The ADSI Edit tool (Active Directory Service Interface Editor) is a special MMC snap-in in Windows. It allows you to connect to Active Directory database partitions (NTDS.dit) or to the third-party LDAP server via Active Directory Service Interfaces. The ADSI Edit tool allows you to create, modify, and delete objects in Active Directory, edit attributes, perform searches, and so on.
Table of Contents
How to Install ADSIEdit on Windows
You can install the ADSIEdit.msc snap-in on Windows Server as well as on the desktop editions of Windows 10 and Windows 11.
To install ADSIEdit on Windows Server 2022/2019/2016:
- Open the Server Manager;
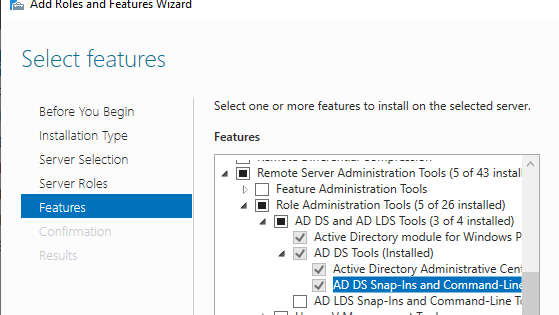
- Click Add roles and Features > Features > Remote Server Administration Tools > AD DS Tools > AD DS Tools > AD DS Snap-Ins and Command-Line Tools;
- Click Install.
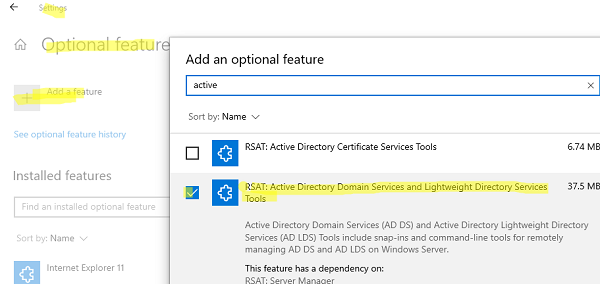
You can install the ADSI Edit Console on desktop OS versions (Windows 10 and Windows 11) via the GUI: Settings > Apps > Optional features > Add a feature > check RSAT: Active Directory Domain Services and Lightweight Directory Services Tools > Install.
You can also install RSAT ADDS tools using PowerShell:
Add-WindowsCapability –online –Name Rsat.ActiveDirectory.DS-LDS.Tools~~~~0.0.1.0
Now you can run ADSI Edit by using the adsiedit.msc command or from Control Panel\System and Security\Administrative Tools.
Managing Active Directory Using ADSIEdit
Important note. The ADSIEdit tool is a low-level tool for direct access to directory partitions. ADSI Edit allows you to make changes directly to the schema, configuration, and objects, bypassing some of the AD security mechanisms. This means that you could damage or destroy your Active Directory by making incorrect changes using adsiedit.msc. Before using this tool, it’s recommended to back up your Active Directory.
To get started with ADSI Edit, you need to connect to specific Distinguished Name or Naming context (also known as directory partition).
Right-click on the root in the ADSI Edit and select Connect to. Here you can choose which Connection Point, Naming Context, or remote computer with LDAP database you want to connect to.
There are four well known naming contexts are available;
- Default naming context — is the root of the current domain in which the domain controller you are accessing is located;
- Configuration — represent the logical structure of the AD forest, including the domain structure and the replication topology (forest-wide);
- Schema — contains definitions of objects that can be created in the AD forest and their available attributes (forest-wide);
- RootDSE — is the entry at the top of the LDAP server directory tree.
To use the encrypted LDAPS protocol to connect to the LDAP server or domain controller, check the Use SSL-based encryption option.
Select the Default naming context to connect to a directory partition containing user, Computer, group, computers, and OU objects. The ADSI Edit console will display all of the containers and Active Directory OUs in a hierarchical tree view (is similar to the AD view in the ADUC console). You can navigate in the AD hierarchy, select modify, move, delete, rename any AD object.
There is a list of available actions in the context menu of each AD object. For example, for the User object, in addition to the typical operations with an AD object (Move, New, Delete, Rename), you can reset the Active Directory user’s password. Also, note that the CN (Canonical Name) and Distinguished Name are displayed in ADSI Edit instead of the object name.
Open the object’s properties and go to the Attribute Editor tab to edit the object’s attributes. Here you can view or edit any object attribute value.
Info. This tab is identical to the Attribute Editor tab in ADUC console user properties.
Both filled and empty attributes are displayed (with the value <not set>). You can use the Filter button to customize the display options for object attributes.
- Show only attributes that have values — hide attributes with empty values;
- Show only writable attributes — show only attributes that the current user has permission to change (depending on the permissions delegated to the user account in Active Directory);
- Show mandatory attributes;
- Show optional attributes;
- Show read-only attributes (Constructed, Backlinks, or System-only).
