A proxy server can be invaluable for various purposes, from improving security and privacy to optimizing network performance. Squid is one of the most popular and versatile proxy servers available, and it’s open-source, making it an excellent choice for setting up your proxy server on Ubuntu. This step-by-step guide will walk you through setting up Squid Proxy Server on Ubuntu.
Table of Contents
Prerequisites
Before you begin, ensure you have the following:
- A machine running Ubuntu (this guide uses Ubuntu 22.04 LTS, but the steps are similar for other versions).
- Terminal access with sudo privileges.
- A basic understanding of Linux commands.
Installing Squid Proxy Server
First, ensure your package index is up to date by running the following command in your terminal:
sudo apt update
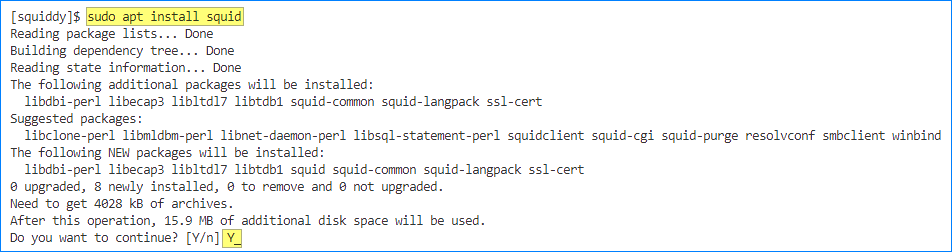
Now, let’s install the Squid proxy server. Run the following command:
sudo apt install squid
The system will prompt you to confirm the installation; type ‘Y’ and press Enter.
Once the installation is finished, confirm that the squid daemon is running.
sudo systemctl status squid
The result below shows that the Squid is enabled and running.
Configuring Squid Proxy Server
At this point, the Squid proxy server is running with default configurations. The configuration file for Squid is located at /etc/squid/squid.conf. You can customize various settings in the configuration file, including access control, allowed IP addresses, and ports.
You can open the Squid proxy server configuration file in a text editor like nano.
sudo nano **/etc/squid/squid.conf**
Note that changes to the configuration require restarting the Squid proxy server by running this command.
sudo systemctl restart squid
Changing the Listening Port
The Squid proxy server listens to port 3128 by default. Should you need to assign a different port number, here’s how to do it.
Open the Squid proxy server configuration file in a text editor like nano.
sudo nano **/etc/squid/squid.conf**
Locate this line:
http_port 3128
Modify the port number as needed. In this example, we’ll change it to port 8080.
Save the configuration file and restart the Squid proxy server.
sudo systemctl restart squid
Allowing Squid Through the Firewall
If a firewall is enabled on your Ubuntu server (e.g., UFW), allow traffic on the Squid proxy port.
If you did not change the Squid proxy server listening port, you can enable the Squid profile in UFW by running this command.
sudo ufw allow Squid
This command allows the following ports in UFW.
If you changed the default listening port, you must run this additional command to allow it. For example, this command allows the port 8080.
sudo ufw allow 8080/tcp
Confirm that the Squid firewall rules are enabled and allowed.
sudo ufw status numbered
After confirming the rules, reload the UFW rules.
sudo ufw reload
Testing Squid Proxy Server Connectivity
Test the Squid proxy server access by running this curl command. Replace the [PROXY_ADDRESS:PORT] and [URL] accordingly.
curl -x [PROXY_ADDRESS:PORT] -I [URL]
If the connection works via the Squid proxy server, you will get an HTTP 200 response like the one below.
Allowing Access to Specific IP Addresses
A typical security restriction with proxy servers is locking access to specific IP addresses or subnets. The default configuration allows only the localhost to access the web through the Squid web proxy.
To allow access to specific IP addresses (e.g., your local network), we’ll enable the localnet ACL. To do so, uncomment the find the “http_access allow localnet” line first.
Next, find the localnet ACL section, uncomment the existing entries, and a new ACL line for the subnet to allow.
Let’s break it down step by step:
- acl localnet src 10.0.0.0/24:
- This line creates an ACL named “localnet.”
- The src keyword indicates that this ACL is based on the source IP address of incoming requests.
- 10.0.0.0/24 is a subnet in CIDR notation, which specifies a range of IP addresses. In this case, it includes all IP addresses from 10.0.0.1 to 10.0.0.254. This is typically a local network range.
- http_access allow localnet:
- This line specifies an access control rule for the HTTP protocol.
- It uses the allow keyword to indicate that it allows access to resources.
- localnet is the name of the ACL defined earlier. This rule allows access to clients that match the IP addresses in the “localnet” ACL.
Save the configuration file and restart the Squid proxy server.
sudo systemctl restart squid
Testing the Squid Proxy Server IP-Based Access Restriction
Now, let’s test the Squid proxy access from a machine on another subnet.
In this example, the Squid proxy server IP address is 10.0.0.6/24, and the test machine is 10.0.1.4/24.
Run the curl command to test the proxy server access.
curl -x http://10.0.0.6:8080 -I https://theitbros.com
The result below shows an HTTP 403 Forbidden error. The “X-Squid-Error: ERR_ACCESS_DENIED 0” header also indicates that the connection from the test machine was denied by the Squid proxy server, which confirms that the localnet ACL works as expected.
Enabling Basic Authentication
You can also require authentication to the Squid proxy server as an additional layer of security. Squid supports several authentication methods, including Samba, LDAP, and HTTP basic authentication. In this example, let’s enable basic authentication.
