DNS is a crucial component of network infrastructure and allows access to network resources, locally and across the Internet, using friendly names instead of IP addresses. There are many different DNS server solutions you can install.
This post will discuss setting up and configuring Unbound DNS, a robust and secure DNS server that can act as a local DNS server and a recursive DNS resolver. We will also cover the installation process, configuration, and essential aspects like DNSSEC validation and DNS over TLS.
Table of Contents
How does DNS work?
At the DNS system’s core are authoritative DNS servers and recursive DNS resolvers. Authoritative servers contain the definitive mapping of domain names to IP addresses, while recursive resolvers query these servers to obtain the required information. DNS queries, DNS messages, and responses are exchanged between the recursive resolver and the authoritative servers until the final IP address is resolved.
You can point clients to your own recursive DNS server or other DNS servers. Many will point to their own DNS server to resolve authoritative DNS server internal DNS zones that may be configured.
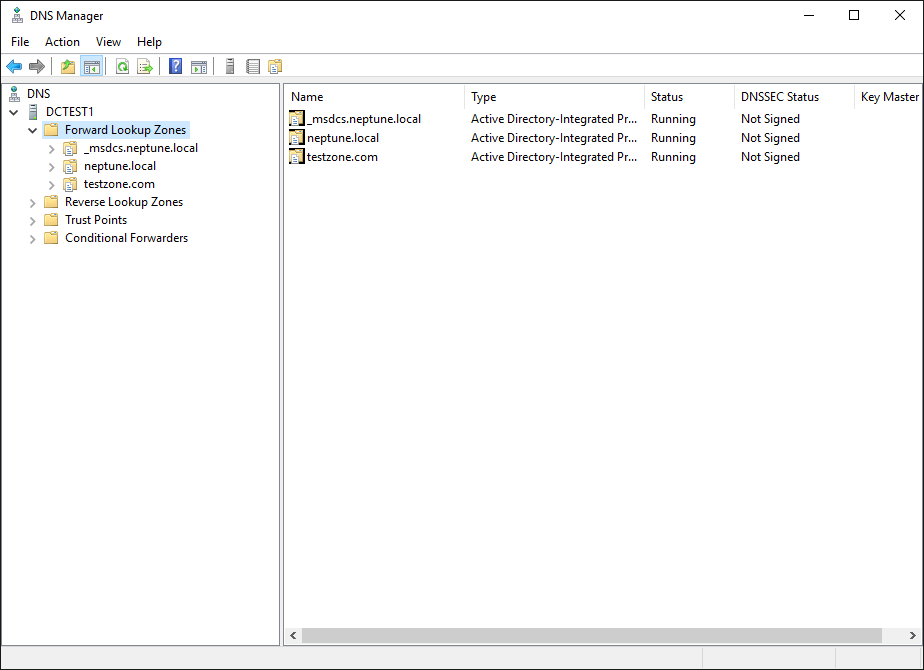
Windows DNS Server with local zones
Root servers
The next important idea to understand with DNS infrastructure is the root server. Root servers, also known as primary root servers, are upstream servers serving as the backbone of the Internet DNS system. They are responsible for providing the initial direction to locate the appropriate authoritative server for the requested domain. There are 13 root servers worldwide, operated by various organizations, and they play a vital role in the functioning of the global DNS system.
Below is an example of the root hints list on a Windows DNS Server. You can see this if you look at the properties of the DNS server and click the Root Hints tab.

Root hints servers on a Windows DNS server
Root servers play a vital role in DNS as they operate in the root zone, the starting point of all DNS lookups. These servers can respond directly to queries for records stored or cached within the root zone and guide other requests to the appropriate Top Level Domain (TLD) server. TLD servers, positioned just below root servers in the DNS hierarchy, are crucial in resolving DNS queries.
Imagine a user typing a web address into their browser. This simple act sets off a chain of events, initiating a DNS lookup that begins at the root zone. As the lookup journeys through the DNS system’s hierarchy, it first encounters the TLD servers and, subsequently, the servers for specific domains (and possibly subdomains) until it finally reaches the authoritative nameserver for the desired domain.
This server holds the numerical IP address of the website in question. This IP address is then returned to the user’s device. Remarkably, despite the numerous steps involved, this entire process unfolds at an impressive speed.
