You can view and manage NTFS permissions on files and folders on the file system from the command line using the built-in iCACLS.exe tool. In this article, we’ll look at the example of using the iCACLS command to list, change, remove, backup and restore NTFS permissions on file system objects on Windows.
To manage the NTFS permissions on an individual file or folder, you can use the graphical Security tab in the file properties in File Explorer. When it comes to managing permissions on tens or hundreds of file system objects, administrators typically prefer to use command-line tools such as iCACLS.
Table of Contents
How to List File and Folder Permissions Using the iCACLS
To list the current NTDS permissions for a specific file and folder, simply open a command prompt and type the command:
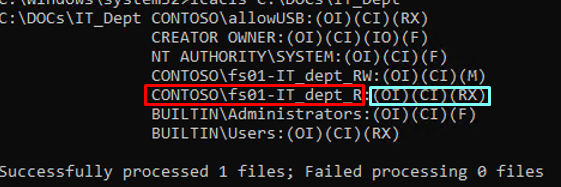
icacls C:\DOCs\IT_Dept
This command returns a list of all users and groups, and the individual permissions assigned to them. This is a Discretionary Access-Control List (DACL), which contains ACL (Access Control List).
Each line is a separate Access Control Entry (ACE) entry in the format:
Security principal : permission levels
Let’s try to understand the syntax of the permissions list returned by the iCACLS command:
CONTOSO\allowUSB:(OI)(CI)(RX) CREATOR OWNER:(OI)(CI)(IO)(F) NT AUTHORITY\SYSTEM:(OI)(CI)(F) CONTOSO\fs01-IT_dept_RW:(OI)(CI)(M) CONTOSO\fs01-IT_dept_R:(OI)(CI)(RX) BUILTIN\Administrators:(OI)(CI)(F) BUILTIN\Users:(OI)(CI)(RX)
Take a look at the following ACE entry: CONTOSO\fs01-IT_dept_R:(OI)(CI)(RX)
CONTOSO\fs01-IT_dept_R – This is the group (or user) to which permissions are assigned.
A list of assigned privileges for this security principal follows the colon (:). In this example:
- (OI) — object inherit;
- (CI) — container inherit;
- (RX) — Read and Execute access.
This means that the members of this group have the right to write and modify filesystem objects in this directory. All child (nested) objects in this directory inherit these NTFS permissions.
You can see what the same ACE entry looks like in File Explorer GUI:
- Open the file or folder properties;
- Navigate to the Permissions tab;
- Click Advanced;
- The Permissions entries contains the list of ACE records.
Below is a complete list of permissions that can be set using the icacls:
iCACLS inheritance settings:
- (OI) — objects inherit the specified ACE;
- (CI) — subdirectories in the current directory inherit ACE;
- (IO) — inherit only to the current object;
- (NP) — don’t propagate inherit;
- (I) — permission inherited from the parent container.
List of basic access permissions:
- D — delete access;
- F — full access;
- N — no access;
- M — modify (includes ‘delete’);
- RX — read and execute access;
- R — read-only access;
- W — write-only access.
Detailed permissions:
- DE — delete;
- RC — read control;
- WDAC — write DAC;
- WO — write owner;
- S — synchronize;
- AS — access system security;
- MA — the maximum allowed permissions;
- GR — generic read;
- GW — generic write;
- GE — generic execute;
- GA — generic all;
- RD — read data/list directory;
- WD — write data/add file;
- AD — append data/add subdirectory;
- REA — read extended attributes;
- WEA — write extended attributes;
- X — execute/traverse;
- DC — delete child;
- RA — read attributes;
- WA — write attributes.
You can view the syntax of the icacls command and some useful usage examples with the command:
icacls.exe /?
Set and Remove File Permissions with iCACLS
You can change the access lists for the file or folder using the icacls.
For example, you want to grant the user John the permissions to modify (M) the contents of the folder C:\PS:
icacls C:\PS /grant John:M
To grant Full Control (F) permission for the NYUsers domain group and apply all settings to the subfolders (/T, traverse subfolders — used to perform operation against all nested files and folders):
icacls "C:\PS" /grant domainname\NYUsers:F /Q /C /T
Grant a user read + execute + delete access permissions to the folder:
icacls E:\PS /grant John:(OI)(CI)(RX,D)
In order to grant read + execute (RX) and write (W) access and inherit down to subfolders and files (OI)(CI):
icacls E:\PS /grant John:(OI)(CI)(RX,W)
You can use the %username% environment variable to grant permissions to the currently logged on user:
ICACLS c:\PS /grant %username%:F
You can use the built-in group names in the icacls command. For example, Administrators, Everyone, Users, etc:
icacls C:\PS /grant Everyone:F /T
You can use the :r switch with /grant parameter to replace existing and inherited ACLs, rather than adding new ACLs to existing or inherited ACLs.
icacls C:\PS /grant:r Administrators:F
You can remove all the NTFS permissions assigned to John by using the /remove parameter:
icacls C:\PS /remove John
You can remove only the Granted or Denied permissions for a specific user or SID:
- /remove:g — remove all granted rights;
- /remove:d — remove all denied right.
iCACLS allows to assign explicitly deny access rights to certain security principals (rarely used). For example we’ll deny this group Modify (M) permissions (it includes: Create+Delete+Read+Write permissions) objects in the destination folder.
icacls c:\ps /deny "NYUsers:(CI)(M)"
Remember that prohibitive rules have a higher priority than allowing ones.
