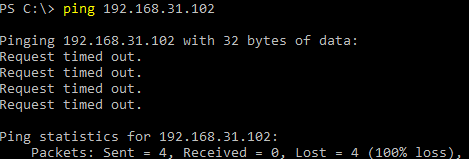
By default, the built-in Windows Defender Firewall blocks all inbound ICMP traffic. As a result, if you try to ping the Windows host from a different device, the computer will not respond to the ICMP echo request (with the Request timed out description). In this article, we’ll look at how to enable or disable host network connectivity checks (ICMP echo requests) using the ping command on Windows 10/11 and Windows Server 2022/2019/2016.
You can use the graphical MMC snap-in, the command line, and the PowerShell console to manage the rules of the Windows Firewall. Let’s look at all three ways of enabling and disabling ICMP rules in the firewall.
How to Allow Ping in Windows Firewall
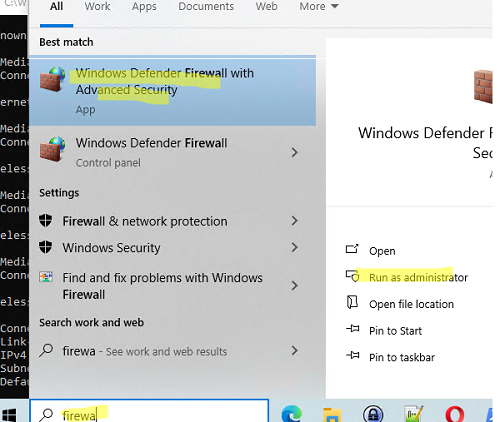
Search for Firewall in the quick search bar and open the Windows Defender Firewall with Advanced Security snap-in (or press Win+R and run the wf.msc command).
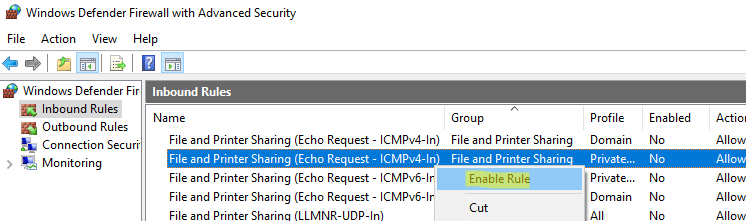
Select Inbound Rules in the left pane and find the File and Printer Sharing (Echo Request – ICMPv4-In) rule. As you can see, the rules for both ICMPv4 and ICMPv6 are available here for both the Domain and the Private network profiles. All of these rules are disabled by default.
You can turn on a firewall rule by right-clicking on it and selecting Enable Rule.
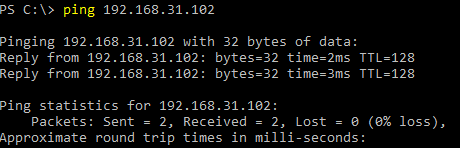
You can remotely check the availability of this computer using the ping command. Now Windows Firewall is not blocking ICMP requests and you can see that the remote host is accessible over the network.
By default, this rule allows ICMP echo requests from any source on the local network. If you want to restrict the list of computers that are allowed to send ICMP requests, or allow ICMP ping for external IP addresses, you can edit the existing rules.
- Open the properties of the firewall rule and go to the ‘Scopes’ tab;
- As you can see, the rule allows ICMP replies for all hosts on the Local subnet;
- You can edit the list of accepted IP addresses in Remote IP Address;
- This is where you can add specific IP addresses, ranges of IP addresses, or subnets.
You can enable and disable the Windows Defender firewall rule from the command line.. Open the elevated cmd prompt or PowerShell console. To allow ICMPv4 ping for all network profiles, run the command:
netsh advfirewall firewall set rule name="File and Printer Sharing (Echo Request - ICMPv4-In)" new enable=yes
You should see the following message:
Updated 2 rule(s).
Ok.
You must also enable the ICMP rule for the IPv6 protocol if it is used in your network communications:
netsh advfirewall firewall set rule name="File and Printer Sharing (Echo Request - ICMPv6-In)" new enable=yes
Separate cmdlets for managing Windows Firewall rules are available in the built-in NetSecurity PowerShell module. To allow ICMP ping for all profiles, run the following commands:
Enable-NetFirewallRule -displayName "File and Printer Sharing (Echo Request - ICMPv4-In)" Enable-NetFirewallRule -displayName "File and Printer Sharing (Echo Request - ICMPv6-In)"
Disable ICMP Ping in Windows Firewall
You can disable ICMP echo request rules from the Windows Defender Firewall graphical console. Select all the rules in the list (by holding down the CTLR key), right click and select Disable Rule.
It is also possible to disable the ICMP ping rules from the command prompt:
netsh advfirewall firewall set rule name="File and Printer Sharing (Echo Request - ICMPv4-In)" new enable=no netsh advfirewall firewall set rule name="File and Printer Sharing (Echo Request - ICMPv6-In)" new enable=no
Or with PowerShell:
Disable-NetFirewallRule -displayName "File and Printer Sharing (Echo Request - ICMPv4-In)" Disable-NetFirewallRule -displayName "File and Printer Sharing (Echo Request - ICMPv6-In)"