What is Unbound DNS Server?
Unbound is a validating, recursive, and caching DNS resolver developed by NLnet Labs. It is designed to be secure, fast, and flexible, offering DNSSEC validation by default. Following a rigorous audit in late 2019, Unbound’s code base has become more resilient than ever before.
With a commitment to enhancing online privacy, Unbound supports DNS-over-TLS and DNS-over-HTTPS, enabling clients to encrypt their communications. Moreover, it embraces various cutting-edge standards that minimize data exchange with authoritative servers, resulting in improved privacy and a more robust DNS. Key advancements include Query Name Minimisation, Aggressive Use of DNSSEC-Validated Cache, and support for authority zones, which facilitate loading a root zone copy.
DNSSEC validation
Looking more closely at DNSSEC, what is it exactly? DNSSEC (Domain Name System Security Extensions) is a set of extensions designed to add a layer of security to DNS, providing cryptographic signatures for DNS data. This ensures the authenticity and integrity of the DNS responses.
It also protects users from attacks like cache poisoning or man-in-the-middle attacks. Implementing DNSSEC validation in your local DNS server can significantly enhance the overall security of your DNS infrastructure.
How does Unbound work?
Unbound can be configured as a local DNS server or a recursive DNS resolver, improving your DNS infrastructure’s performance and security. You can also use it along with other security solutions like Pi-Hole.
Installing Unbound DNS using apt install
To install Unbound on a Debian-based system, simply run the following command:
sudo apt install unbound
This will install Unbound and its dependencies on your system. Once the installation is complete, you can proceed with the configuration.
Installing Unbound DNS using Docker
Let’s look at how to install Unbound DNS servers using Docker containers. You can use a simple Docker run command or Docker Compose code.
Using Docker run command
First, create a directory on the host machine to store Unbound configuration files and logs:
mkdir -p /path/to/unbound/config
Replace /path/to/unbound/config with the desired path on your host machine.
Next, run the Unbound container using the docker run command and mount the host directory to the container’s /opt/unbound/etc/unbound directory:
docker run -d --name unbound \ -v /path/to/unbound/config:/opt/unbound/etc/unbound \ -p 53:53/tcp -p 53:53/udp \ --restart=always \ mvance/unbound
Using Docker Compose
To install Unbound DNS using Docker Compose with a persistent volume mount, create a docker-compose.yml file in your project directory with the following content:
version: '3' services: unbound: image: mvance/unbound container_name: unbound volumes: - /path/to/unbound/config:/opt/unbound/etc/unbound ports: - "53:53/tcp" - "53:53/udp" restart: always
Replace /path/to/unbound/config with the desired path on your host machine.
Save the file, and then run the following command in your project directory:
docker-compose up -d
These examples demonstrate how to run Unbound DNS with a persistent volume mount using Docker run command and Docker Compose. This ensures that your Unbound configuration files and logs are stored on the host machine and persist even if the container is removed or recreated.
Validating our setup
After installing Unbound, it’s essential to validate that the server is running correctly and can resolve DNS queries. To do this, you can use the dig command as follows:
dig @localhost example.com
If the response contains an IP address for example.com, your Unbound server is functioning correctly.
Testing validation
To test DNSSEC validation, you can use the dig command with the +dnssec flag:
dig @localhost example.com +dnssec
If the response includes the “ad” flag, it indicates that Unbound has successfully validated the DNSSEC data.
Local DNS server
Unbound can be configured as a local DNS server, providing DNS resolution services to devices on your local network. This can improve the performance and security of your DNS infrastructure, as Unbound can cache DNS responses and perform DNSSEC validation.
Unbound configuration file
The main configuration file for Unbound is typically located at /etc/unbound/unbound.conf. This file contains various settings and options that control the behavior of the Unbound server. You can customize this file according to your requirements, such as specifying upstream DNS servers, enabling DNS over TLS, and setting access control rules.
Testing DNS lookup
After making changes to the Unbound configuration file, testing the DNS lookup functionality is essential to ensure everything works as expected. You can use the dig command to perform a DNS lookup:
dig @localhost example.com
If you receive a valid IP address in the response, your Unbound server is functioning correctly.