You can enable or disable permission inheritance on folder/file objects using the /inheritance option.
Three values are available for the /inheritance parameter:
- e — enable inheritance;
- d — disable inheritance and copy current ACE;
- r — remove all inherited ACEs.
To disable the inherited permissions and copy the current ACL (explicit permissions):
icacls c:\PS /inheritance:d
Disable inheritance and remove all inherited permissions, run:
icacls c:\PS /inheritance:r
To enable the inherited permissions on a file or folder object:
icacls c:\PS /inheritance:e
If you need to propagate new permissions to all files and subfolders in the target folder without using inheritance:
icacls "C:\PS\" /grant:r Everyone:(NP)(RX) /T
In this case, no specific permissions on subfolders will be overwritten.
The icacls allows you to manage not only NTFS permissions for file system objects on the local computer, but also permissions for remote shared folders.
To grant full access to the docs folder on the remote computer fssrv01, run the following command:
icacls \\fssrv01\docs /grant bjackson:F
You can also access local files on a remote computer through the administrative shares (C$, D$, etc.). This means that this command will work as well:
icacls \\fssrv01\d$\docs /grant bjackson:F
You may receive the “Access is denied” error when trying to change permissions on a file or folder using the icacls:
- Check that you are running at an elevated command prompt (as an administrator);
- Make sure you are allowed to change the permissions of this object (your account must have “Change permissions” assigned to the object).
Hint. The iCACLS doesn’t allow you to list effective NTFS permissions on a file system object. Use the Security tab in the File Explorer GUI to view the resulting permissions.
Quite a common problem: after copying directories between two drives, you can lose access permission to folders on a target drive. In this case, you can reset NTFS permissions.
The following command will reset all explicit and inherited permissions for all folders and files on drive E:
Icacls.exe E:\* /reset /T
If your version of Windows doesn’t support long paths, you won’t be able to change the permissions for an object if the full path to such an object is longer than 256 characters (with the Destination path too long error). In these cases, instead of using the following icacls command:
ICACLS C:\PS\LongFilePath /Q /C /T /reset
You should use:
ICACLS "\\?\C:\PS\LongFilePath " /Q /C /T /reset
ICACLS allows you to set a high integrity level for a file or folder. Only administrators can access and modify files and folders with a high level of integrity.
icacls C:\PS\myfile.txt /setintegritylevel H
The following entry will now appear in the file’s ACL:
Mandatory Label\High Mandatory Level:(NW)
After that, even if the user has Full Control access permissions to the file, he will not be able to change it and will receive an Access is denied error.
Note. In addition to the icacls tool, you can manage the NTFS permissions of file system objects using PowerShell.
Changing Ownership on File or Folder Using ICACLS
Using the icacls command, you can change the owner of a directory or folder. For example:
icacls c:\ps\secret.docx /setowner John /C /L /Q
- /Q — suppress success messages;
- /L — run the command against the symbolic link, instead of its target;
- /C — continue despite errors. Error messages will still be displayed;
You can change the owner of all the files in the directory (/T – recursively):
icacls c:\ps\* /setowner John /T /C /L /Q
You can also use icacls to reset the current permissions on file system objects:
icacls C:\ps /T /Q /C /RESET
The permissions of the target folder will be replaced with the permissions that are inherited from the parent object. This command is equivalent of the “Replace all child permission entries with inheritable permission from this object” in File Explorer.
You cannot change the owner of the object.
Note that the icacls command with the /setowner option doesn’t allow you to forcibly change the ownership of filesystem objects. If you are not the current object owner, use the takeown command to take file or folder ownership.
To find out all files with non-canonical ACLs or lengths that do not match the number of ACEs, use the /verify parameter.
icacls "c:\test" /verify /T
How to Backup and Restore NTFS ACLs Using ICACLS
The icacls command allows you to save the ACL of the current object to a plain text file. You can then apply the saved permission list to the same or other objects (a kind of way to backup ACLs).
Export the current ACL of the folder and save it in the *.TXT file:
icacls C:\PS\* /save c:\temp\PS_folder_ACLs.txt /T
This command saves ACLs not only for the directory itself but also for all subfolders and files. You can open the resulting text file using notepad or any text editor.
To apply saved ACLs to the folder (restore permissions), run the command:
icacls C:\PS /restore c:\temp\PS_folder_ACLs.txt /T /C /Q
This makes it much easier to copy ACLs from one folder to another (or between hosts).







1 comment
10000 times more helpful than the Microsoft documentation!!!!!