One of the most critical tasks for administrators is to manage user access to resources, including remote desktop access. Controlling remote desktop access to servers contributes to a more secure environment.
By default, members of the built-in groups Remote Desktop Users and Administrators are allowed to access the remote desktop on workstations and servers. But for domain controllers, only the Administrators group has remote desktop access permissions.
In this blog post, we will discuss how to add Active Directory users to the remote desktop users group using Group Policy Object (GPO) and PowerShell.
Table of Contents
Create a Security Group for RDP Users
It is good practice to use group-based access whenever possible. This allows for easier user access management by adding or removing users from the appropriate group.
So instead of adding specific users to the Remote Desktop Users group, let’s first create a security group that will be added as a member. This way, you can create multiple groups if needed and organize user access more efficiently.
OPTION 1: Using the Active Directory Users and Computers Console
- Log in to the domain controller and open the Active Directory Users and Computers (ADUC) console.
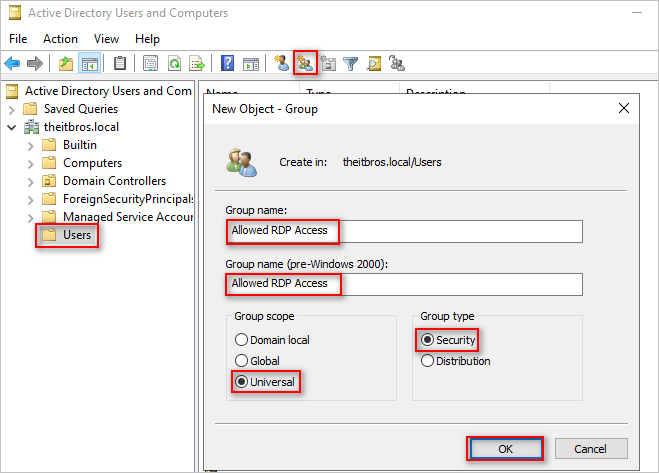
- Navigate to the Active Directory OU container where you want to create the new security group. In this example, we’ll select the Users OU.
- Click the New Group button.
- On the New Object > Group window, type the group name, select the group scope, select Security as the group type, and click OK.
- Once the security group is created, you can add the members (users and groups) to it. These members are the intended Remote Desktop Access users.
- After adding users and groups as members, click OK to save the changes and close the group properties window.
Option 2: Using PowerShell
To create the Allow RDP Users group using PowerShell:
- Log in to the server and open an elevated PowerShell session.
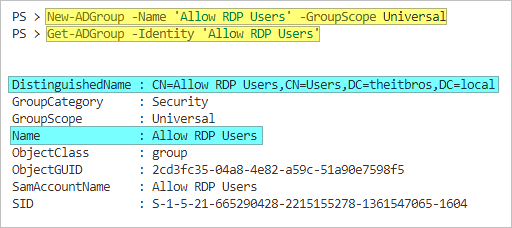
- Run the following command to create the security group. This command creates the security group named Allow RDP Users inside the Users OU:
New-ADGroup -Name 'Allow RDP Users' -GroupScope Universal Get-ADGroup -Identity 'Allow RDP Users'
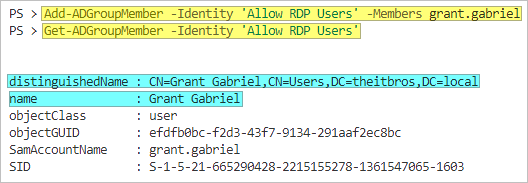
- Lastly, let’s add a user to the group:
Add-ADGroupMember -Identity 'Allow RDP Users' -Members grant.gabriel Get-ADGroupMember -Identity 'Allow RDP Users'
Add Users to the Remote Desktop Users Group using GPO
Group Policy Object (GPO) is a powerful tool that allows administrators to manage settings for multiple users and computers in an organization. One of the settings that can be controlled using GPO is the remote desktop users group membership.
We’ll configure the Remote Desktop Users policy item in this example using the GUI.
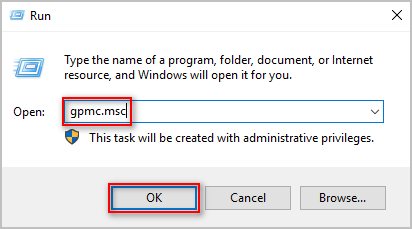
- Open the Group Policy Management Console (GPMC) on the domain controller.
gpmc.msc
- Right-click the domain and click Create a GPO in this domain, and Link it here.
Note. You can also create and link the new GPO in a specific OU.
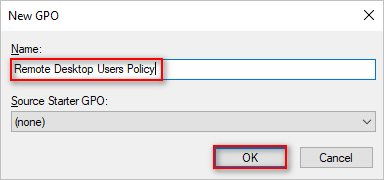
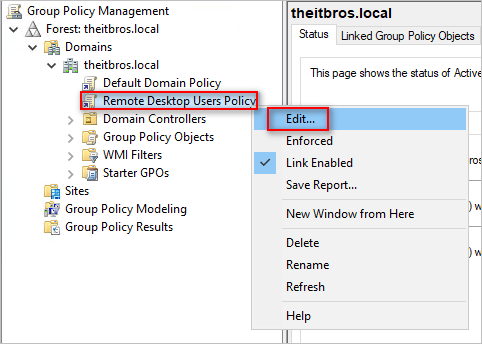
- Type Remote Desktop Users Policy as the policy name and click OK.
- Right-click the new policy and click Edit.
