There is no convenient way to find out if Multi-Factor Authentication is enabled for a particular user and what MFA methods are configured in the Microsoft 365 Admin Centre web interface. In this article, we’ll show you how to get the MFA status of Microsoft 365 users using PowerShell.
Previously, you could use the Get-MsolUser cmdlet from the MsOnline module or the Get-AzureADUser cmdlet from the AzureAD module to get the MFA status of Microsoft 365 users. However, after 30 June 2023, legacy Azure AD and MSOL modules (which use the Azure AD API) have been deprecated. So, now you must use the Microsoft Graph PowerShell module to get user MFA status in your Azure tenant.
Install the PowerShell module Microsoft Graph for all users on your computer:
Install-Module Microsoft.Graph -Scope AllUsers –force
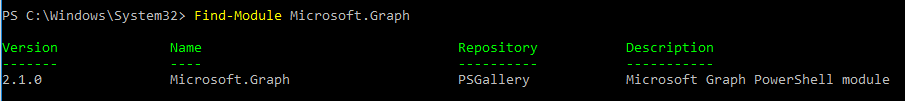
You can check if your computer has Microsoft Graph installed:
Find-Module Microsoft.Graph
Then connect to your tenant using the Microsoft Graph module:
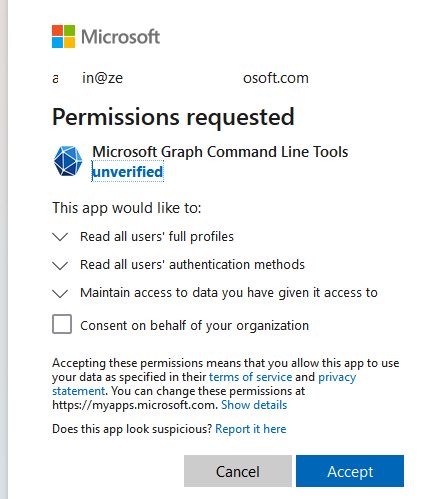
Connect-MgGraph -Scopes "User.Read.All,UserAuthenticationMethod.Read.All"
Authenticate and grant the Microsoft Graph command line tools permissions to read all Azure user properties and authentication methods.
If you’ve successfully authenticated to Azure via PowerShell, you should see the message “Welcome to Microsoft Graph!
Run the following command to get the MFA status for a single user:
Get-MGUserAuthenticationMethod -userid kirill@theitbros.onmicrosoft.com | fl
Hint. An error occurs if you have not granted access to UserAuthenticationMethod.Read scope:
Get-MgUserAuthenticationMethod_List1: Request Authorization failed
Only microsoft.graph.passwordAuthenticationMethod is enabled for the user in this example. This means that MFA is not configured.
If the user has any other MFA methods that are configured, the Get-MGUserAuthenticationMethod cmdlet lists them.
For example, my account is configured to authenticate using the Microsoft Authenticator app on a mobile device (#microsoft.graph.microsoftAuthenticatorAuthenticationMethod).
Other strong MFA authentication methods including biometrics, authenticator applications, hardware security keys, etc. can be configured for the user.
If multiple MFA methods are configured for a user, the command output can be difficult to understand which methods are enabled.
So you can use this simple PowerShell script to check the MFA status for a single user. The script checks whether any strong auth methods other than ‘Password Authentication’ are configured for the user.
$AzureUserUPN='adm2@theitbros.onmicrosoft.com'
$MFAUserData=Get-MgUserAuthenticationMethod -UserId $AzureUserUPN
$AzureUserObject = [PSCustomObject]@{
"User" = 'n/a'
"MFA status" = "Disabled"
"Email authentication" = "False"
"FIDO2 authentication" = "False"
"Microsoft Authenticator" = "False"
"Password authentication" = "False"
"Phone authentication" = "False"
"Software Oath" = "False"
"Temporary Access Pass" = "False"
"Windows Hello for Business" = "False"
"Passwordless Authenticator" = "False"
}
$AzureUserObject.user = $AzureUserUPN
foreach ($method in $MFAUserData) {
Switch ($method.AdditionalProperties["@odata.type"]) {
"#microsoft.graph.microsoftAuthenticatorAuthenticationMethod" {
$AzureUserObject."Microsoft Authenticator" = $true
$AzureUserObject."MFA status" = "Enabled"
}
"#microsoft.graph.emailAuthenticationMethod" {
$AzureUserObject."Email authentication" = $true
$AzureUserObject."MFA status" = "Enabled"
}
"#microsoft.graph.passwordAuthenticationMethod" {
$AzureUserObject."Password authentication" = $true
if ($AzureUserObject."MFA status" -ne "Enabled") {
$AzureUserObject."MFA status" = "Disabled"
}
}
"#microsoft.graph.fido2AuthenticationMethod" {
$AzureUserObject."FIDO2 authentication" = $true
$AzureUserObject."MFA status" = "Enabled"
}
"#microsoft.graph.phoneAuthenticationMethod" {
$AzureUserObject."Phone authentication" = $true
$AzureUserObject."MFA status" = "Enabled"
}
"#microsoft.graph.softwareOathAuthenticationMethod" {
$AzureUserObject."Software Oath" = $true
$AzureUserObject."MFA status" = "Enabled"
}
"#microsoft.graph.temporaryAccessPassAuthenticationMethod" {
$AzureUserObject."Temporary Access Pass" = $true
$AzureUserObject."MFA status" = "Enabled"
}
"#microsoft.graph.windowsHelloForBusinessAuthenticationMethod" {
$AzureUserObject."Windows Hello for Business" = $true
$AzureUserObject."MFA status" = "Enabled"
}
}
}
$AzureUserObject
The script will return MFA status: Disabled if the user is configured to use password authentication only.
If one or more strong auth methods are configured in addition to password authentication, this means that MFA is enabled for the user.





3 comments
Nice script, but the fact that we have to calculate and “guess” whether a user is actually required to use MFA is a typical oversight on Microsoft’s part. I have people who have their MFA status as “Disabled” in the O365 MFA settings, but come back as MFA Enabled using this script. And the O365 GUI unfortunately doesn’t allow you to filter by “Disabled”, only Enabled and Enforced. Typical half-baked half-ass Microsoft.
GUI is showing that MFA is disabled, but CLI and this script is showing that MFA is enabled. The user cannot user email using SMTP script , as user cannot login. MFA needs to be disabled.
The problem is that you can have all the auth methods in the world configured, but if you don’t enable / enforce it, it won’t require the user to use MFA and this script is assuming he does have it enabled by default.