Testing DNSSEC
To test if your Unbound server is correctly performing DNSSEC validation, use the dig command with the +dnssec flag:
dig @localhost example.com +dnssec
If the response contains the “ad” flag, it indicates that Unbound has successfully validated the DNSSEC data for the queried domain.
Using openresolv
Openresolv is a tool that helps manage multiple DNS resolvers on a system. Integrating Unbound with openresolv allows you to automatically update the system’s DNS resolver configuration whenever Unbound starts or stops. To configure Unbound to work with openresolv, add the following lines to your Unbound configuration file:
include: /etc/resolvconf/run/resolv.conf resolvconf: yes
Forwarding using DNS over TLS
DNS over TLS (DoT) is a security feature that encrypts DNS queries and responses, protecting them from eavesdropping and tampering. To enable DNS over TLS forwarding in Unbound, add the following configuration to the /etc/unbound/unbound.conf file:
forward-zone: name: "." forward-tls-upstream: yes forward-addr: <Upstream DNS server with TLS support>
Replace <Upstream DNS server with TLS support> with the address of a DNS server that supports DNS over TLS, such as Cloudflare’s 1.1.1.1 or Google’s 8.8.8.8.
Manually specifying DNS servers
In some cases, you may want to manually specify the DNS servers that Unbound should use for resolving queries. You can do this by adding the following configuration to the /etc/unbound/unbound.conf file:
forward-zone: name: "." forward-addr: <DNS server 1> forward-addr: <DNS server 2>
Replace <DNS server 1> and <DNS server 2> with the IP addresses of the desired DNS servers.
DNS change in Drakconnect
Using Mandriva Linux with the Drakconnect tool, you can change the system’s DNS settings to Unbound by modifying the /etc/resolv.conf file. Replace the existing nameserver entries with the following line:
nameserver 127.0.0.1
This will configure the system to use the local Unbound server for DNS resolution once you have Unbound installed and configured on the local Mandriva Linux server.
Setting up unbound-control for remote control
Unbound-control is a command-line tool that allows you to remotely manage and monitor your Unbound server. On your unbound DNS server, this is installed automatically. However, you can also set up unbound-control to remotely manage your Unbound server follow these steps:
- Install the unbound-control package if it’s not already installed.
- Run sudo unbound-control-setup to generate the necessary SSL certificates and keys.
- Add the following configuration lines to the /etc/unbound/unbound.conf file:
remote-control: control-enable: yes control-interface: 127.0.0.1 control-port: 8953 server-key-file: "/etc/unbound/unbound_server.key" server-cert-file: "/etc/unbound/unbound_server.pem" control-key-file: "/etc/unbound/unbound_control.key" control-cert-file: "/etc/unbound/unbound_control.pem"
- Restart the Unbound server to apply the changes. Now you can use the unbound-control command to manage your Unbound server remotely.
Root hints systemd timer
Keeping the root hints file up-to-date is essential for ensuring the accuracy and efficiency of the DNS resolution process.
A systemd timer can automate this task by periodically updating the root hints file. To set up a systemd timer for updating the root hints, follow these steps:
- Create a script that downloads the latest root hints file:
```bash #!/bin/bash wget -O /etc/unbound/root.hints https://www.internic.net/domain/named.cache
- Save this script as /usr/local/bin/update-root-hints.sh and make it executable:
sudo chmod +x /usr/local/bin/update-root-hints.sh
- Create a systemd service file /etc/systemd/system/update-root-hints.service with the following content:
[Unit] Description=Update Unbound root hints [Service] Type=oneshot ExecStart=/usr/local/bin/update-root-hints.sh
- Create a systemd timer file /etc/systemd/system/update-root-hints.timer with the following content:
[Unit] Description=Timer for updating Unbound root hints [Timer] OnCalendar=monthly Persistent=true [Install] WantedBy=timers.target
- Enable and start the timer:
sudo systemctl enable --now update-root-hints.timer
- The root hints file will now be updated automatically monthly.
Using Unbound DNS Server in conjunction with Pi-Hole
Pi-Hole is a very popular solution to run in the home lab and the home network in general. It provides DNS sinkholing, allowing you to block DNS domains that serve ads, track information, and gather other telemetry data.
