In order to authenticate with Active Directory, you will need to provide your valid username and password. If the user has entered an incorrect password, an error message will be displayed on the Windows sign-in screen:
The user name or password is incorrect. Try again.
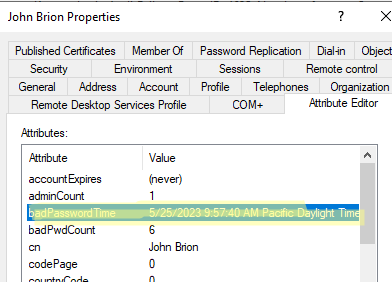
If the user has attempted to log in with an incorrect password, details of it are written to the badPasswordTime attribute in the user’s AD user properties. It also increments the badPwdCount attribute value by one.
If the badPwdCount value exceeds the threshold specified in the Account lockout threshold parameter of your Account Lockout Policy, the user account will be locked for a period of time.
Based on the lock event, you can keep track of the device from which the user account has been locked out (check the post to get the account lockout source in AD).
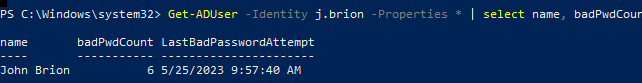
You can use the PowerShell command to get the current values of these AD user attributes:
Get-ADUser -Identity j.brion -Properties * | select name, badPwdCount, LastBadPasswordAttempt
However, if you haven’t configured a lockout policy, or if you’ve set a high lockout threshold value that is not reached, you won’t be able to find the source of bad password login attempts.
In this article, we will have a look at how to find out the computer name and IP address of the device from which the login attempts with a bad password are being made. This can help you quickly detect brute force attacks or resolve user account lockout issues.
To track failed authentication attempts with bad passwords, you must enable an audit policy on AD domain controllers.
- Open the Group Policy Management Console (gpmc.msc);
- Expand the Domain Controllers Organizational Unit and edit the Default Domain Controllers Policy;
- Go to the following Group Policy section: Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy > Logon/Logoff;
- Enable the Audit Logon policy. To only track bad password attempts in domain controller security logs, select Failure only;
- Force update the GPO settings with the command gpupdate /force (or wait for 5 minutes; this is the default policy refresh interval for Domain Controllers).
Now, if a user tries to log in with an incorrect password, an event with the Event ID 4625 will appear on the domain controller which they are trying to authenticate against (logonserver).
- Open the Event Viewer MMC snap-in (eventvwr.msc);
- Expand Windows Logs;
- Right-click on the Security and select Filter current log;
- Enter the code 4625 in the Event ID field;
- Only failed login events remain in the list of events;
- Open the latest event An account failed to log on.
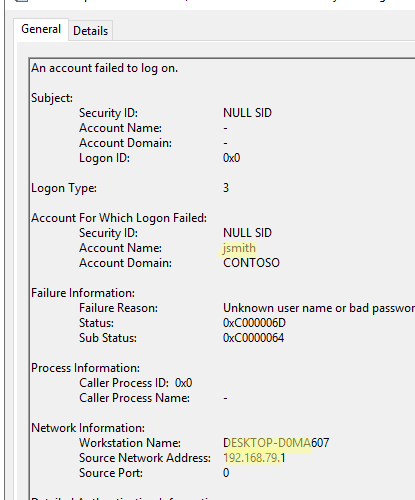
- The event description contains lots of useful information. It contains the name of the user who attempted to authenticate.
Account For Which Logon Failed:
Account Name: j.smith
And the reason for the login error:
Failure Reason: Unknown user name or bad password.
Now scroll down the event description. The name and IP of the computer from which the failed login attempt was made will be listed here:
Network Information:
Workstation Name: DESKTOP-D0MA607
Source Network Address: 192.168.79.1
Source Port: 0
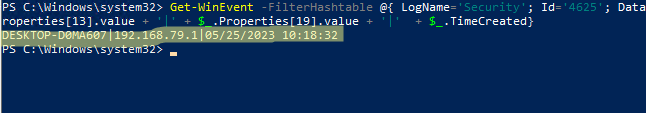
You can use PowerShell to display a list of computers (host name + IP address) that have attempted to log on with an incorrect password as the specified user.
$username="jsmith"
Get-WinEvent -FilterHashtable @{ LogName='Security'; Id='4625'; Data=$username } | foreach {$_.Properties[13].value + '|' + $_.Properties[19].value + '|' + $_.TimeCreated}
To query all domain controllers in AD and obtain information about the sources of bad password attempts, run:
$username="jsmith"
Get-ADDomainController -fi * | select -exp hostname | % {
$GweParams = @{
‘Computername’ = $_
‘LogName’ = ‘Security’
‘FilterXPath’ = "*[System[EventID=4625] and EventData[Data[@Name='TargetUserName']='$Username']]"
}
$Events = Get-WinEvent @GweParams
$Events | foreach {$_.Computer + " " +$_.Properties[13].value + '|' + $_.Properties[19].value + '|' + $_.TimeCreated}
}
That’s it. Hope this was useful to understand how to find bad password attempts in Active Directory.