Creating the Password File
First, you must create the /etc/squid/passwords file that will contain the USERNAME:PASSWORD pair.
sudo touch /etc/squid/passwords
Next, ensure that the proxy account owns the passwords file.
sudo chown proxy: /etc/squid/passwords
Creating a New Username and Password
Next, by running this command, let’s append a new username and password to the /etc/squid/passwords file. Replace proxyuser1 with the username you want to create.
sudo htpasswd -c /etc/squid/passwords proxyuser1
Note. If you received an error saying “htpasswd: command not found”, you must install the apache2-utils package by running:
sudo apt install apache2-utils
When prompted, type and re-type the new password.
Adding Basic Authentication
Let now enable the basic authentication directive in the Squid proxy configuration. Open the /etc/squid/squid.conf file in the text editor.
sudo nano /etc/squid/squid.conf
Insert the below code into the Squid proxy configuration file.
# Add basic authentication auth_param basic program /usr/lib/squid/basic_ncsa_auth /etc/squid/passwords auth_param basic children 5 auth_param basic realm Squid Basic Authentication auth_param basic credentialsttl 2 hours # Create new ACL auth_users # User must be authenticated acl basic_auth_users proxy_auth REQUIRED # Allow ACL auth_users http_access allow basic_auth_users
In this example, the basic authentication directive takes precedence over localnet ACL, which means even those devices within the subnet in the localnet ACL will be asked for authentication.
Here’s an explanation of each part of the configuration:
- auth_param basic program /usr/lib/squid/basic_ncsa_auth /etc/squid/passwords: This line specifies the program and location of a helper application that Squid will use for basic authentication. In this case, it’s using the basic_ncsa_auth program located at /usr/lib/squid/basic_ncsa_auth, and it expects to find user credentials in the file /etc/squid/passwords.
Note. The correct location of basic_ncsa_auth can be confirmed by running this command: dpkg -L squid | grep ncsa_auth. - auth_param basic children 5: This line sets the number of child processes Squid should spawn to handle basic authentication. In this case, it’s set to 5 child processes.
- auth_param basic realm Squid Basic Authentication: Here, a realm is defined for the basic authentication. The realm is essentially a description or label for the authentication realm, and in this case, it’s named “Squid Basic Authentication.”
- auth_param basic credentialsttl 2 hours: This line sets the time-to-live (TTL) for the cached authentication credentials to 2 hours. After 2 hours, users will need to re-authenticate.
- acl basic_auth_users proxy_auth REQUIRED: This line creates a new Access Control List (ACL) named basic_auth_users. It uses the proxy_auth tag, indicating that users must be authenticated to be part of this ACL. The REQUIRED keyword means that authentication is required for users to access resources through the proxy.
- http_access allow basic_auth_users: This line allows access to HTTP resources for users who belong to the basic_auth_users ACL. In other words, it grants access to authenticated users who have passed basic authentication.
Save the configuration file and restart the Squid proxy server service.
sudo systemctl restart squid
Testing the Squid Proxy Server Authentication
To test the basic authentication, let’s run the following commands. The first command uses the Squid proxy server but does not provide the basic authentication credentials.
# Without authentication curl -x http://10.0.0.6:8080 -I https://theitbros.com
The above command should fail with the HTTP 407 Proxy Authentication Required error.
Now, let’s provide the proxy credentials.
curl -x http://10.0.0.6:8080 -U USERNAME:PASSWORD-I https://theitbros.com
As a result, curl could authenticate, and an HTTP 200 Connection established code is returned.
Note. If you want to exclude IP addresses from basic authentication, move the ACL for that IP address (subnet) before the basic authentication directive.
Blocking Websites with Squid Proxy Server
Blocking specific websites can be an essential feature for many proxy server deployments. Squid provides powerful access control mechanisms that allow you to block websites. Here’s how you can block websites using Squid:
Creating a Blocked Website List
Create a new file called /etc/squid/blocked_websites.acl containing the blocked website list.
sudo touch /etc/squid/blocked_websites.acl sudo nano /etc/squid/blocked_websites.acl
Once the file is opened, enter the website domains to block. I’m adding three website domains in this example: .youtube.com, .reddit.com, and .twitter.com. Save the file and close the editor. You can add more sites to this file as needed.
Enable Website Blocking
Now, open the Squid proxy server configuration file for editing:
sudo nano /etc/squid/squid.conf
Then, insert these lines:
# Block websites from /etc/squid/blocked_websites.acl acl blocked_websites dstdomain "/etc/squid/blocked_websites.acl" http_access deny blocked_websites
Close the file and restart Squid:
sudo systemctl restart squid
Testing Squid Proxy Website Blocking
Now, test the Squid proxy server with a website that is not blocked to establish a baseline.
curl -x http://10.0.0.6:8080 -U PROXYUSERNAME:PASSWORD -I https://theitbros.com
As expected, you’ll see the HTTP 200 code because the site is not in the blocked website list.
Test the proxy server again with a blocked website, such as youtube.com.
curl -x http://10.0.0.6:8080 -U PROXYUSERNAME:PASSWORD -I https://youtube.com
You’ll get a HTTP 403 Forbidden code because youtube.com is blocked.
Conclusion
Setting up a Squid Proxy Server on Ubuntu can significantly enhance your network’s security and performance. Whether you’re using it for content filtering, caching, or privacy protection, Squid’s versatility and robustness make it a valuable tool.
Remember to regularly maintain and update your Squid configuration to adapt to changing requirements and security concerns. With this guide and some exploration of Squid’s capabilities, you can harness the power of a proxy server to improve your network’s efficiency and security.