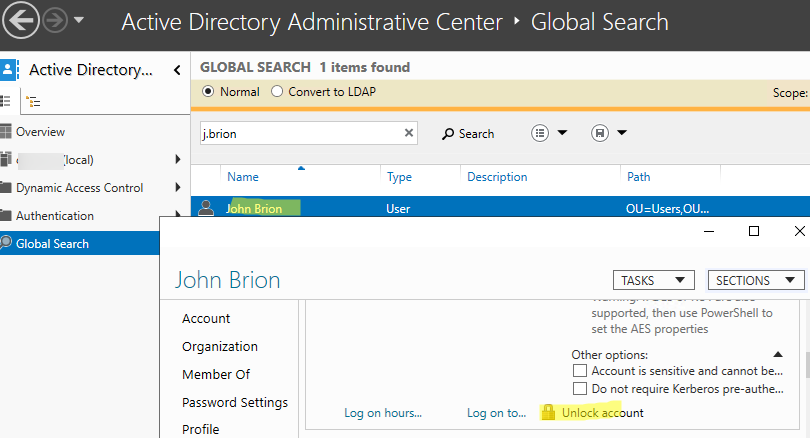
You can also use the Active Directory Administrative Center (ADAC) snap-in (dsac.exe) to unlock users.
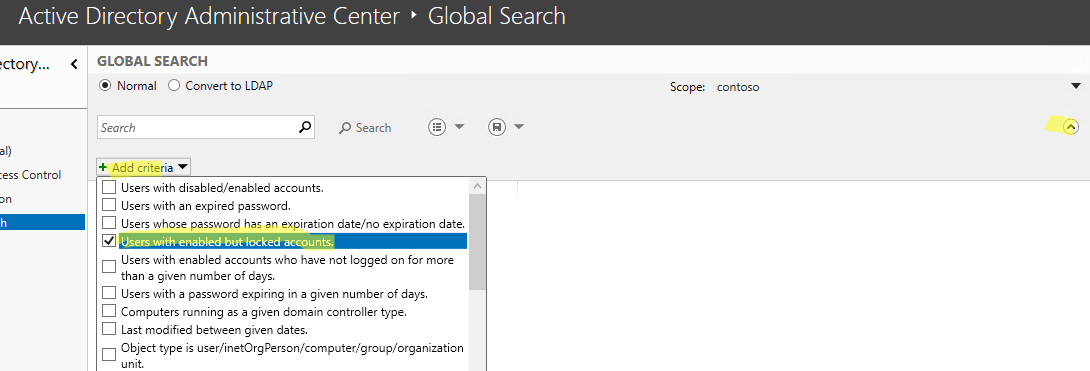
ADAC allows you to find all locked users in the domain:
- Click on an arrow button in the right top corner of console;
- Click Add criteria and select “Users with enabled but locked accounts”;
- Click Add and then Search;
- A list of all locked user accounts will appear in the console. You can select them all, open Properties, and unlock all users at once by clicking Unlock account.
How to Unlock Active Directory User Accounts with PowerShell
It is much faster to unlock Active Directory users by using PowerShell CLI. You can use the built-in PowerShell Active Directory module which is available on all of the domain controllers (or you can install the module on desktop Windows computers using the command: Get-WindowsCapability -Name Rsat.ActiveDirectory* -Online | Add-WindowsCapability -Online).
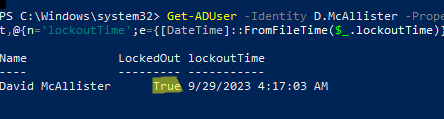
You can check if the user account is locked and display the lockout time:
Get-ADUser -Identity bjackson -Properties LockedOut,lockoutTime| Select-Object Name,LockedOut,@{n='lockoutTime';e={[DateTime]::FromFileTime($_.lockoutTime)}}
This user account is locked (Lockedout=True).
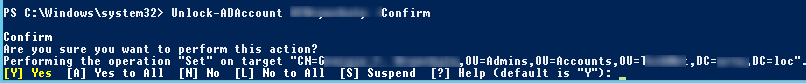
You can unlock an account by running:
Unlock-ADAccount bjackson –Confirm
Press Y to confirm the action > Enter.
You can also use the following syntax:
Get-ADUser -Identity bjackson | Unlock-ADAccount
Check if this account is now unlocked (Lockedout=True):
Get-ADUser -Identity bjackson -Properties LockedOut | Select-Object samaccountName,Lockedout
The user can now log on to the domain computer using his account.
You can list all locked user accounts in the domain:
Search-ADAccount -lockedout | Select-Object SamAccountName, LastLogonDate, Lockedout
Use the following PowerShell one-liner to unlock all users at once:
Search-ADAccount –UsersOnly -Lockedout | Unlock-AdAccount -Confirm
How to Delegate Unlock User Permission in Active Directory
By default, only members of the built-in ‘Domain Admins’ and ‘Account Operators’ groups can remove user account locks in Active Directory. You can delegate unlock user permission to non-admin users. To do this:
- Create a new allowUnlockAccount Active Directory security group in the domain;
- Open the ADUC console and right-click on the users’ OU;
- Select the item Delegate Control (learn more about how to delegate control in Active Directory);
- Click Add and select the allowUnlockAccount group. Click Next;
- Select Create a custom task to delegate > Only the following objects in the folder > User objects;
- Select Property-specific and check two permissions in the list: Read lockoutTime and Write lockoutTime;
- Save your changes.
Now members of the AllowUnlockAccount group can use the ADUC MMC snap-in or the Unlock-ADAccount PowerShell cmdlet to unlock user accounts from the target OU.
You can enable audit for accounts unlock events. To find out who has unlocked a specific user, you need to enable the Audit User Account Management policy for domain controllers (Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Account Management).
After updating the GPO, you can filter the Security Log by the Event ID 4767 (A user account was unlocked) to identify the user who unlocked the AD account.






1 comment
Love the Document, but there is a type under the heading “Account Lockout Policy” you incorrectly used the word “licking” instead of “locking”
Comments are closed.