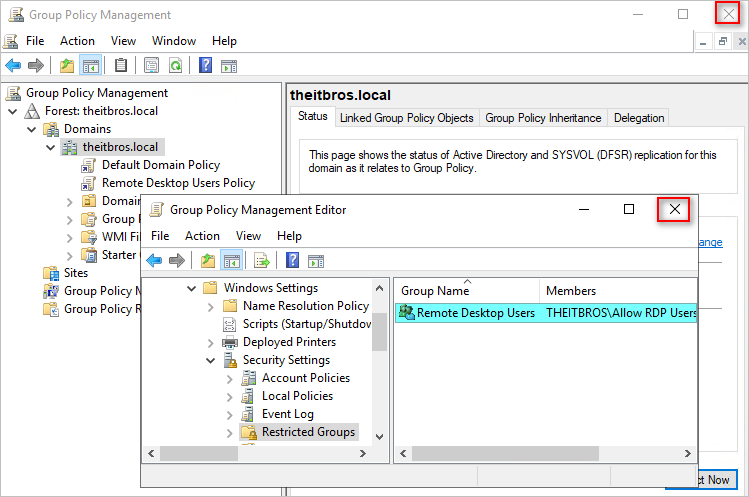
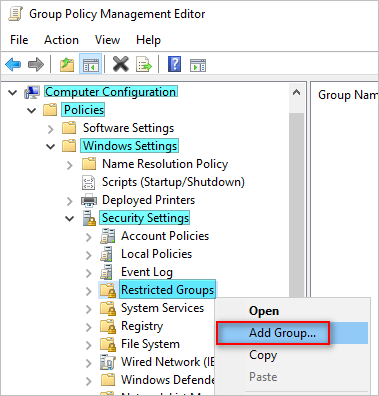
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings.
- Right-click on Restricted Groups and click Add Group.
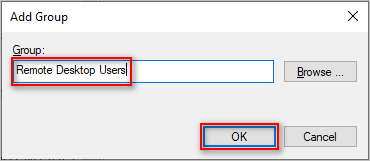
- On the Add Group dialog box, type Remote Desktop Users and click OK.
Note. Do not click Browse. You will not see the Remote Desktop Users in the Active Directory because it is a local group on each computer.
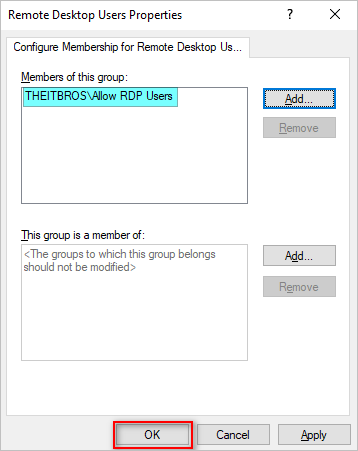
- The Remote Desktop Users Properties window opens. Under the Members of this group property, click Add.
- Browse for the security group you created earlier (Allow RDP Users) and save it as a member of the Remote Desktop Users group.
Note. You can also add domain users to the Remote Desktop Group.
- Click OK on the Remote Desktop Users Properties to save the changes.
- Close the Group Policy Editor and the Group Policy Management window.
- Finally, wait for the group policy replication throughout the domain. You can also force the group policy Remote Desktop Users by running gpupdate /force.
- Let’s check on one of the computers if the Allow RDP Users group is now a local Remote Desktop Users group member. In this example, we are entering a remote PowerShell session on PC1:
Enter-PSSession -ComputerName PC1
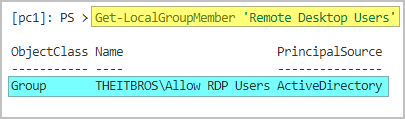
- Next, list the Remote Desktop Users group members on PC1 using the Get-LocalGroupMember cmdlet:
Get-LocalGroupMember -Group 'Remote Desktop Users'
That’s it! You’ve created the Remote Desktop Users group policy.
At this point, all Allow RDP Users security group members can RDP into the computers in the domain. If a user who isn’t a Remote Desktop Users group member tries to RDP, they will get a message like the one below.
So an administrator has to add the user as a member of the Remote Desktop Users through the Allow RDP Users security group.
Add Users to the Remote Desktop Users Group using PowerShell
You can also add users to Remote Desktop Users using PowerShell using the Add-LocalGroupMember cmdlet.
Note. A GPO configured for Remote Desktop Users will automatically overwrite the Remote Desktop Users’ group membership every time the computer updates the group policy. Only use this method if the RDP access is needed temporarily or if no GPO is configured for Remote Desktop Users.
Run the command below to add a user to the Remote Desktop Group locally on a computer.
Add-LocalGroupMember -Group 'Remote Desktop Users' -Member 'DOMAIN\USERNAME'
To add a user to the Remote Desktop Group locally on a remote computer, you can use PowerShell remoting with Enter-PSSession.
Enter-PSSession -ComputerName <remote_computer> Add-LocalGroupMember -Group 'Remote Desktop Users' -Member 'DOMAIN\USERNAME'
Or you can also run the Invoke-Command cmdlet to run the Add-LocalGroupMember command remotely.
Invoke-Command -ComputerName PC1 -ScriptBlock {
Add-LocalGroupMember -Group 'Remote Desktop Users' -Member 'DOMAIN\USERNAME'
}
Conclusion
Managing user access is an important task for system administrators, and adding Active Directory users to the remote desktop users group is just one aspect of this task. By using GPO and PowerShell, administrators can easily manage user access to remote desktops.
By following best practices and regularly reviewing access, administrators can ensure their environments are secure and only authorized users have access.





 Note. You can also add domain users to the Remote Desktop Group.
Note. You can also add domain users to the Remote Desktop Group.