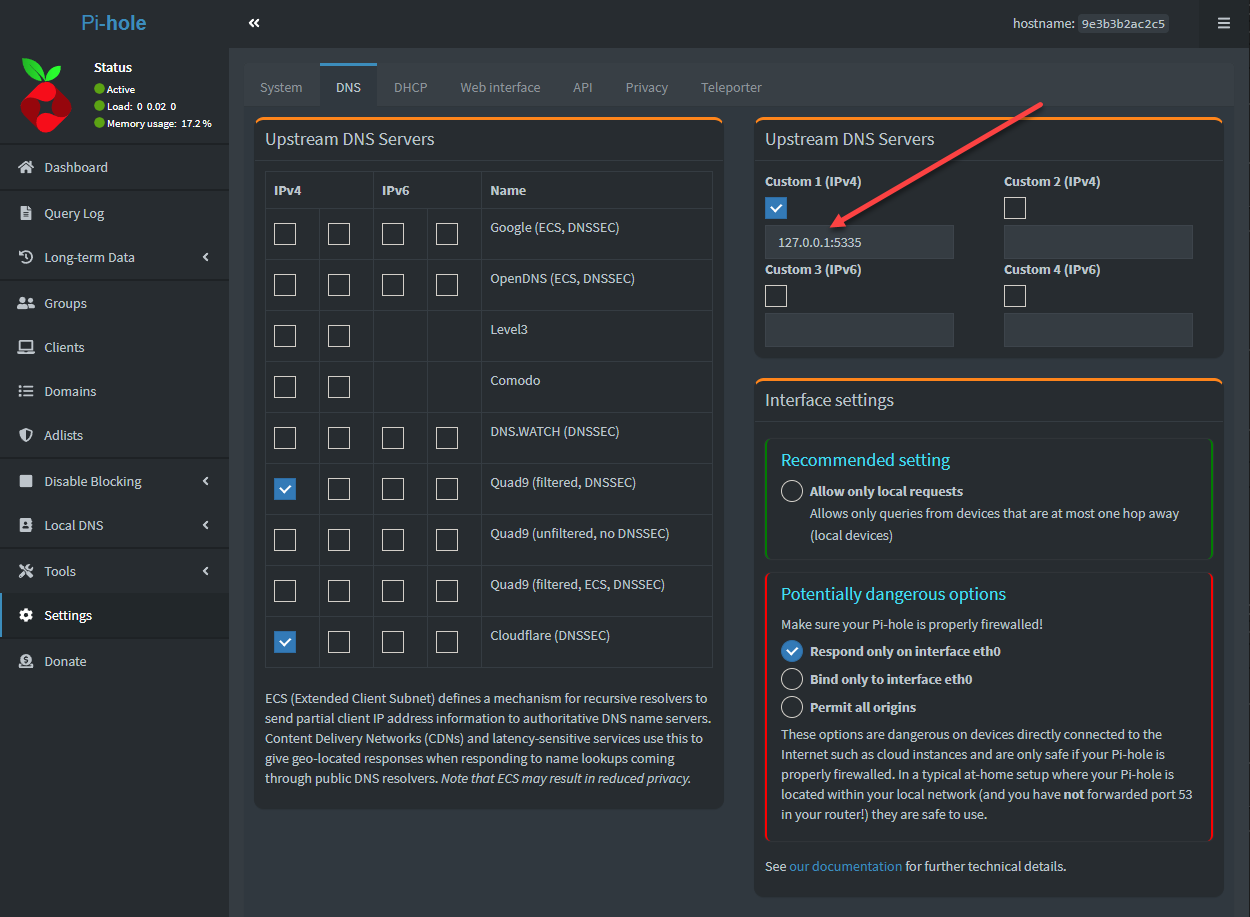
You can use Unbound as the upstream DNS server for Pi-Hole since Pi-Hole can’t do DNS over HTTPS natively. Both can be run on the same host by way of Docker containers. In your Pi-Hole configuration, you specify Unbound as your upstream DNS server.
Below is a Pi-Hole server pointed to a local Unbound DNS server.
Wrapping up
Unbound DNS is powerful and secure DNS server that can act as a local DNS server and a recursive DNS resolver. Following the steps outlined above, you can set up a secure and efficient DNS infrastructure that leverages DNSSEC validation and DNS over TLS to protect your network from potential threats. You can also use Unbound DNS Server in conjunction with other security solutions like Pi-Hole to further protect your environment. All-in-all, it is a great solution with many features and benefits.