To change the value of any attribute of an object, double-click on it, set a new value, and save the changes.
Note that object attributes can have different data types (Integer, String, MultiString, Time, etc). The values of the attributes containing the time/date are displayed in their normal form in the ADSI Attribute Editor console, but when you try to edit them, you will see that they are stored in the Active Directory database in Timestamp format.
ADSI Edit allows you to change AD settings that cannot be configured in any other way. For example, each domain user can join up to 10 computers to the domain. This is defined by the LDAP attribute ms-DS-MachineAccountQuota, which can only be edited via ADSI Edit (in the domain properties).
You can search for objects in AD using various criteria with the ADSI Edit Console:
- Right-click on the default naming context and select New > Query;
- Enter the query name, select the search root and specify the LDAP query code manually or generate it using the wizard (Query Edit button). In this example, we are looking for AD users named David:
(&(objectCategory=user)(objectClass=user)(givenName=david*))
- Save the query;
- The ADSI console will display a list of AD objects that match your LDAP query.
Next, we will look at examples of actions that can be performed using the ADSIEdit console.
Hide Specific OU in Active Directory with ADSI Edit
ADSI Edit allows you to hide specific OUs from the ADUC snap-in. Simply open the OU properties and change the showInAdvancedViewOnly attribute from False (or Not Set) to True.
Check the AD Schema Version Using ADSI Edit
- Select Schema as well-known Naming Context;
- Expand Schema, right-click CN=Schema,CN=Configuration,DC=theitbros,DC=com, and select Properties;
- Check the objectVersion value;
- In our case, it is 69. This number corresponds to the AD Schema version in Windows Server 2012 R2.
Adding Additional Columns to the ADUC Console
By default, only a specific list of attributes is displayed in the Active Directory Users and Computers console. A complete list of attributes that can be displayed in ADUC is available in the View > Add/Remove Columns menu. But there is no operatingSystem attribute in this list. You can add the operatingSystem attribute to the list of available columns in the ADUC console using ADSIEdit.
- Connect to Configuration Naming Context in ADSI Edit;
- Navigate to CN=DisplaySpecifiers > CN=409 and open the properties of the CN=organizationalUnit-Display object;
- Find the extraColumns property in the attribute editor and add the value: operatingSystem,Operating System,0,150,0
Hint. The following format is used used: <ldapDisplayName>,<Column Title>,<Displayed by default>,<Column Width>,<unused>
- Save the changes in ADSI, go to ADUC and check if the operatingSystem attribute is now displayed.
Manage AD Using ADSI Adapter for PowerShell
PowerShell allows you to connect to an LDAP AD using an ADSI adapter. This is not the easiest way to manage AD (features compared to the PowerShell Active Directory module), but sometimes you need to use it.
In order to retrieve information about an AD object via the ADSI interface, you need to specify the LDAP path to it:
[adsi]'LDAP://CN=M-DC02,OU=Domain Controllers,DC=contoso,DC=com'
List all object attributes:
[adsi]'LDAP://CN=M-DC02,OU=Domain Controllers,DC=contoso,DC=com' | Format-List *
You can get the value of a specific object attribute, for example, ms-DS-MachineAccountQuota (described above):
[adsi]"LDAP://DC=contoso,DC=com" | Format-List ms-DS-MachineAccountQuota
Use the ConvertLargeIntegerToInt64 function to convert the timestamp attribute value to normal date/time format:
$user = [adsi]"LDAP:// CN=Administrator,CN=Users,DC=contoso,DC=com"
[PSCustomObject] @{
name = $user.name.Value
pwdLastSet = [datetime]::FromFileTime($user.ConvertLargeIntegerToInt64($user.pwdLastSet.value))
}
You can use LDAP search filters to find objects in AD via ADSI. For example, we need to find all the domain controllers running Windows Server 2019 OS:
([adsisearcher]'(&(objectCategory=computer)(operatingSystem=Windows Server 2019*)(primaryGroupID=516))').FindAll()
Find users with “Password Never Expires” set:
([adsisearcher]'(&(objectCategory=person)(objectClass=user)(userAccountControl:1.2.840.113556.1.4.803:=66048))').FindAll()
List all disabled user accounts in AD:
([adsisearcher]'(&(objectCategory=person)(objectClass=user)(userAccountControl:1.2.840.113556.1.4.803:=2))').FindAll()
The ADSI interface also allows you to modify and create AD objects. For example, to create a new OU:
$TargetOU = [adsi]'LDAP://DC=contoso,DC=com'
$NewOU =$TargetOU.Create('organizationalUnit','ou=NewYork')
$NewOU.SetInfo()